Publications
The materials presented below are for academic use only. Copyright and all rights therein are retained by the authors or by the respective copyright holders.
# indicates the corresponding author.
[Books] [Conference papers] [Journal & Magazine papers] [Posters & Demos] [Patents]
Books
2023
- Posts & Telecom Press
 Cyberspace Mapping—Principles, Techniques and Applications网络空间测绘—原理、技术与应用Jiahai Yang, Lin He, Chenglong LiPosts & Telecom Press , 2023🏆 National Fund for Academic Publication in Science and Technology (NFAPST)Internet Measurement
Cyberspace Mapping—Principles, Techniques and Applications网络空间测绘—原理、技术与应用Jiahai Yang, Lin He, Chenglong LiPosts & Telecom Press , 2023🏆 National Fund for Academic Publication in Science and Technology (NFAPST)Internet Measurement@book{mapping, author = {Yang, Jiahai and He, Lin and Li, Chenglong}, title = {Cyberspace Mapping—Principles, Techniques and Applications}, publisher = {Posts & Telecom Press}, year = {2023}, chinesetitle = {网络空间测绘—原理、技术与应用}, }
Conference papers
2026
- INFOCOMDivide, Predict, Conquer: Adaptive Internet-wide Service Discovery with Limited SeedsDaguo Cheng, Zedong Jia, Ying Liu, Lin He#, Chao He, Jiuzhou Zhang, Chentian Wei, Jiasheng Zhou, Zhaoan Wang, Jinlong EIn Proceedings of the 45th IEEE Conference on Computer Communications (INFOCOM 2026)
Tokyo, Japan, May 18–21, 2026Internet Measurement@inproceedings{cheng2026divide, title = {Divide, Predict, Conquer: Adaptive Internet-wide Service Discovery with Limited Seeds}, author = {Cheng, Daguo and Jia, Zedong and Liu, Ying and He, Lin and He, Chao and Zhang, Jiuzhou and Wei, Chentian and Zhou, Jiasheng and Wang, Zhaoan and E, Jinlong}, booktitle = {Proceedings of the 45th IEEE Conference on Computer Communications (INFOCOM 2026)}, year = {2026}, pages = {1-10}, doi = {}, address = {Tokyo, Japan}, date = {May 18–21}, } - INFOCOMBreaking the Seed Barrier: Discovering Active IPv6 Addresses in Seedless ScenariosWenjian Zhang, Guanglei Song, Binkai Ma, Lin He, Songyun Wu, Hongxu Chen, Zhiliang Wang, Jiahai YangIn Proceedings of the 45th IEEE Conference on Computer Communications (INFOCOM 2026)
Tokyo, Japan, May 18–21, 2026IPv6 Internet Measurement@inproceedings{zhang2026breaking, title = {Breaking the Seed Barrier: Discovering Active IPv6 Addresses in Seedless Scenarios}, author = {Zhang, Wenjian and Song, Guanglei and Ma, Binkai and He, Lin and Wu, Songyun and Chen, Hongxu and Wang, Zhiliang and Yang, Jiahai}, booktitle = {Proceedings of the 45th IEEE Conference on Computer Communications (INFOCOM 2026)}, year = {2026}, pages = {1-10}, doi = {}, address = {Tokyo, Japan}, date = {May 18–21}, }
2025
- USENIX ATC
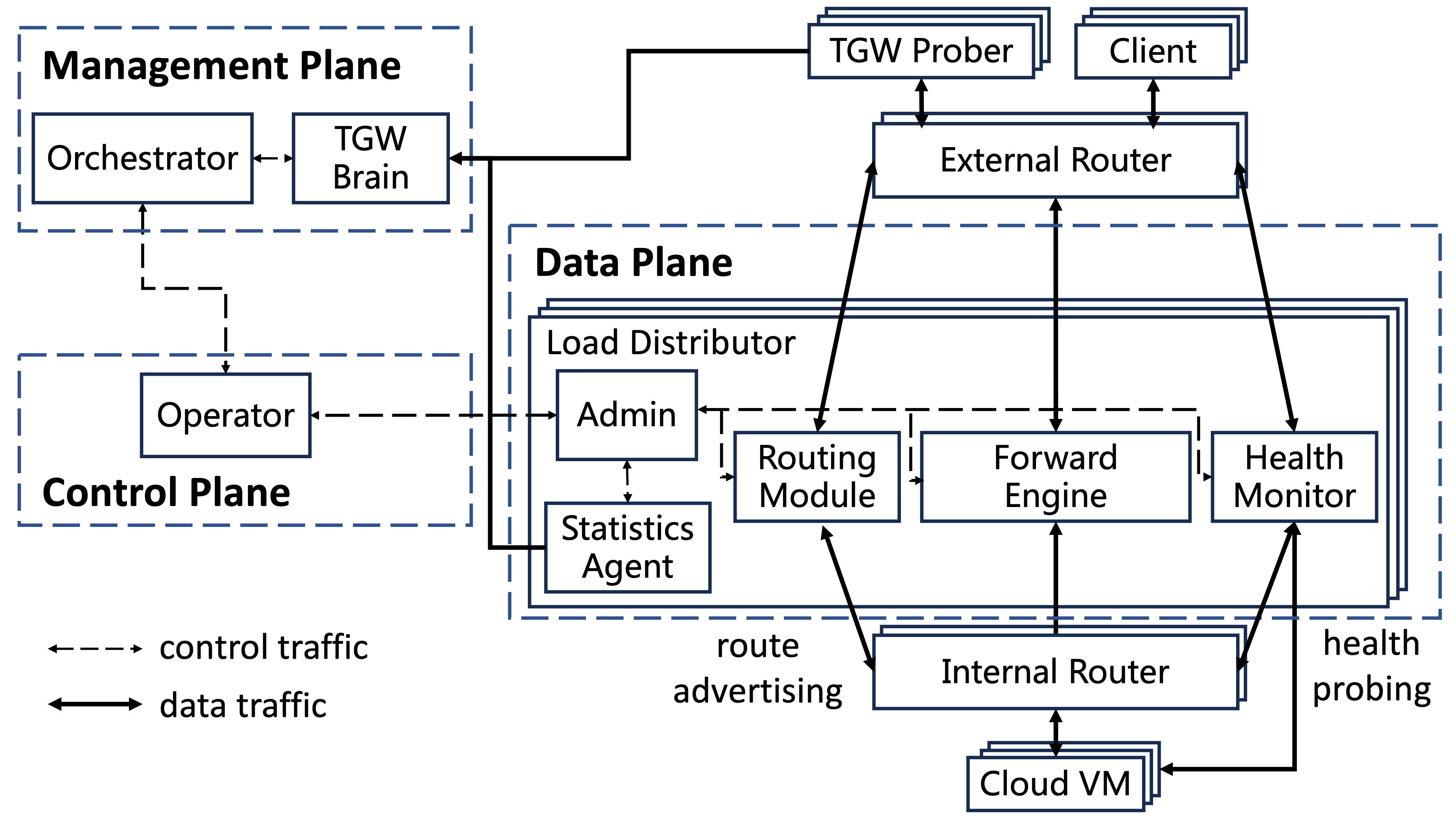 TGW: Operating an Efficient and Resilient Cloud Gateway at ScaleYifan Yang, Lin He#, Jiasheng Zhou, Xiaoyi Shi, Yichi Xu, Shicheng Wang, Jinlong E, Ying Liu, Junwei Zhang, Zhuang Yuan, Hengyang XuIn Proceedings of the 2025 USENIX Annual Technical Conference (USENIX ATC 2025)
TGW: Operating an Efficient and Resilient Cloud Gateway at ScaleYifan Yang, Lin He#, Jiasheng Zhou, Xiaoyi Shi, Yichi Xu, Shicheng Wang, Jinlong E, Ying Liu, Junwei Zhang, Zhuang Yuan, Hengyang XuIn Proceedings of the 2025 USENIX Annual Technical Conference (USENIX ATC 2025)
Boston, MA, USA, July 7–9, 2025Network ArchitectureLarge-scale cloud data centers have become a critical Internet infrastructure. As the cloud entrance, today’s cloud gateways have integrated multiple functions such as elastic public access and load balancing to cope with the rapid growth of services and requirements. To meet the demands of largescale clouds for efficient packet forwarding, scalable state management, and high resilience, we design, deploy, and operate Tencent Gateway (TGW), an efficient and resilient cloud gateway at scale. Compared to other large cloud providers that primarily offer services like search, e-commerce, or shortform video, the “killer services” of Tencent Cloud are online gaming and live streaming, which come with much stricter requirements for latency, jitter, and packet loss. From a technological perspective, TGW is highly decoupled and modular, with core components focused on efficient forwarding planes, a scalable state migration mechanism, a resilient failure recovery mechanism, and a failure detection and localization system. In terms of engineering, TGW has been operating in large-scale, real-world industrial environments for eight years, during which we have gained extensive insights and experience. We evaluate TGW both in testbed and real-world scenarios. In our testbed, TGW’s single node achieves 2.9× the forwarding capacity of prior systems. Between clusters, states and traffic can be migrated in 4 s without packet loss. In our real-world environment, TGW handles tens of Tbps of traffic, with a worst-case packet drop rate ranging from 10^−7 to 10^−4, while balancing traffic across clusters. Additionally, TGW can quickly migrate states and traffic and recover from failures without tenant awareness, guided by our failure localization system, achieving 100% availability for years.
@inproceedings{yang2025tgw, title = {TGW: Operating an Efficient and Resilient Cloud Gateway at Scale}, author = {Yang, Yifan and He, Lin and Zhou, Jiasheng and Shi, Xiaoyi and Xu, Yichi and Wang, Shicheng and E, Jinlong and Liu, Ying and Zhang, Junwei and Yuan, Zhuang and Xu, Hengyang}, booktitle = {Proceedings of the 2025 USENIX Annual Technical Conference (USENIX ATC 2025)}, year = {2025}, isbn = {978-1-939133-48-9}, address = {Boston, MA, USA}, date = {July 7–9}, pages = {199-215}, url = {https://www.usenix.org/conference/atc25/presentation/yang-yifan}, publisher = {USENIX Association}, } - Wisely Optimizing Short Video Streaming for a User-Vendor Win-Win OutcomeJinlong E, Wei Xu, Jianfei Bi, Lin He, Haoyang Li, Anqi Gu, Dan Yang, Yunpeng ChaiIn Proceedings of the 39th Annual Conference of the ACM Special Interest Group on Data Communication (SIGCOMM 2025): Short Paper
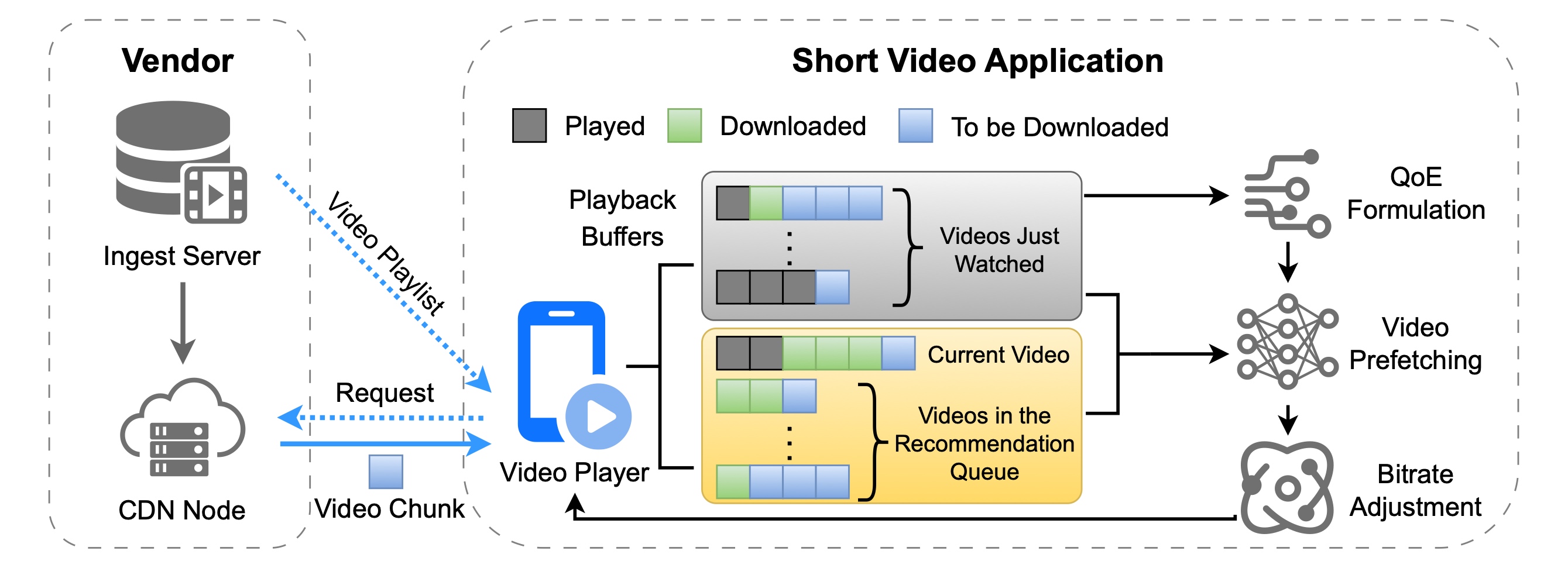
Coimbra, Portugal, September 8-11, 2025Network ArchitectureShort video streaming platforms widely employ video prefetching to ensure users’ quality of experience (QoE), but frequent user swipes lead to massive data wastage, creating a significant financial burden for vendors. Existing academic and industrial solutions fail to strike a balance, often sacrificing either data savings or the authentic user-perceived QoE. We introduce a framework that intelligently reduces streaming data consumption without compromising user experience. The core idea is to make prefetching decisions adaptive to both user swiping behavior and dynamic network conditions. This is mainly achieved through a novel user-perceived QoE metric, a fast-convergent hierarchical reinforcement learning (HRL) model for prefetching decisions, and a decoupled bitrate control policy. Real-world evaluations show our framework significantly outperforms the state-of-the-art solutions on data wastage as well as user-perceived QoE.
@inproceedings{e2025wisely, title = {Wisely Optimizing Short Video Streaming for a User-Vendor Win-Win Outcome}, author = {E, Jinlong and Xu, Wei and Bi, Jianfei and He, Lin and Li, Haoyang and Gu, Anqi and Yang, Dan and Chai, Yunpeng}, booktitle = {Proceedings of the 39th Annual Conference of the ACM Special Interest Group on Data Communication (SIGCOMM 2025): Short Paper}, year = {2025}, pages = {1272-1274}, doi = {10.1145/3718958.3754346}, address = {Coimbra, Portugal}, date = {September 8-11}, } - INFOCOM
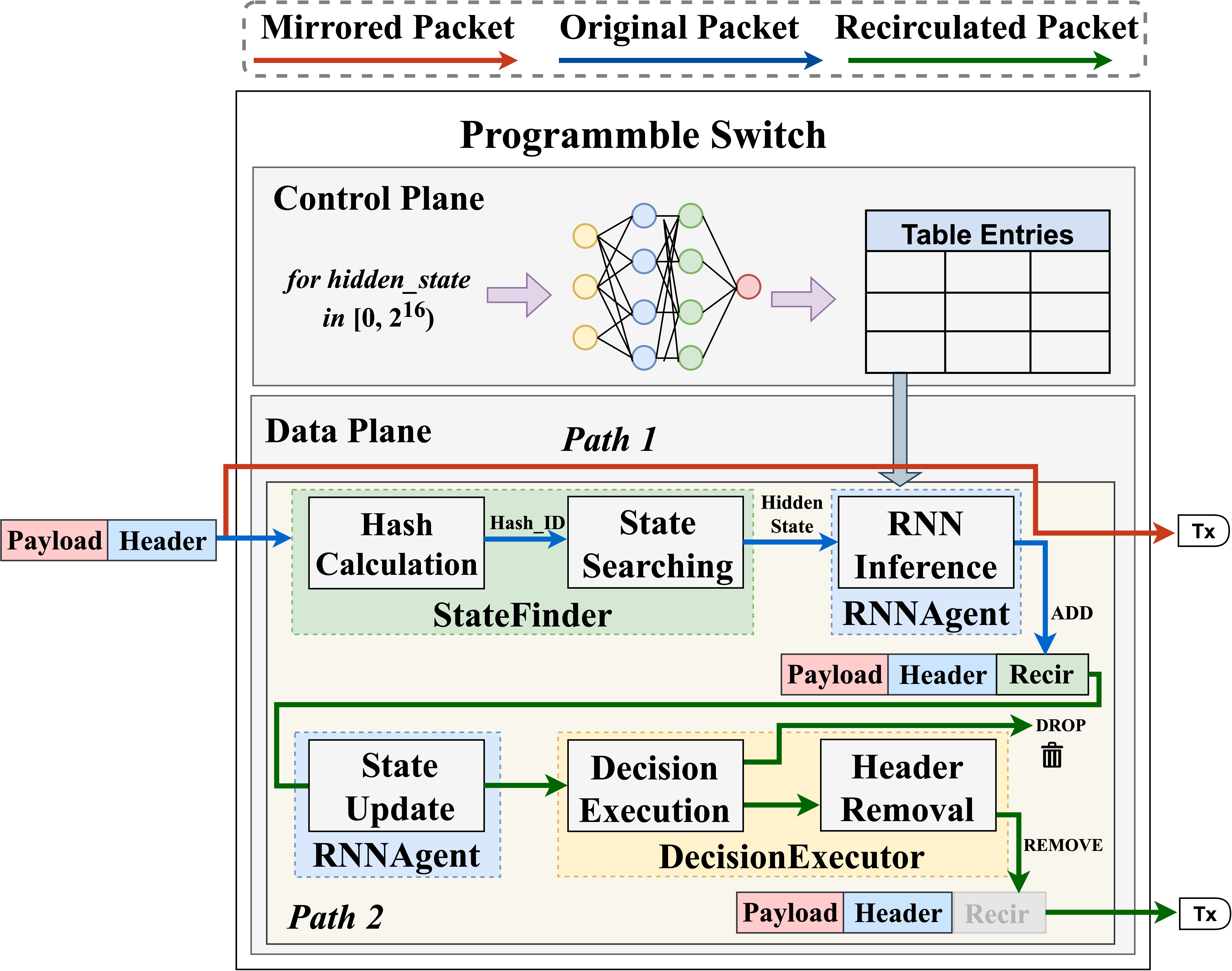
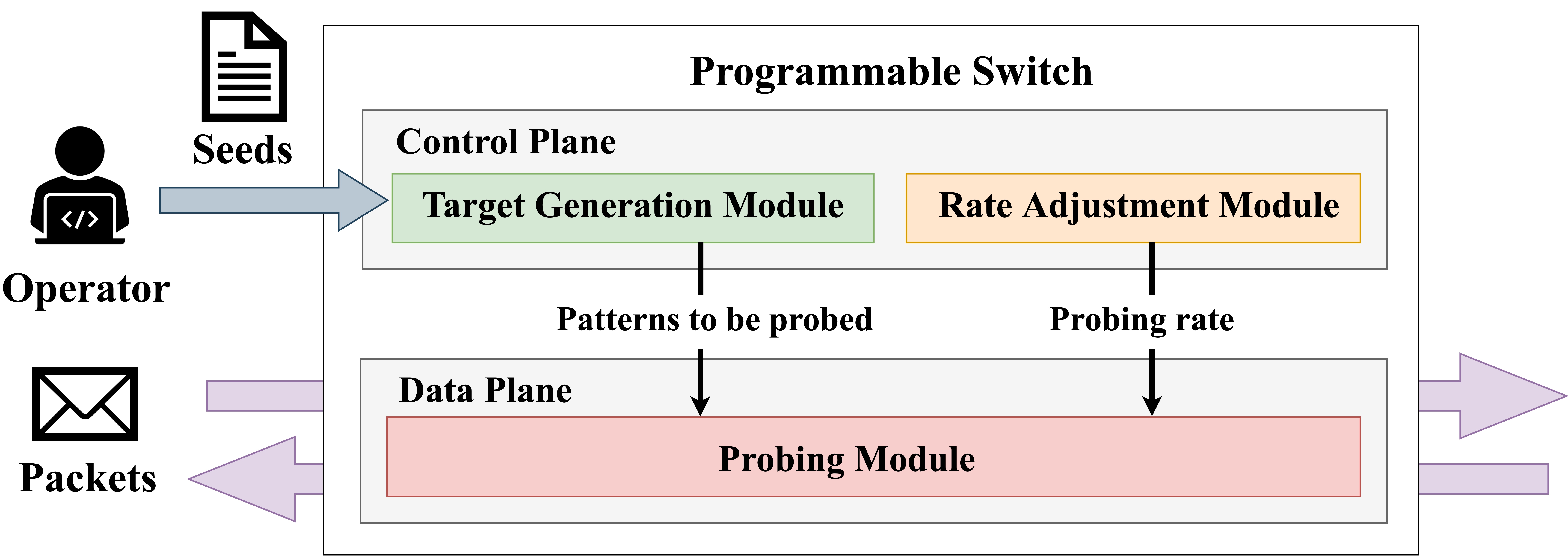 6Map: Enabling Fast Active IPv6 Address Discovery with Programmable SwitchesIn Proceedings of the 44th IEEE Conference on Computer Communications (INFOCOM 2025)
6Map: Enabling Fast Active IPv6 Address Discovery with Programmable SwitchesIn Proceedings of the 44th IEEE Conference on Computer Communications (INFOCOM 2025)
London, United Kingdom, May 19–22, 2025IPv6 Internet Measurement Programmable NetworksThe vast address space of IPv6 makes it impractical to apply exhaustive scanning to survey the entire network. Existing studies that aim to quickly discover active IPv6 addresses by optimizing the scanning space face issues of poor scalability and high time complexity, which hinder a comprehensive understanding of the IPv6 network and impede the timely provision of security snapshots and the development of IPv6. Fortunately, the emergence of programmable switches provides an opportunity to address the above issues. To this end, we propose 6Map, a fast active IPv6 address discovery system based on programmable switches. We design a lightweight target generation algorithm running on the control plane of the programmable switch and implement fast scanning address generation on the switch ASIC. The experimental results show that IPv6 active address discovery efficiency is up to 40.1× compared to the state-of-the-art method at the 100M probe budget.
@inproceedings{zhou20256map, title = {6Map: Enabling Fast Active IPv6 Address Discovery with Programmable Switches}, author = {Zhou, Jiasheng and He, Lin and Yang, Yifan and Shi, Xiaoyi and Cheng, Daguo and E, Jinlong and Liu, Ying and Zhang, Dong}, booktitle = {Proceedings of the 44th IEEE Conference on Computer Communications (INFOCOM 2025)}, year = {2025}, pages = {1-10}, doi = {10.1109/INFOCOM55648.2025.11044705}, address = {London, United Kingdom}, date = {May 19–22}, } - WWW
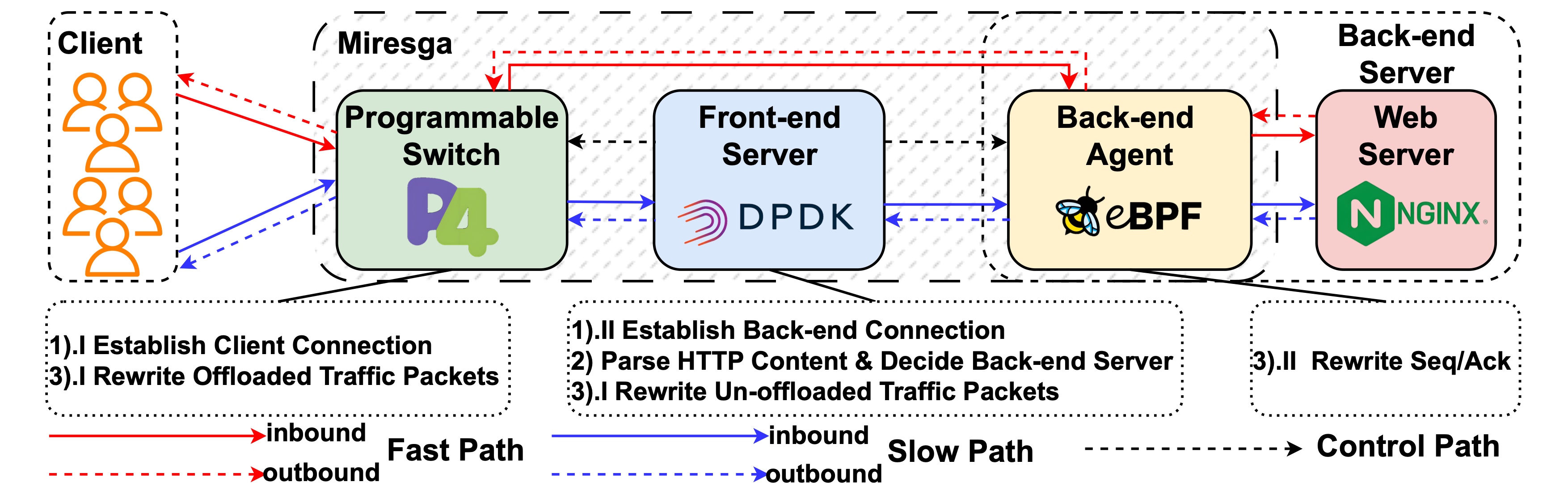 Miresga: Accelerating Layer-7 Load Balancing with Programmable SwitchesIn Proceedings of the 34th ACM Web Conference (WWW 2025)
Miresga: Accelerating Layer-7 Load Balancing with Programmable SwitchesIn Proceedings of the 34th ACM Web Conference (WWW 2025)
Sydney, Australia, April 28 – May 2, 2025Programmable NetworksAs online cloud services expand rapidly, layer-7 load balancing has become indispensable for maintaining service availability and performance. The emergence of programmable switches with both high performance and a certain degree of flexibility has made it possible to apply programmable switches to load balancing. Nevertheless, the meager memory capacity and the relatively sluggish speed of table entry insertion and deletion of programmable switches have severely constrained their performance. To this end, we introduce Miresga, a hybrid and high-performance layer-7 load balancing system by co-designing hardware and software. The core idea of Miresga is to maximize the utilization of hardware and software resources by rationally partitioning the layer-7 load balancing task, thereby improving performance. To achieve this, Miresga offloads the elephant flows, which account for the majority of traffic, to programmable switches that excel at packet processing, and Miresga utilizes general-purpose servers with stronger computational capabilities to parse application layer protocols and apply load balancing rules. To alleviate memory pressure on the programmable switch, Miresga employs a back-end agent to handle memory-intensive tasks, working in conjunction with the programmable switch to complete the offloaded tasks. This design leverages the performance advantages of the programmable switch while avoiding bottlenecks caused by its limited memory and table insertion speed. We implement the Miresga prototype with a 3.2 Tbps Intel Tofino switch and general-purpose servers. The evaluation results show that Miresga achieves 3.9x throughput and 0.4x latency compared to software load balancing solutions. Compared to state-of-the-art design employing programmable switches, Miresga achieves almost the same throughput and latency for delivering large objects and 5.0x throughput and 0.2x latency when transmitting small objects.
@inproceedings{shi2025miresga, title = {Miresga: Accelerating Layer-7 Load Balancing with Programmable Switches}, author = {Shi, Xiaoyi and He, Lin and Zhou, Jiasheng and Yang, Yifan and Liu, Ying}, booktitle = {Proceedings of the 34th ACM Web Conference (WWW 2025)}, year = {2025}, pages = {2424-2434}, doi = {10.1145/3696410.3714809}, address = {Sydney, Australia}, date = {April 28 – May 2}, } - WWW
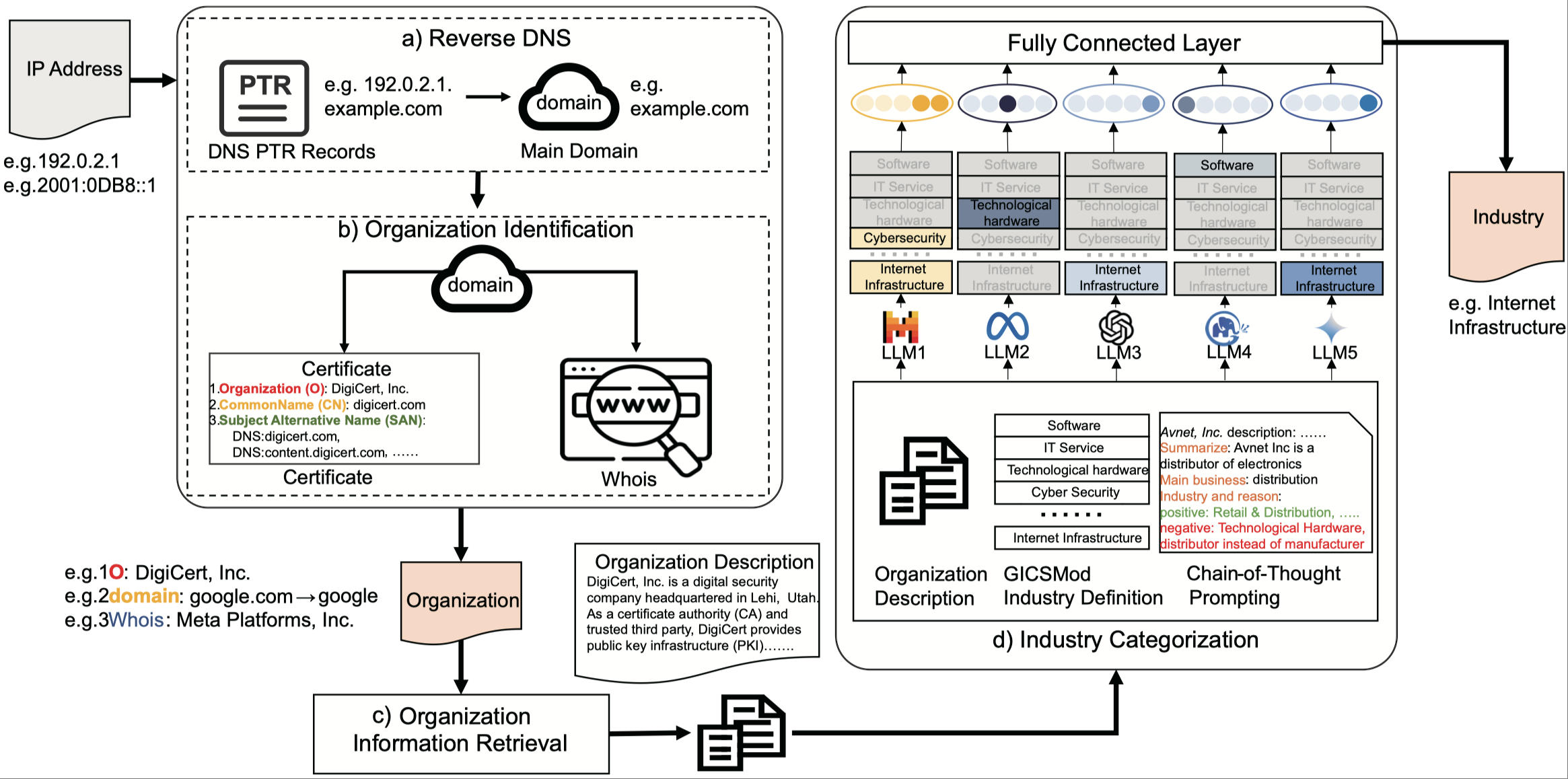 IPdb: A High-precision IP Level Industry Categorization of Web ServicesHongxu Chen, Guanglei Song, Zhiliang Wang, Jiahai Yang, Songyun Wu, Jinlei Lin, Lin He, Chenglong LiIn Proceedings of the 34th ACM Web Conference (WWW 2025)
IPdb: A High-precision IP Level Industry Categorization of Web ServicesHongxu Chen, Guanglei Song, Zhiliang Wang, Jiahai Yang, Songyun Wu, Jinlei Lin, Lin He, Chenglong LiIn Proceedings of the 34th ACM Web Conference (WWW 2025)
Sydney, Australia, April 28 – May 2, 2025Internet MeasurementIP addresses with web services are crucial in the Internet ecosystem. Classifying these addresses by industry and organization offers valuable insights into the entities utilizing them, enabling more efficient network management and enhanced security. Previous work in website classification and Internet management struggles to offer an IP-level perspective of the industries of web services due to their limited industry categories or potential industry inconsistencies between IP address owners and AS owners. To this end, we present IPdb, an IP-level industry categorization dataset. To construct the dataset, we developed LLMIC, a Large Language Model-based Industry Categorization framework with a precision of nearly 96%. IPdb serves as a labeled database for future endeavors in developing IP-level industry classifiers, encompassing over 200 million IP addresses. Furthermore, our study indicates that 30% 50% of organizations within critical infrastructure industries deploy web servers across multiple ASes. Our study also validates the problem of mismatched granularity in industry categorization at the AS level with 87.83% ASes in IPv4 and 72.96% ASes in IPv6 containing IP addresses from different industries.
@inproceedings{chen2025ipdb, title = {IPdb: A High-precision IP Level Industry Categorization of Web Services}, author = {Chen, Hongxu and Song, Guanglei and Wang, Zhiliang and Yang, Jiahai and Wu, Songyun and Lin, Jinlei and He, Lin and Li, Chenglong}, booktitle = {Proceedings of the 34th ACM Web Conference (WWW 2025)}, year = {2025}, pages = {4374-4385}, doi = {10.1145/3696410.3714669}, address = {Sydney, Australia}, date = {April 28 – May 2}, } - ICNP
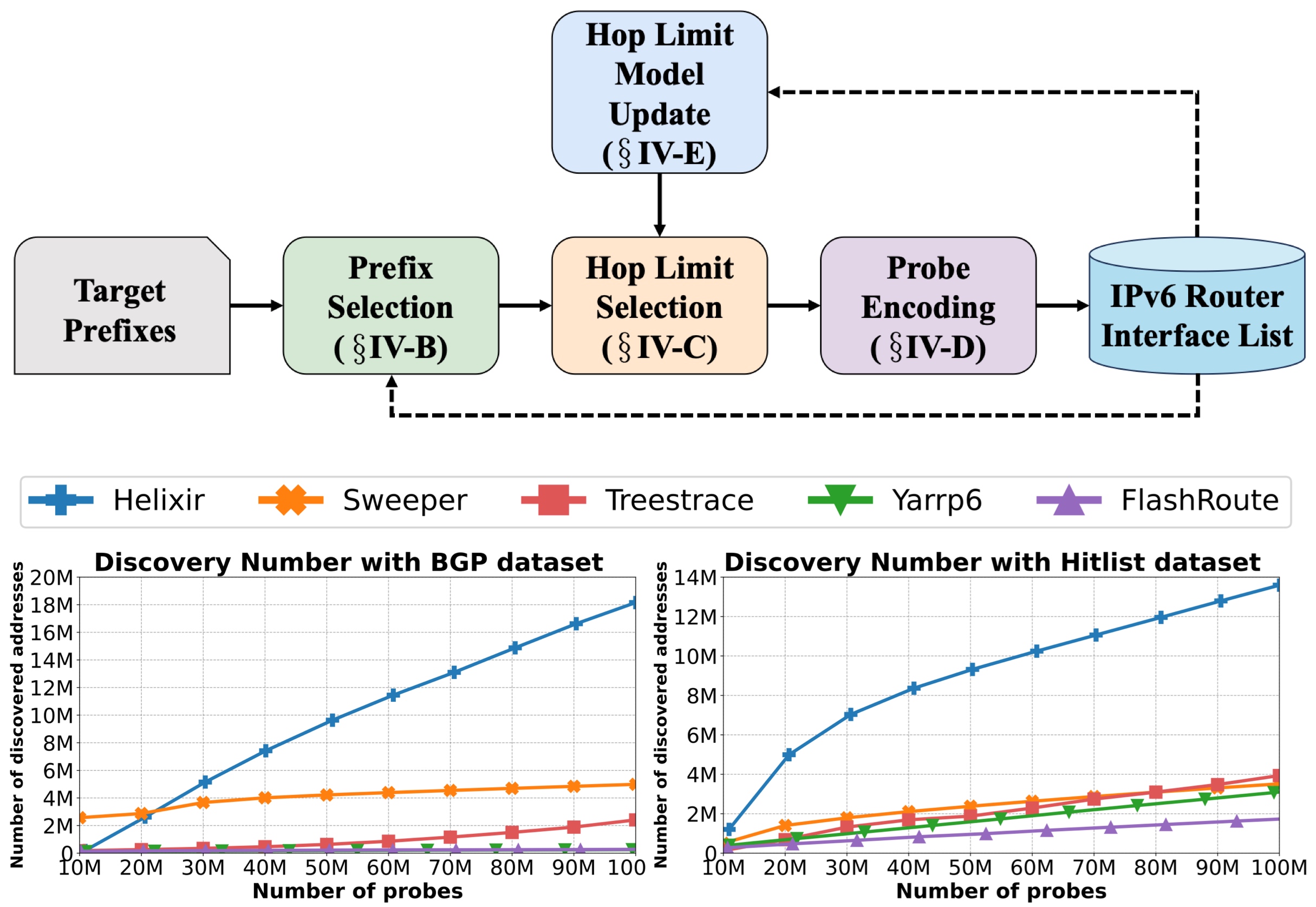 Lightning in the Dark: Uncovering Global IPv6 Router Interfaces and Their Security ImplicationsJiasheng Zhou, Ying Liu, Lin He#, Xiaoyi Shi, Yifan Yang, Chentian Wei, Daguo Cheng, Wenwen Gong, Jiahai YangIn Proceedings of the 33rd IEEE International Conference on Network Protocols (ICNP 2025)
Lightning in the Dark: Uncovering Global IPv6 Router Interfaces and Their Security ImplicationsJiasheng Zhou, Ying Liu, Lin He#, Xiaoyi Shi, Yifan Yang, Chentian Wei, Daguo Cheng, Wenwen Gong, Jiahai YangIn Proceedings of the 33rd IEEE International Conference on Network Protocols (ICNP 2025)
Seoul, South Korea, September 22-25, 2025IPv6 Internet MeasurementThe IPv6 routing infrastructure is an important part of the modern Internet, and the collection of its interface addresses is greatly significant in network security, performance optimization, and measurement analysis. However, existing methods suffer from two major problems: the lack of flexibility in budget allocation across probing rounds and the absence of a dynamic hop limit adjustment mechanism based on feedback. These problems lead to the low hit rate and inefficiency of existing methods for discovering router interfaces, which seriously hinders the comprehensive knowledge of IPv6 routing infrastructure. To this end, we propose Helixir, a feedback-based, high hit-rate, and efficient IPv6 router interface discovery system. Helixir’s core design includes a dynamic budget allocation mechanism across probing rounds, an inter-prefix budget allocation strategy that adequately trades off exploration and exploitation, and a hop limit selection method based on Thompson sampling. Real-world experiments show that with a 100M budget, Helixir achieves a hit rate 3.64× that of state-of-the-art methods on the BGP prefixes dataset, and Helixir successfully discovers over 31 million IPv6 router interface addresses in total within half an hour. In addition, a systematic security analysis of the discovered router interfaces shows that many devices open sensitive ports and expose hundreds of potential CVE vulnerabilities, highlighting the security risks in the IPv6 network.
@inproceedings{zhou2025lightning, title = {Lightning in the Dark: Uncovering Global IPv6 Router Interfaces and Their Security Implications}, author = {Zhou, Jiasheng and Liu, Ying and He, Lin and Shi, Xiaoyi and Yang, Yifan and Wei, Chentian and Cheng, Daguo and Gong, Wenwen and Yang, Jiahai}, booktitle = {Proceedings of the 33rd IEEE International Conference on Network Protocols (ICNP 2025)}, year = {2025}, pages = {1-14}, doi = {10.1109/ICNP65844.2025.11192454}, address = {Seoul, South Korea}, date = {September 22-25}, } - ICNP
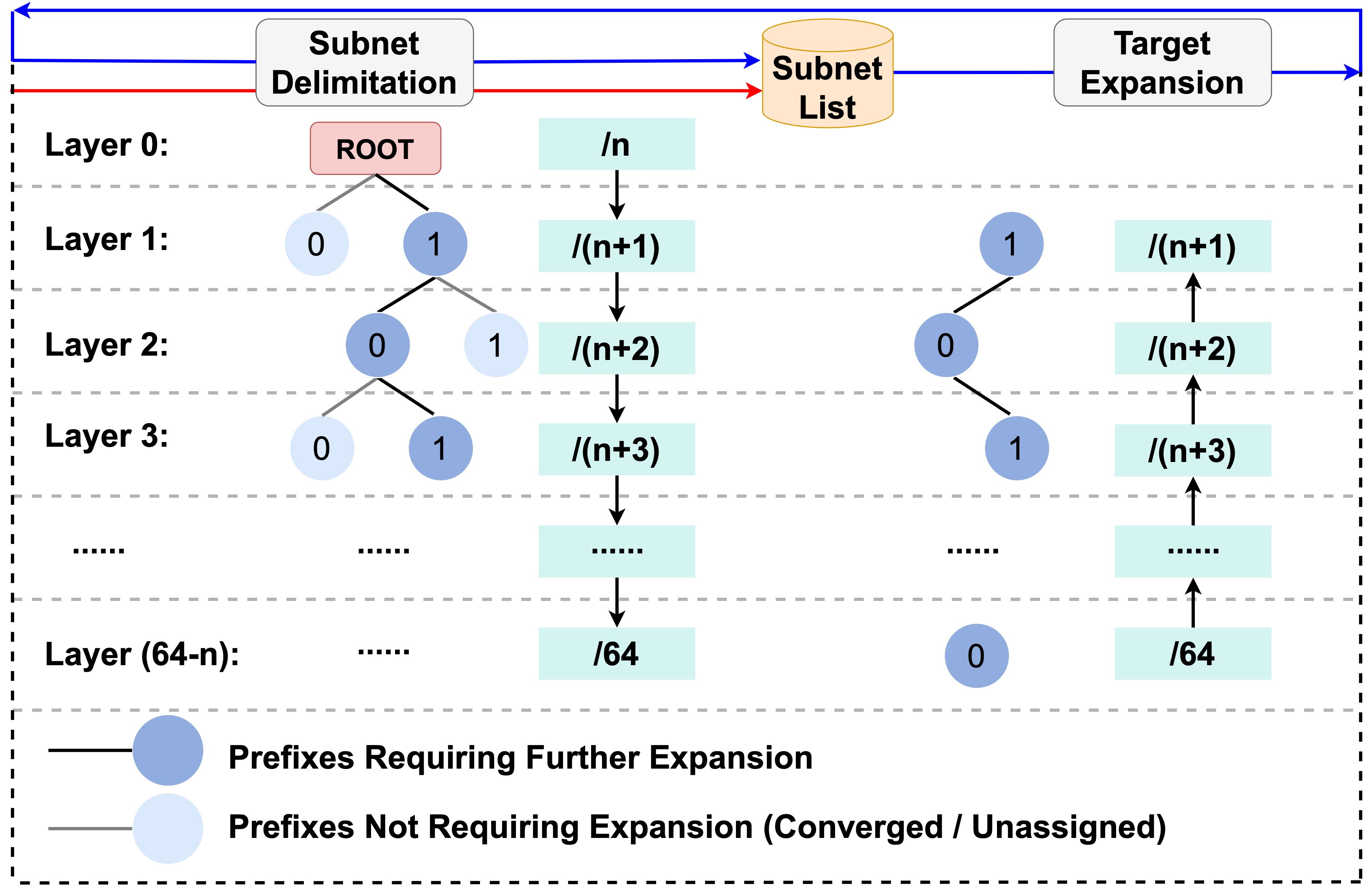 SubRecon: Efficient Internet‑wide IPv6 Subnet Discovery and Its ApplicationsJiasheng Zhou, Ying Liu, Lin He#, Yifan Yang, Xiaoyi Shi, Daguo Cheng, Chentian Wei, Yun Fan, Guanglei SongIn Proceedings of the 33rd IEEE International Conference on Network Protocols (ICNP 2025)
SubRecon: Efficient Internet‑wide IPv6 Subnet Discovery and Its ApplicationsJiasheng Zhou, Ying Liu, Lin He#, Yifan Yang, Xiaoyi Shi, Daguo Cheng, Chentian Wei, Yun Fan, Guanglei SongIn Proceedings of the 33rd IEEE International Conference on Network Protocols (ICNP 2025)
Seoul, South Korea, September 22-25, 2025IPv6 Internet MeasurementThe vastness of the IPv6 address space has led to the common practice of allocating prefixes to end users rather than individual addresses. Users can assign these prefixes as a single subnet or divide them into multiple subnets for different purposes. Allocation strategies vary significantly in terms of prefix granularity, and identifying the actual granularity of subnet assignments is crucial for improving measurement efficiency, accuracy, and for better IPv6 network management. However, no existing method can discover IPv6 subnets at an Internet-wide scale. To this end, we propose SubRecon, an Internet-wide IPv6 subnet discovery system. SubRecon consists of two key phases: subnet delimitation and target expansion. In the subnet delimitation phase, we perform a systematic scan across the entire IPv6 address space without relying on any existing seed dataset. This phase adopts a top-down approach, probing prefixes from the shortest to the longest in a hierarchical manner. At each level, we recursively refine prefixes and discard sub-prefixes that do not meet the convergence condition. This pruning strategy eliminates redundant probes in unallocated regions, significantly reducing the search space and improving probing efficiency. To further improve coverage, the target expansion phase leverages the active address dataset as an auxiliary input. It identifies active addresses not covered by previously discovered subnets, expands them into new candidate target prefixes, and performs another round of subnet delimitation. This helps enhance the completeness and coverage of the final discovered subnet set. Experimental results show that SubRecon discovers 8,381,974 IPv6 subnets across 14,147 Autonomous Systems (ASes), and the resulting subnet list can serve as high-quality input for topology discovery. Additionally, during the subnet discovery process, SubRecon identifies a large number of last-hop router interfaces, discovering approximately 10 million more than the current state-of-the-art methods.
@inproceedings{zhou2025subrecon, title = {SubRecon: Efficient Internet‑wide IPv6 Subnet Discovery and Its Applications}, author = {Zhou, Jiasheng and Liu, Ying and He, Lin and Yang, Yifan and Shi, Xiaoyi and Cheng, Daguo and Wei, Chentian and Fan, Yun and Song, Guanglei}, booktitle = {Proceedings of the 33rd IEEE International Conference on Network Protocols (ICNP 2025)}, year = {2025}, pages = {1-12}, doi = {10.1109/ICNP65844.2025.11192387}, address = {Seoul, South Korea}, date = {September 22-25}, } - ICNP
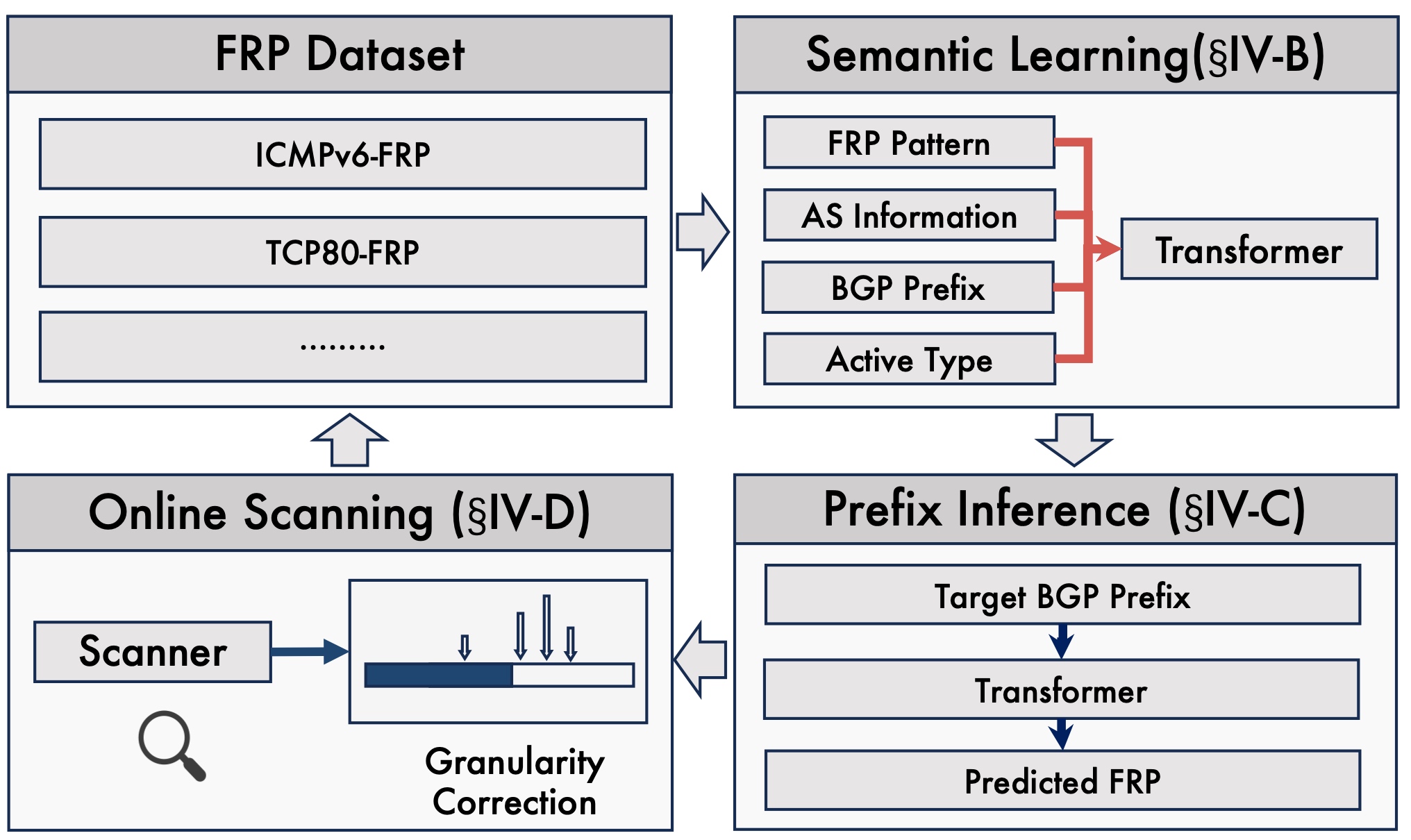 Gungnir: Autoregressive Model for Unified Generation of IPv6 Fully Responsive PrefixesChentian Wei, Ying Liu, Lin He#, Daguo Cheng, Jiasheng ZhouIn Proceedings of the 33rd IEEE International Conference on Network Protocols (ICNP 2025)
Gungnir: Autoregressive Model for Unified Generation of IPv6 Fully Responsive PrefixesChentian Wei, Ying Liu, Lin He#, Daguo Cheng, Jiasheng ZhouIn Proceedings of the 33rd IEEE International Conference on Network Protocols (ICNP 2025)
Seoul, South Korea, September 22-25, 2025IPv6 Internet MeasurementWith the widespread adoption of IPv6, its vast address space presents significant challenges for network asset discovery. Traditional exhaustive scanning approaches are no longer practical, while strategies based on target generation algorithms are increasingly undermined by the existence of Fully Responsive Prefixes (FRPs)—prefixes in which all addresses appear responsive to probing. FRPs distort scanning results, introducing bias and inefficiency. Existing FRP probing techniques suffer from limited scalability, poor accuracy, and restricted applicability in large-scale IPv6 environments. To this end, we propose Gungnir, a multi-protocol unified FRP probing framework based on autoregressive semantic modeling. Gungnir captures the intricate relationships between FRP patterns and their influencing factors through a deep semantic learning architecture. It leverages prefix inference and a granularity correction mechanism to accurately predict and validate FRPs while avoiding errors introduced by incorrect prefix length estimation. Extensive experiments show that Gungnir outperforms state-of-the-art techniques, achieving up to 27× greater efficiency, 4.2× broader coverage, and discovering more autonomous systems and routing prefixes under the same prefix budget. Beyond performance, we analyze the service and port distributions of the discovered FRPs, uncovering operational patterns and potential security implications. These insights offer valuable guidance for IPv6 measurement, address discovery, and network defense. Code is available at https://github.com/THUNAME/Gungnir.
@inproceedings{wei2025gungnir, title = {Gungnir: Autoregressive Model for Unified Generation of IPv6 Fully Responsive Prefixes}, author = {Wei, Chentian and Liu, Ying and He, Lin and Cheng, Daguo and Zhou, Jiasheng}, booktitle = {Proceedings of the 33rd IEEE International Conference on Network Protocols (ICNP 2025)}, year = {2025}, pages = {1-12}, doi = {10.1109/ICNP65844.2025.11192425}, address = {Seoul, South Korea}, date = {September 22-25}, } - ICNP
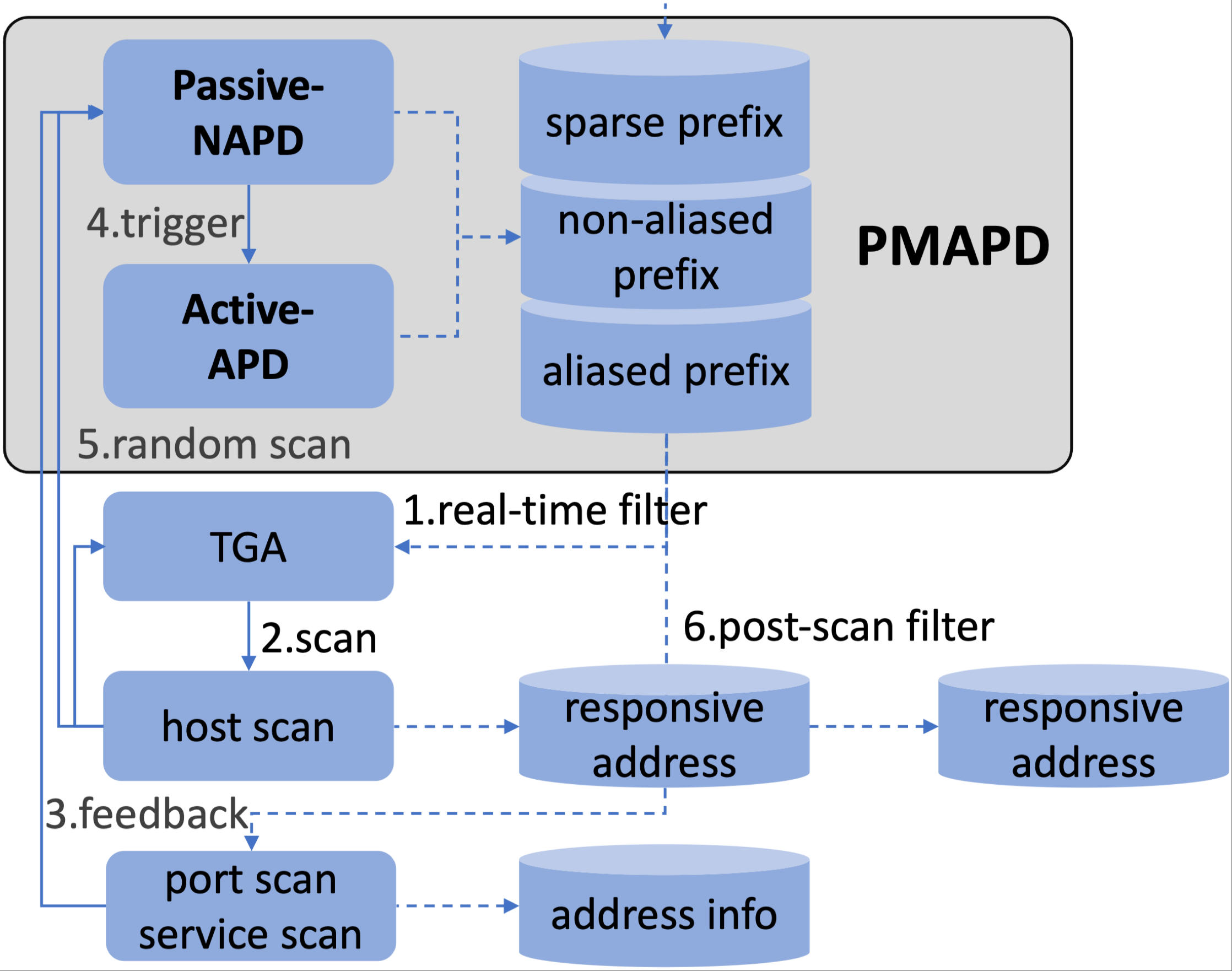 PMAPD: A Passive-enhanced Multi-level Aliased Prefix Detection Approach for IPv6 ScanningWei Zhang, Gang Ren, Xia Yin, Lin HeIn Proceedings of the 33rd IEEE International Conference on Network Protocols (ICNP 2025)
PMAPD: A Passive-enhanced Multi-level Aliased Prefix Detection Approach for IPv6 ScanningWei Zhang, Gang Ren, Xia Yin, Lin HeIn Proceedings of the 33rd IEEE International Conference on Network Protocols (ICNP 2025)
Seoul, South Korea, September 22-25, 2025IPv6 Internet MeasurementIPv6 scanning is a critical technique for network security assessment and Internet measurement. However, the prevalence of aliased prefixes significantly distorts scan results and severely interferes with target generation algorithms (TGAs) that rely on dynamic density feedback. To address the limitations of existing aliased prefix detection methods, such as insufficient accuracy and excessive overhead, this paper proposes PMAPD, a Passive-enhanced Multi-level Aliased Prefix Detection approach. PMAPD integrates passive analysis with active probing. The passive analysis component reuses existing scan data—primarily host responsiveness obtained at no extra cost from the main address scan, and opportunistically uses port and service information if available, to enhance detection accuracy and efficiency. The active probing component builds upon the strengths of prior active methods while incorporating optimizations to achieve a better balance between detection precision and cost. Experimental results demonstrate PMAPD’s superiority in improving the discovery of de-aliased active addresses, reducing aliased addresses in scanning results, and significantly lowering detection overhead. Across three different TGAs tested (6Tree, DET, 6Sense), PMAPD significantly outperforms the widely used traditional method MAPD: it improves the de-aliased hits by 12% to 57%, substantially reduces the aliased ratio in scan results by over 9% to 94%, and dramatically lowers detection overhead, costing only 3% to 17% of MAPD’s overhead. PMAPD offers a novel and effective aliased prefix detection solution for efficient and accurate IPv6 network scanning.
@inproceedings{zhang2025pmapd, title = {PMAPD: A Passive-enhanced Multi-level Aliased Prefix Detection Approach for IPv6 Scanning}, author = {Zhang, Wei and Ren, Gang and Yin, Xia and He, Lin}, booktitle = {Proceedings of the 33rd IEEE International Conference on Network Protocols (ICNP 2025)}, year = {2025}, pages = {1-11}, doi = {10.1109/ICNP65844.2025.11192373}, address = {Seoul, South Korea}, date = {September 22-25}, } - IWQoS
 Bringing New Life to Old Tools: Measuring Source Address Validation Deployment with 6in4 TunnelsJiaxing Guo, Lin He#, Daguo Cheng, Xingang Shi, Ying LiuIn Proceedings of the 33rd IEEE/ACM International Symposium on Quality of Service (IWQoS 2025)
Bringing New Life to Old Tools: Measuring Source Address Validation Deployment with 6in4 TunnelsJiaxing Guo, Lin He#, Daguo Cheng, Xingang Shi, Ying LiuIn Proceedings of the 33rd IEEE/ACM International Symposium on Quality of Service (IWQoS 2025)
Gold Coast, Australia, July 2–4, 2025Internet MeasurementSource Address Validation (SAV) is a security mechanism deployed at network boundaries to prevent packets with illegal source addresses from crossing these boundaries. While SAV plays an important role in mitigating source address spoofing, its deployment across the global Internet remains limited. Measuring SAV deployment is essential for enhancing the understanding of the security landscape of networks. In this study, we propose a novel method for measuring SAV deployment based on 6in4 tunnels, complementing existing measurement work. Using this method, we measure inbound SAV for IPv4 and outbound SAV for IPv6, obtaining results from 12,417 and 2,104 Autonomous Systems (ASes), respectively. Based on our measurements, we analyze factors that may influence SAV deployment, including network address space size, AS type, and geographical location. Additionally, we provide a global heatmap of spoofable rates for networks in different countries and regions. Note that the measuring method using 6in4 tunnels we introduce is not only applicable to SAV measurements but also holds potential for other measurement tasks, such as connectivity testing and transmission path discovery. This method offers a new way for large-scale measurement tasks across different networks, which may benefit future research.
@inproceedings{guo2025bringing, title = {Bringing New Life to Old Tools: Measuring Source Address Validation Deployment with 6in4 Tunnels}, author = {Guo, Jiaxing and He, Lin and Cheng, Daguo and Shi, Xingang and Liu, Ying}, booktitle = {Proceedings of the 33rd IEEE/ACM International Symposium on Quality of Service (IWQoS 2025)}, year = {2025}, pages = {1-10}, doi = {10.1109/IWQoS65803.2025.11143432}, address = {Gold Coast, Australia}, date = {July 2–4}, } - IWQoS
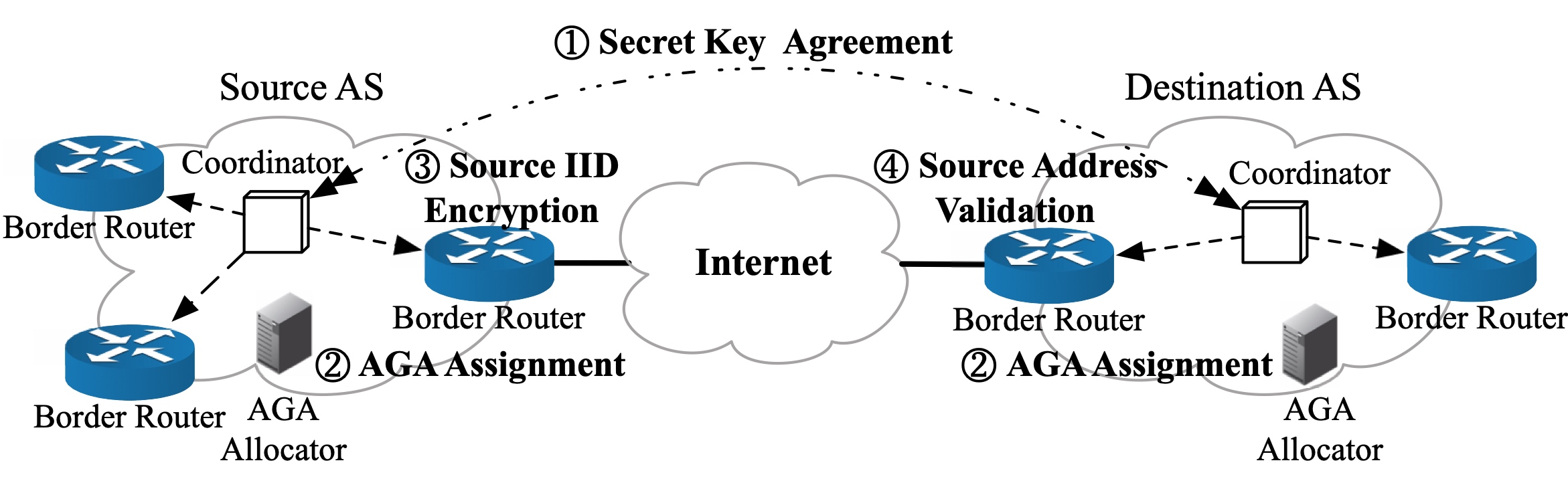
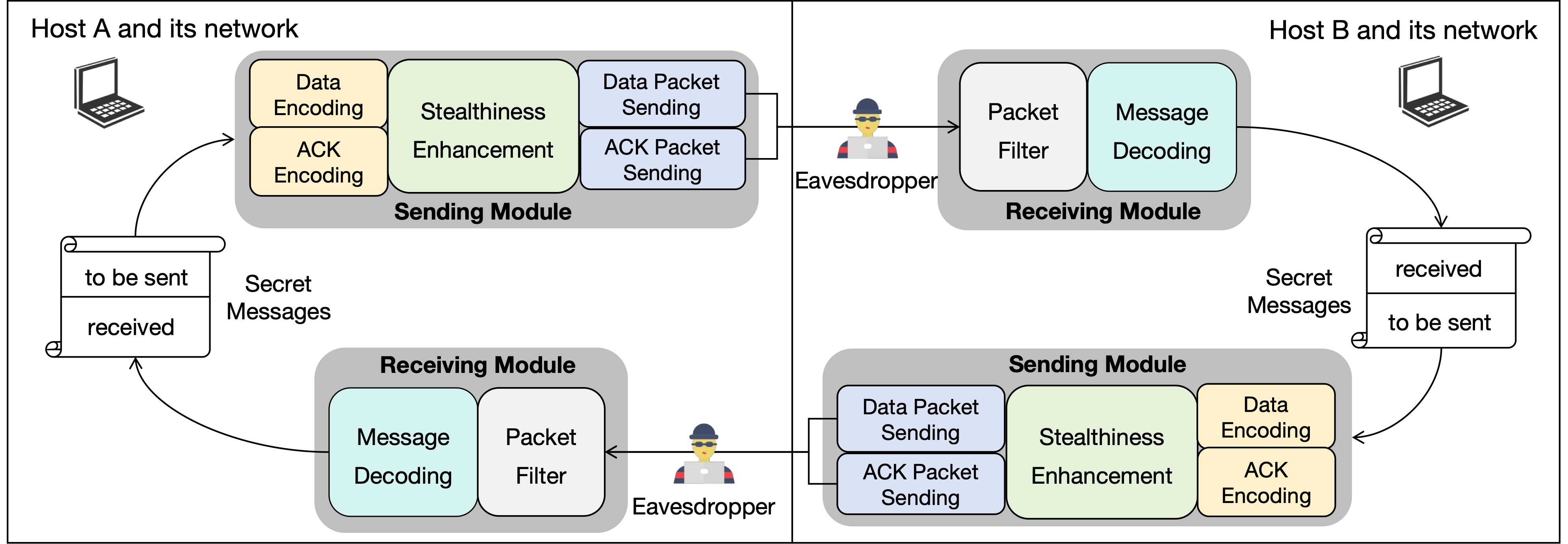 APCC: Enabling Reliable IPv6 Covert Communication with Aliased PrefixesZhaoan Wang, Lin He#, Daguo Cheng, Ying LiuIn Proceedings of the 33rd IEEE/ACM International Symposium on Quality of Service (IWQoS 2025)
APCC: Enabling Reliable IPv6 Covert Communication with Aliased PrefixesZhaoan Wang, Lin He#, Daguo Cheng, Ying LiuIn Proceedings of the 33rd IEEE/ACM International Symposium on Quality of Service (IWQoS 2025)
Gold Coast, Australia, July 2–4, 2025IPv6 Protocol DesignCovert communication ensures undetectable information exchange between parties while posing risks when exploited for malicious purposes. Existing network covert channels face challenges in reliability, throughput, and stealthiness due to packet loss, limited capacity, and detectable anomalies. This paper proposes APCC, a reliable covert communication system that leverages IPv6 aliased prefixes for the first time, where secret data is embedded in the Interface Identifier field of IPv6 addresses. APCC enhances stealthiness through encryption and camouflage strategies (e.g., traffic blending and rate control). Additionally, it employs a reliable transmission mechanism incorporating sequence numbering, acknowledgment, and retransmission to mitigate packet loss and reordering. It ensures deployment flexibility across ICMPv6, UDP, or TCP protocols. Evaluations in real-world and simulated environments demonstrate that APCC achieves 100% accuracy under high latency (800 ms RTT) and packet loss (10%), with throughput up to 34.7 Kbps. Detection tests show APCC evades major intrusion detection systems (Snort, Zeek) except for Suricata’s TCP alerts. We also propose mitigation measures to reduce APCC’s potential negative impact. This work highlights critical vulnerabilities in IPv6 infrastructure while advancing robust covert communication methodologies for high-stakes scenarios.
@inproceedings{wang2025apcc, title = {APCC: Enabling Reliable IPv6 Covert Communication with Aliased Prefixes}, author = {Wang, Zhaoan and He, Lin and Cheng, Daguo and Liu, Ying}, booktitle = {Proceedings of the 33rd IEEE/ACM International Symposium on Quality of Service (IWQoS 2025)}, year = {2025}, pages = {1-10}, doi = {10.1109/IWQoS65803.2025.11143455}, address = {Gold Coast, Australia}, date = {July 2–4}, } - ICC
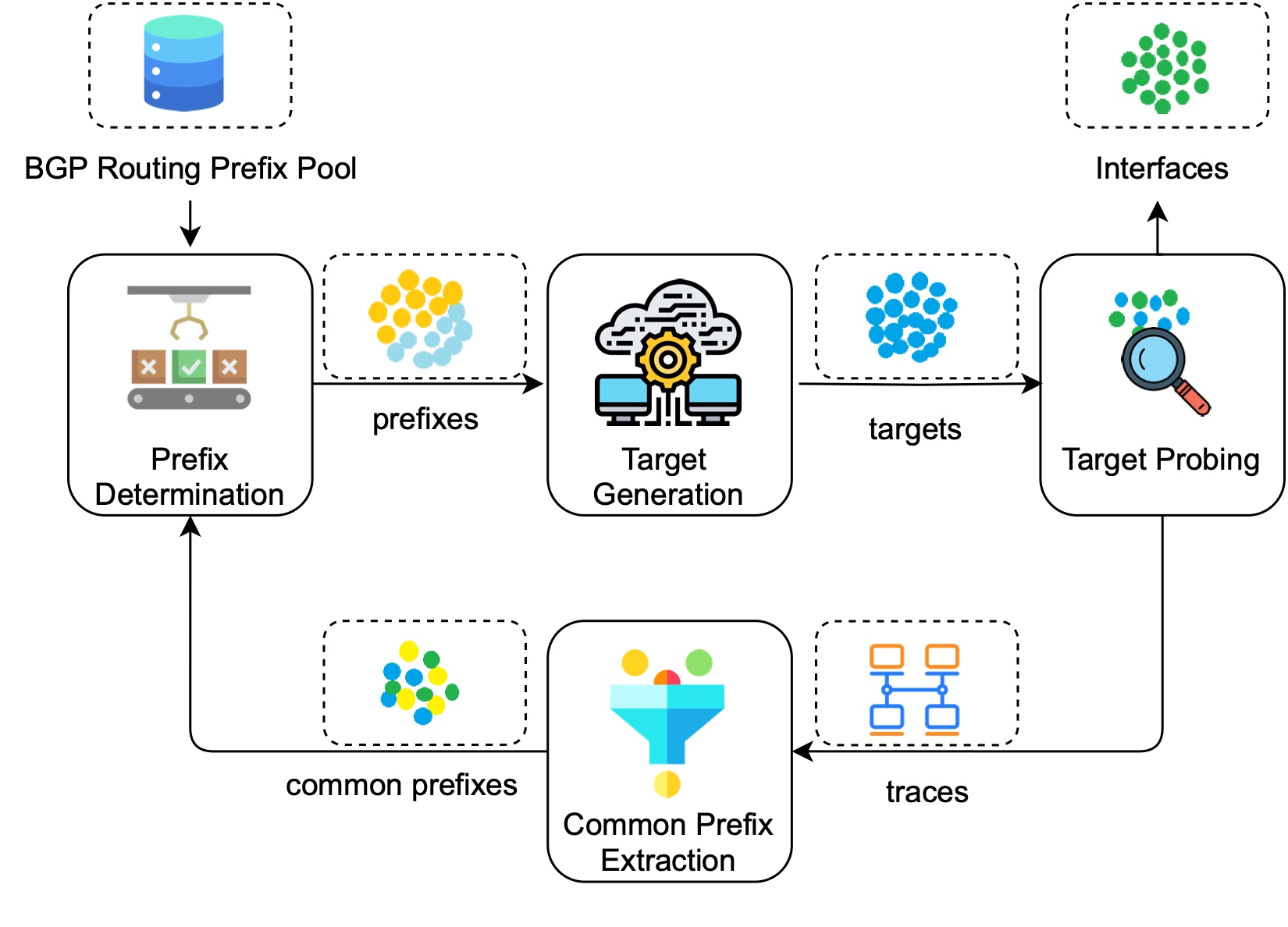 TopoMiner: Efficient IPv6 Topology DiscoveryLi Tan, Hongwei Li, Lin He#, Wenwen Gong, Guanglei Song, Daguo Cheng, Jiahai Yang, Ying LiuIn Proceedings of the 2025 IEEE International Conference on Communications (ICC 2025)
TopoMiner: Efficient IPv6 Topology DiscoveryLi Tan, Hongwei Li, Lin He#, Wenwen Gong, Guanglei Song, Daguo Cheng, Jiahai Yang, Ying LiuIn Proceedings of the 2025 IEEE International Conference on Communications (ICC 2025)
Montreal, Canada, June 8–12, 2025IPv6 Internet MeasurementTopology discovery can be used to obtain the connectivity and operational status of network devices by discovered interfaces. By performing topology discovery on networks, administrators can better understand and manage networks and improve network reliability and security. However, the large IPv6 address space, sparse address distribution, and unknown address assignment policies make it infeasible to simply and roughly probe the IPv6 network topology. To this end, we design an efficient IPv6 interface-level topology discovery method called TopoMiner. It performs multiple rounds of probing the IPv6 topology with the given set of IPv6 prefixes and locates the high-density interface regions based on the results of each round of topology discovery. TopoMiner then performs prefix expansion and address generation for the high-density interface address regions. At the same time, TopoMiner also uses some of the prefixes that have been probed to regenerate the target addresses. In this way, TopoMiner can dynamically adjust the breadth and depth of topology discovery and thus complete multiple rounds of topology discovery within the packet-sending budget. In real-word probing, TopoMiner achieves a 3-7X enhancement in probing efficiency compared to state-of-the-art topology discovery methods.
@inproceedings{tan20256topominer, title = {TopoMiner: Efficient IPv6 Topology Discovery}, author = {Tan, Li and Li, Hongwei and He, Lin and Gong, Wenwen and Song, Guanglei and Cheng, Daguo and Yang, Jiahai and Liu, Ying}, booktitle = {Proceedings of the 2025 IEEE International Conference on Communications (ICC 2025)}, year = {2025}, pages = {4326-4332}, doi = {10.1109/ICC52391.2025.11162067}, address = {Montreal, Canada}, date = {June 8–12}, } - NOMS
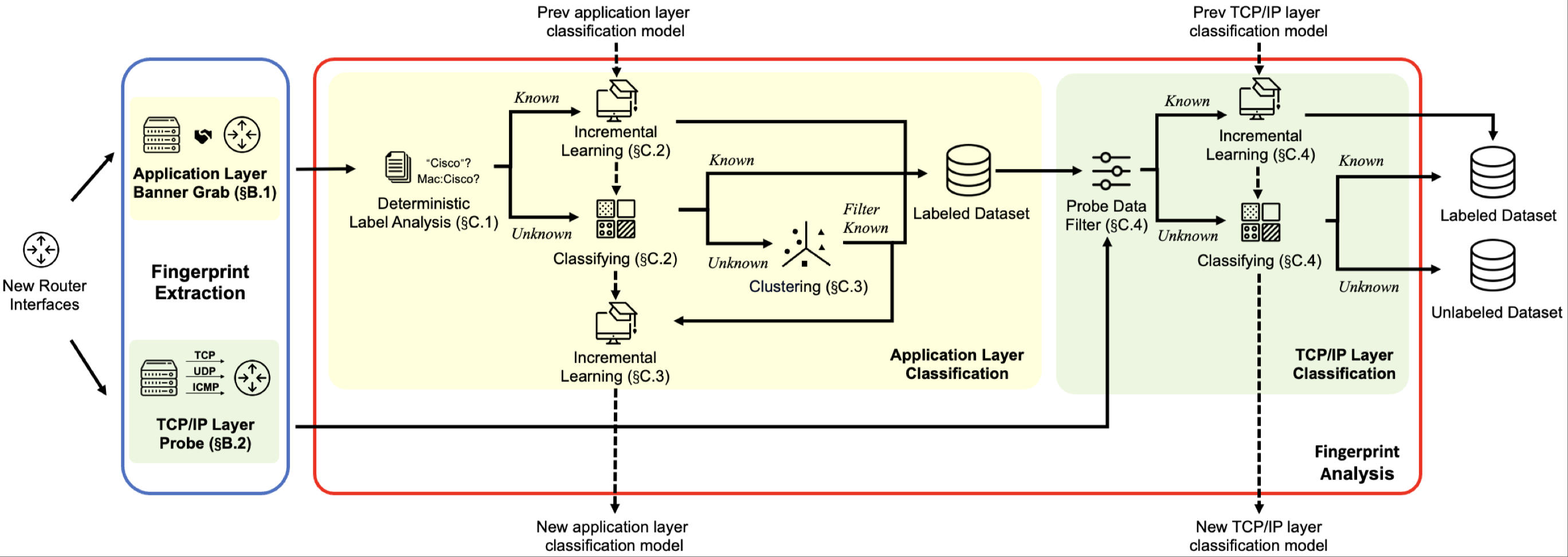 6RV: Incremental Learning-based Continuous Identification of IPv6 Router VendorsIn Proceedings of the 38th IEEE/IFIP Network Operations and Management Symposium (NOMS 2025)
6RV: Incremental Learning-based Continuous Identification of IPv6 Router VendorsIn Proceedings of the 38th IEEE/IFIP Network Operations and Management Symposium (NOMS 2025)
Honolulu, HI, USA, May 12–16, 2025IPv6 Internet MeasurementThe growth of IPv6 networks has led to an expanding number of network routers, but there is not enough research on vendors of these devices. Existing router vendor identification algorithms are based on IPv4, and these static analysis algorithms cannot adapt to dynamically changing IPv6 networks. In this paper, we develop 6RV, a framework for IPv6 router vendors continuous identification based on incremental learning. First, we count the addresses of newly discovered router interfaces every month and obtain router device fingerprints through active probing, and then analyze these data fingerprints through an incremental learning approach to identify the router vendors of new nodes. We validate our identification framework on the ITDK dataset over a period of 8 months, obtaining more than 500K router vendor labels with 94% correctness. Finally, we also analyze the IPv6 router vendor dataset from different perspectives and draw some interesting conclusions.
@inproceedings{li20256rv, title = {6RV: Incremental Learning-based Continuous Identification of IPv6 Router Vendors}, author = {Li, Shenao and Wang, Zhiliang and Yang, Jiahai and Dong, Enhuan and Li, Chenglong and He, Lin and Zhang, Hui and Song, Guanglei}, booktitle = {Proceedings of the 38th IEEE/IFIP Network Operations and Management Symposium (NOMS 2025)}, year = {2025}, pages = {1-9}, doi = {10.1109/NOMS57970.2025.11073725}, address = {Honolulu, HI, USA}, date = {May 12–16}, }
2024
- P4runpro: Enabling Runtime Programmability for RMT Programmable SwitchesIn Proceedings of the 38th Annual Conference of the ACM Special Interest Group on Data Communication (SIGCOMM 2024)
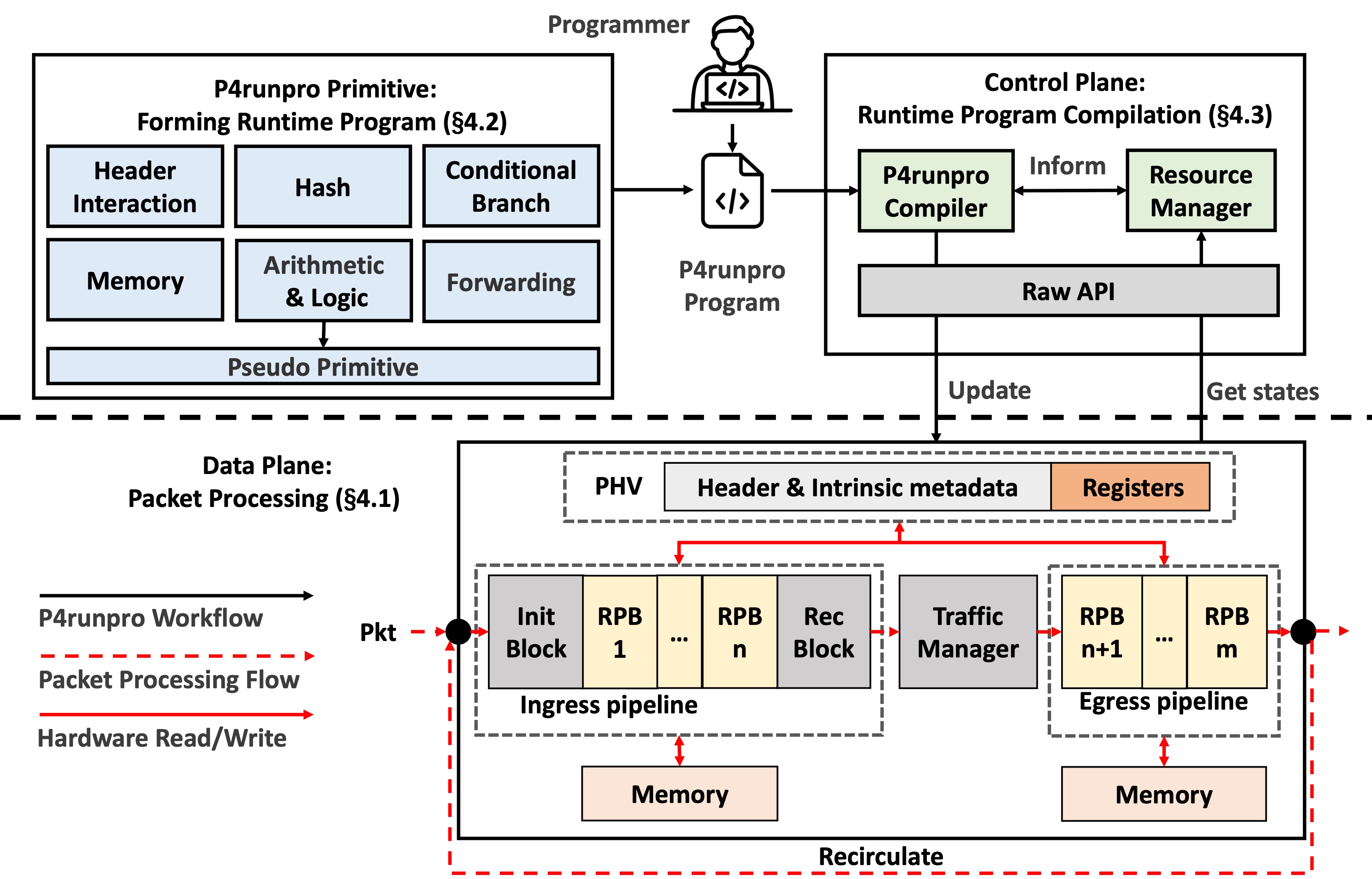
Sydney, Australia, August 4-8, 2024Programmable NetworksProgrammable switches have revolutionized network operations by enabling the flexible customization of packet processing logic using language like P4. However, changing the programs running on the switch requires disturbing traffic and suspending other unrelated programs. In this paper, we present P4runpro, enabling runtime data plane updates with dynamic resource allocation. The P4runpro data plane abstracts hardware resources and defines dynamically reconfigurable atomic operations that form packet processing logic. P4runpro provides runtime programming interfaces called P4runpro primitives for the operator to write high-level programs. We have designed the P4runpro compiler to automatically and consistently link the P4runpro programs to the running data plane. We implement our prototype on a Tofino switch. We implement 15 example runtime programs using P4runpro to demonstrate its generality and expressiveness. Our evaluation results show that compared to the state-of-the-art, P4runpro can respond within hundreds of milliseconds, achieve an average of 60% to 80% dynamic resource utilization, concurrently run ≈0.6K to ≈2.8K programs, and introduce lower overhead. Our case studies illustrate the benefit of runtime programming and prove the same functionality between P4runpro and conventional P4 programs.
@inproceedings{yang2024p4runpro, title = {P4runpro: Enabling Runtime Programmability for RMT Programmable Switches}, author = {Yang, Yifan and He, Lin and Zhou, Jiasheng and Shi, Xiaoyi and Cao, Jiamin and Liu, Ying}, booktitle = {Proceedings of the 38th Annual Conference of the ACM Special Interest Group on Data Communication (SIGCOMM 2024)}, year = {2024}, pages = {921-937}, doi = {10.1145/3651890.3672230}, address = {Sydney, Australia}, date = {August 4-8}, } - INFOCOM
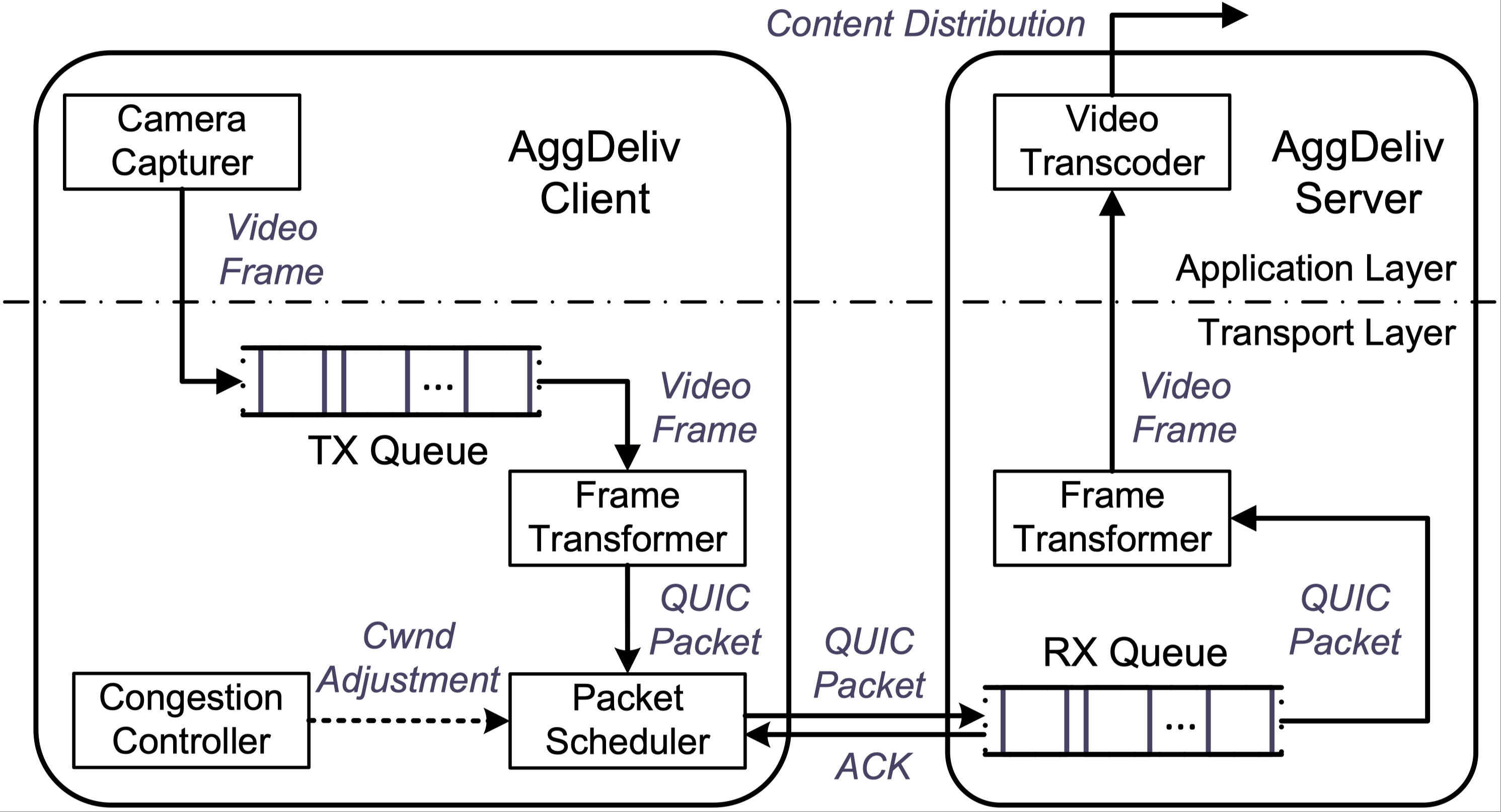 AggDeliv: Aggregating Multiple Wireless Links for Efficient Mobile Live Video DeliveryJinlong E, Lin He, Zongyi Zhao, Yachen Wang, Gonglong Chen, Wei ChenIn Proceedings of the 43rd IEEE Conference on Computer Communications (INFOCOM 2024)
AggDeliv: Aggregating Multiple Wireless Links for Efficient Mobile Live Video DeliveryJinlong E, Lin He, Zongyi Zhao, Yachen Wang, Gonglong Chen, Wei ChenIn Proceedings of the 43rd IEEE Conference on Computer Communications (INFOCOM 2024)
Vancouver, Canada, May 20–23, 2024Network ArchitectureMobile live-streaming applications with stringent latency and bandwidth requirements have gained tremendous attention in recent years. Encountered with bandwidth insufficiency and congestion instability of the wireless uplinks, multi-access networking provides opportunities to achieve fast and robust connectivity. However, the state-of-the-art multi-path transmission solutions are lack of adaptivity to the heterogeneous and dynamic nature of wireless networks. Meanwhile, the indispensable video coding and transformation bring about extra latency and make the video delivery vulnerable to network throughput fluctuation. This paper presents AggDeliv, a framework that provides efficient and robust multi-path transmission for mobile live video delivery. The key idea is to relate multi-path packet scheduling to congestion control optimization over diverse wireless links and adapt it to the mobile video characteristics. This is achieved by probabilistic packet allocation based on links’ congestion windows, wireless-oriented delay and loss aware congestion control, as well as lightweight video frame coding and network adaptive frame-packet transformation. Real-world evaluations demonstrate that our framework significantly outperforms the state-of-the-art solutions on aggregate goodput and streaming video bitrate.
@inproceedings{e2024aggdeliv, title = {AggDeliv: Aggregating Multiple Wireless Links for Efficient Mobile Live Video Delivery}, author = {E, Jinlong and He, Lin and Zhao, Zongyi and Wang, Yachen and Chen, Gonglong and Chen, Wei}, booktitle = {Proceedings of the 43rd IEEE Conference on Computer Communications (INFOCOM 2024)}, year = {2024}, pages = {1171-1180}, doi = {10.1109/INFOCOM52122.2024.10621184}, address = {Vancouver, Canada}, date = {May 20–23}, } - ICNP
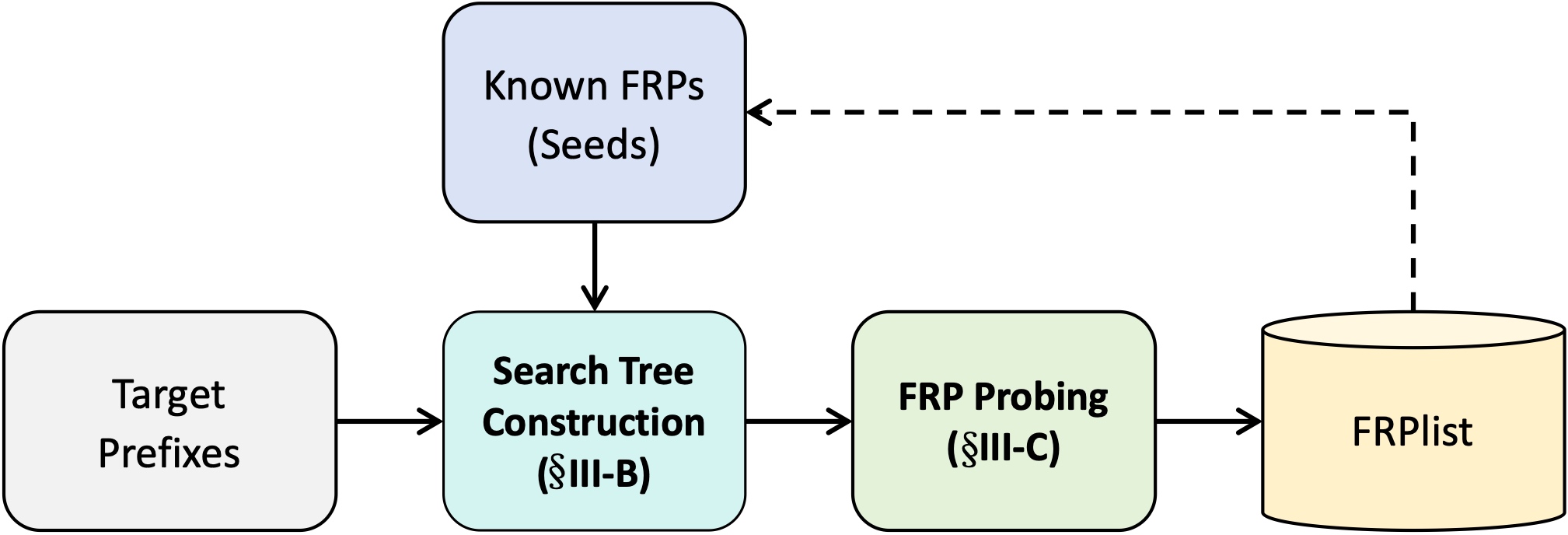 Luori: Active Probing and Evaluation of Internet-wide IPv6 Fully Responsive PrefixesDaguo Cheng, Lin He#, Chentian Wei, Qilei Yin, Boran Jin, Zhaoan Wang, Xiaoteng Pan, Sixu Zhou, Ying Liu, Shenglin Zhang, Fuchao Tan, Wenmao LiuIn Proceedings of the 32nd IEEE International Conference on Network Protocols (ICNP 2024)
Luori: Active Probing and Evaluation of Internet-wide IPv6 Fully Responsive PrefixesDaguo Cheng, Lin He#, Chentian Wei, Qilei Yin, Boran Jin, Zhaoan Wang, Xiaoteng Pan, Sixu Zhou, Ying Liu, Shenglin Zhang, Fuchao Tan, Wenmao LiuIn Proceedings of the 32nd IEEE International Conference on Network Protocols (ICNP 2024)
Charleroi, Belgium, October 28-31, 2024IPv6 Internet MeasurementWith the large-scale deployment and application of IPv6, IPv6 network measurements will become increasingly important. However, a special type of IPv6 prefix called Fully Responsive Prefix (FRP) is having a significant impact on IPv6 measurement campaigns, which is defined as all addresses under a prefix responding to scans. Obviously, there cannot be a real responder behind each of these addresses. To reveal the current status and impact of Internet-wide IPv6 FRPs, we propose for the first time an active probing method for Internet-wide IPv6 FRPs, Luori, which transforms the active probing process under IPv6 huge prefix space (potential range of prefix presence) into a dynamic search process in a tree based on reinforcement learning, achieving efficient probing of arbitrary routing prefixes. The evaluation results show that Luori found 31.7K largest FRPs in a single Internet-wide probing with 11M budget, covering 1.5×1030 address space, which is 106× that of existing methods. More importantly, after six months of Internet-wide probing, we have found 516K largest FRPs, which covers 1.3 × 1033 address space and 795 ASes, making it the largest publicly known FRP list. Based on this list, we screen out 20% of the addresses covered by FRPs from a well-known IPv6 active address dataset. Furthermore, we further analyze and find that the distribution of these FRPs is extensive and their implementation methods are diverse, which can provide beneficial references for the practical application of FRPs. We also make this list publicly available and maintain it long-term for use and study by relevant researchers.
@inproceedings{cheng2024luori, title = {Luori: Active Probing and Evaluation of Internet-wide IPv6 Fully Responsive Prefixes}, author = {Cheng, Daguo and He, Lin and Wei, Chentian and Yin, Qilei and Jin, Boran and Wang, Zhaoan and Pan, Xiaoteng and Zhou, Sixu and Liu, Ying and Zhang, Shenglin and Tan, Fuchao and Liu, Wenmao}, booktitle = {Proceedings of the 32nd IEEE International Conference on Network Protocols (ICNP 2024)}, year = {2024}, pages = {1-12}, doi = {10.1109/ICNP61940.2024.10858548}, address = {Charleroi, Belgium}, date = {October 28-31}, } - ICNP
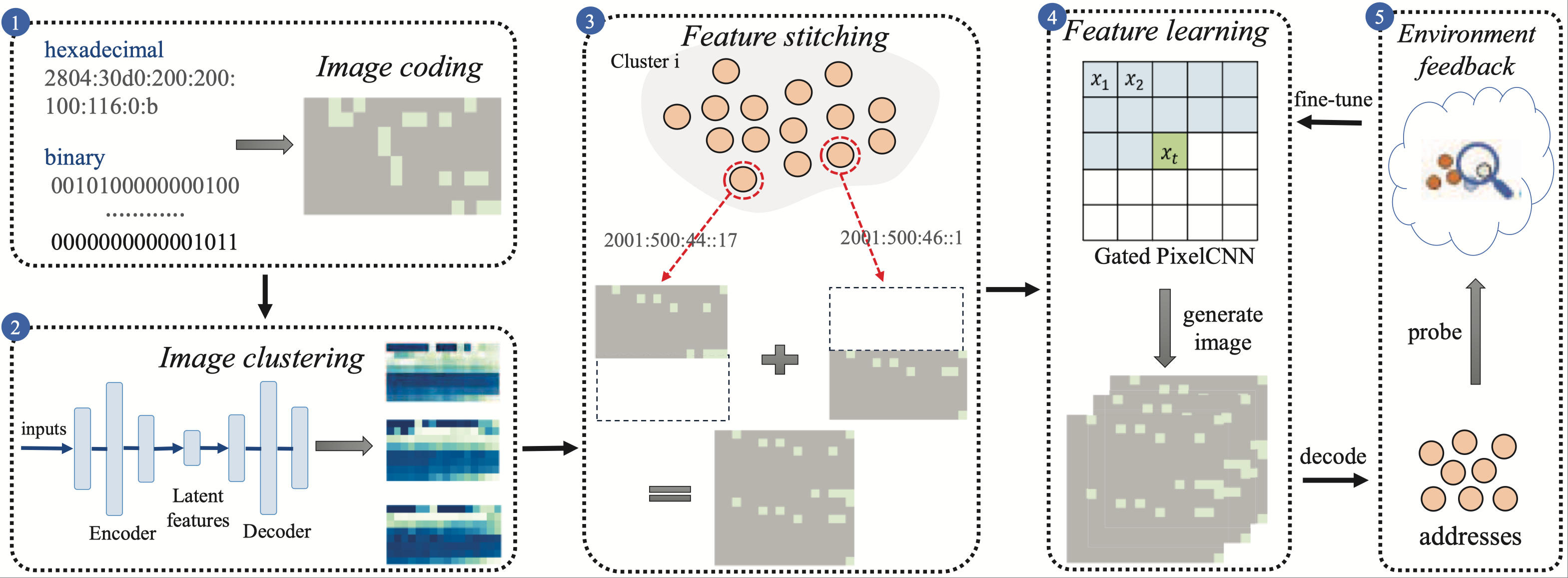 6Vision: Image-encoding-based IPv6 Target Generation in Few-seed ScenariosWenjian Zhang, Guanglei Song, Lin He, Jinlei Lin, Songyun Wu, Zhiliang Wang, Chenglong Li, Jiahai YangIn Proceedings of the 32nd IEEE International Conference on Network Protocols (ICNP 2024)
6Vision: Image-encoding-based IPv6 Target Generation in Few-seed ScenariosWenjian Zhang, Guanglei Song, Lin He, Jinlei Lin, Songyun Wu, Zhiliang Wang, Chenglong Li, Jiahai YangIn Proceedings of the 32nd IEEE International Conference on Network Protocols (ICNP 2024)
Charleroi, Belgium, October 28-31, 2024IPv6 Internet MeasurementEfficient global Internet scanning is crucial for network measurement and security analysis. While existing target generation algorithms verify remarkable performance in largescale detection, their efficiency notably diminishes in few-seed scenarios. This decline is primarily attributed to the intricate configuration rules and sampling bias of seed addresses. Moreover, instances where BGP prefixes have few seed addresses are widespread, constituting 63.65% of occurrences. We introduce 6Vision to tackle this challenge by introducing a novel approach of encoding IPv6 addresses into images, facilitating comprehensive analysis of intricate configuration rules. Through feature stitching, 6Vision not only improves the learnable features but also amalgamates addresses associated with configuration patterns for enhanced learning. Moreover, it integrates an environmental feedback mechanism to refine model parameters based on identified active addresses, thereby alleviating the sampling bias inherent in seed addresses. As a result, 6Vision achieves high-accuracy detection even in few-seed scenarios. The HitRate of 6Vision is improved by 181%∼2,490% compared to existing algorithms, while the CoverNum is 1.18∼11.20 times that of them. Additionally, 6Vision can function as a preliminary detection module for existing algorithms, yielding a conversion gain (CG) ranging from 242%∼2,081%. Ultimately, we achieve a conversion rate (CR) of 28.97% for few-seed scenarios. We enrich the IPv6 hitlist, not only enhancing current target generation algorithms for large-scale address detection in few-seed scenarios but also effectively supporting IPv6 network measurement and security analysis.
@inproceedings{zhang20246vision, title = {6Vision: Image-encoding-based IPv6 Target Generation in Few-seed Scenarios}, author = {Zhang, Wenjian and Song, Guanglei and He, Lin and Lin, Jinlei and Wu, Songyun and Wang, Zhiliang and Li, Chenglong and Yang, Jiahai}, booktitle = {Proceedings of the 32nd IEEE International Conference on Network Protocols (ICNP 2024)}, year = {2024}, pages = {1-12}, doi = {10.1109/ICNP61940.2024.10858550}, address = {Charleroi, Belgium}, date = {October 28-31}, } - IPCCC
 Overlooked Backdoors: Investigating 6to4 Tunnel Nodes and Their Exploitation in the WildJiaxing Guo, Lin He#, Ying LiuIn Proceedings of the 43rd IEEE International Performance Computing and Communications Conference (IPCCC 2024)
Overlooked Backdoors: Investigating 6to4 Tunnel Nodes and Their Exploitation in the WildJiaxing Guo, Lin He#, Ying LiuIn Proceedings of the 43rd IEEE International Performance Computing and Communications Conference (IPCCC 2024)
Orlando, Florida, USA, November 22–24, 2024IPv6 Internet MeasurementAs native IPv6 adoption increases, the use of 6to4 tunnels has declined, yet they remain a significant security concern in today’s Internet. This study investigates the real-world deployment of 6to4 tunnels, revealing their current scale, characteristics, and security implications. We identify open 6to4 relays in 216 countries and 13,114 autonomous systems, noting stable short-term counts but a long-term decline. We analyze the security of these nodes and find over 578k nodes vulnerable to address spoofing and packet injection. Additionally, we present several under-emphasized scenarios where open 6to4 nodes are abused, including leveraging services on 6to4 nodes as traffic amplifiers, circumventing restrictions using multiple 6to4 addresses, and connecting 6to4 nodes to render attacks untraceable.
@inproceedings{guo2024overlooked, title = {Overlooked Backdoors: Investigating 6to4 Tunnel Nodes and Their Exploitation in the Wild}, author = {Guo, Jiaxing and He, Lin and Liu, Ying}, booktitle = {Proceedings of the 43rd IEEE International Performance Computing and Communications Conference (IPCCC 2024)}, year = {2024}, pages = {1-8}, doi = {10.1109/IPCCC59868.2024.10850165}, address = {Orlando, Florida, USA}, date = {November 22–24}, }
2023
- Your Router is My Prober: Measuring IPv6 Networks via ICMP Rate Limiting Side ChannelsLong Pan, Jiahai Yang, Lin He#, Zhiliang Wang, Leyao Nie, Guanglei Song, Yaozhong LiuIn Proceedings of the 30th Annual Network and Distributed System Security Symposium (NDSS 2023)
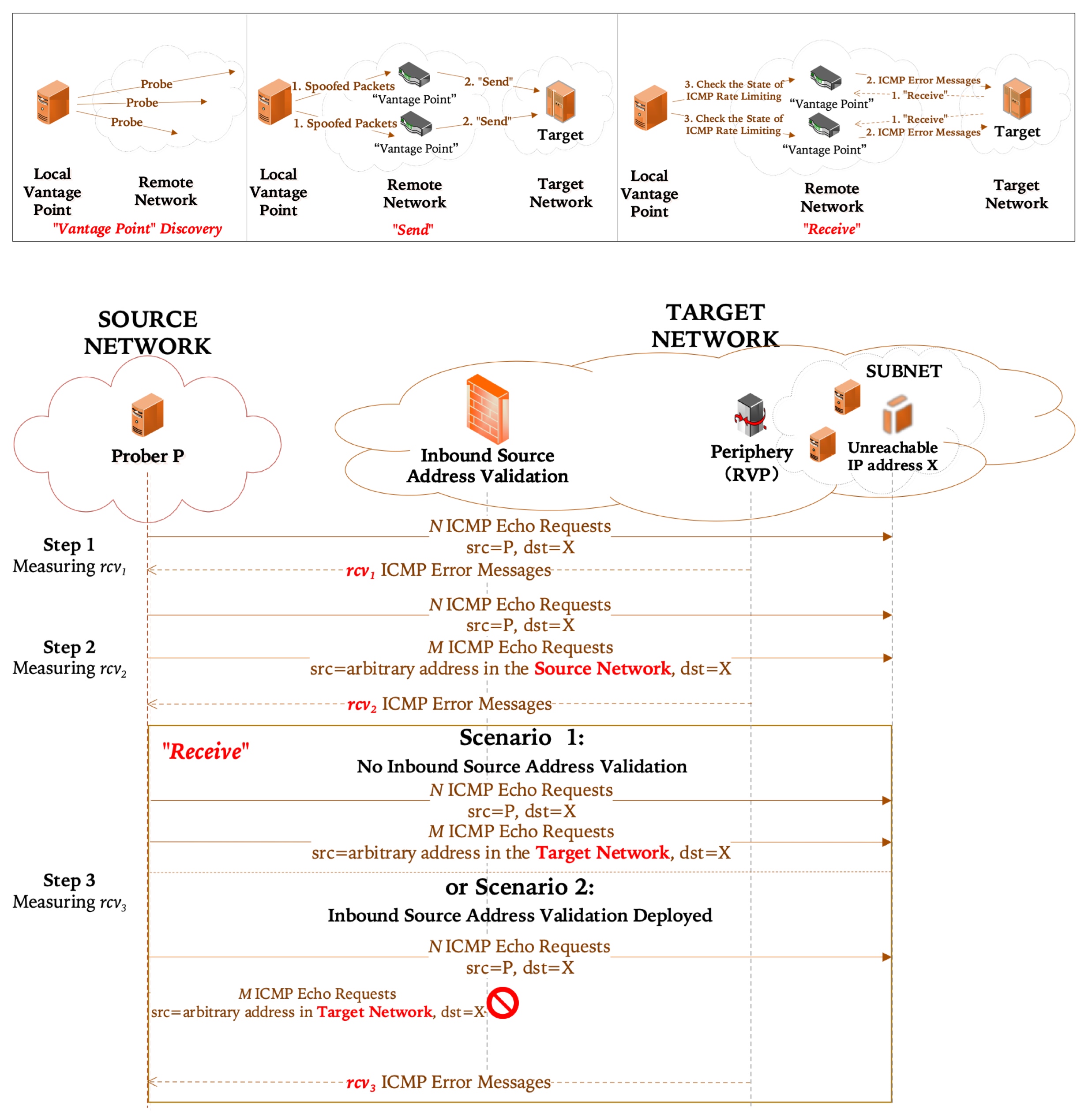
San Diego, California, USA, February 27 – March 3, 2023IPv6 Internet MeasurementActive Internet measurements face challenges when some measurements require many remote vantage points. In this paper, we propose a novel technique for measuring remote IPv6 networks via side channels in ICMP rate limiting, a required function for IPv6 nodes to limit the rate at which ICMP error messages are generated. This technique, iVantage, can to some extent use 1.1M remote routers distributed in 9.5k autonomous systems and 182 countries as our “vantage points”.We apply iVantage to two different, but both challenging measurement tasks: 1) measuring the deployment of inbound source address validation (ISAV) and 2) measuring reachability between arbitrary Internet nodes. We accomplish these two tasks from only one local vantage point without controlling the targets or relying on other services within the target networks. Our large-scale ISAV measurements cover 50% of all IPv6 autonomous systems and find 79% of them are vulnerable to spoofing, which is the most large-scale measurement study of IPv6 ISAV to date. Our method for reachability measurements achieves over 80% precision and recall in our evaluation. Finally, we perform an Internet-wide measurement of the ICMP rate limiting implementations, present a detailed discussion on ICMP rate limiting, particularly the potential security and privacy risks in the mechanism of ICMP rate limiting, and provide possible mitigation measures. We make our code available to the community.
@inproceedings{pan2023your, title = {Your Router is My Prober: Measuring IPv6 Networks via ICMP Rate Limiting Side Channels}, author = {Pan, Long and Yang, Jiahai and He, Lin and Wang, Zhiliang and Nie, Leyao and Song, Guanglei and Liu, Yaozhong}, booktitle = {Proceedings of the 30th Annual Network and Distributed System Security Symposium (NDSS 2023)}, year = {2023}, publisher = {The Internet Society}, address = {San Diego, California, USA}, date = {February 27 – March 3}, } - INFOCOM
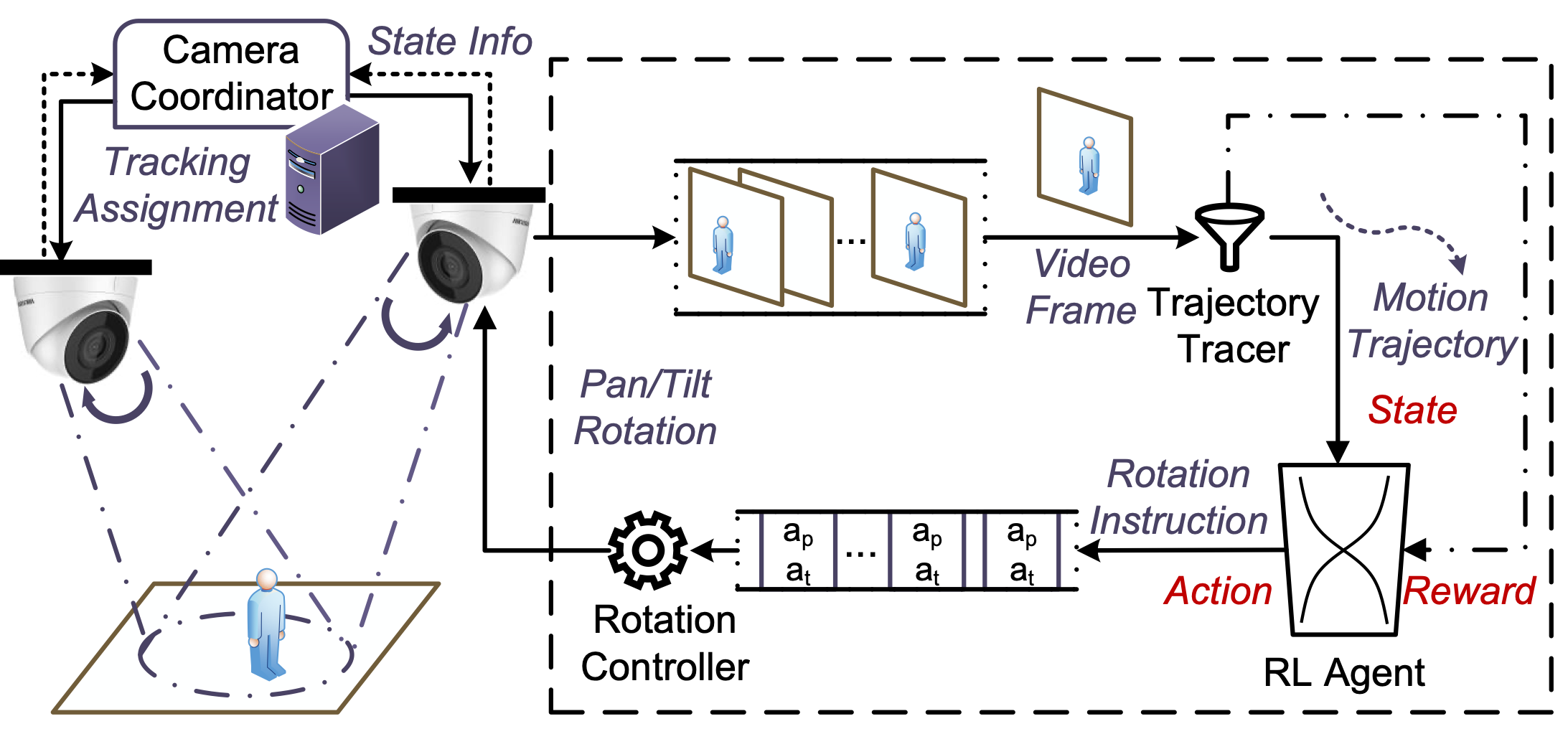
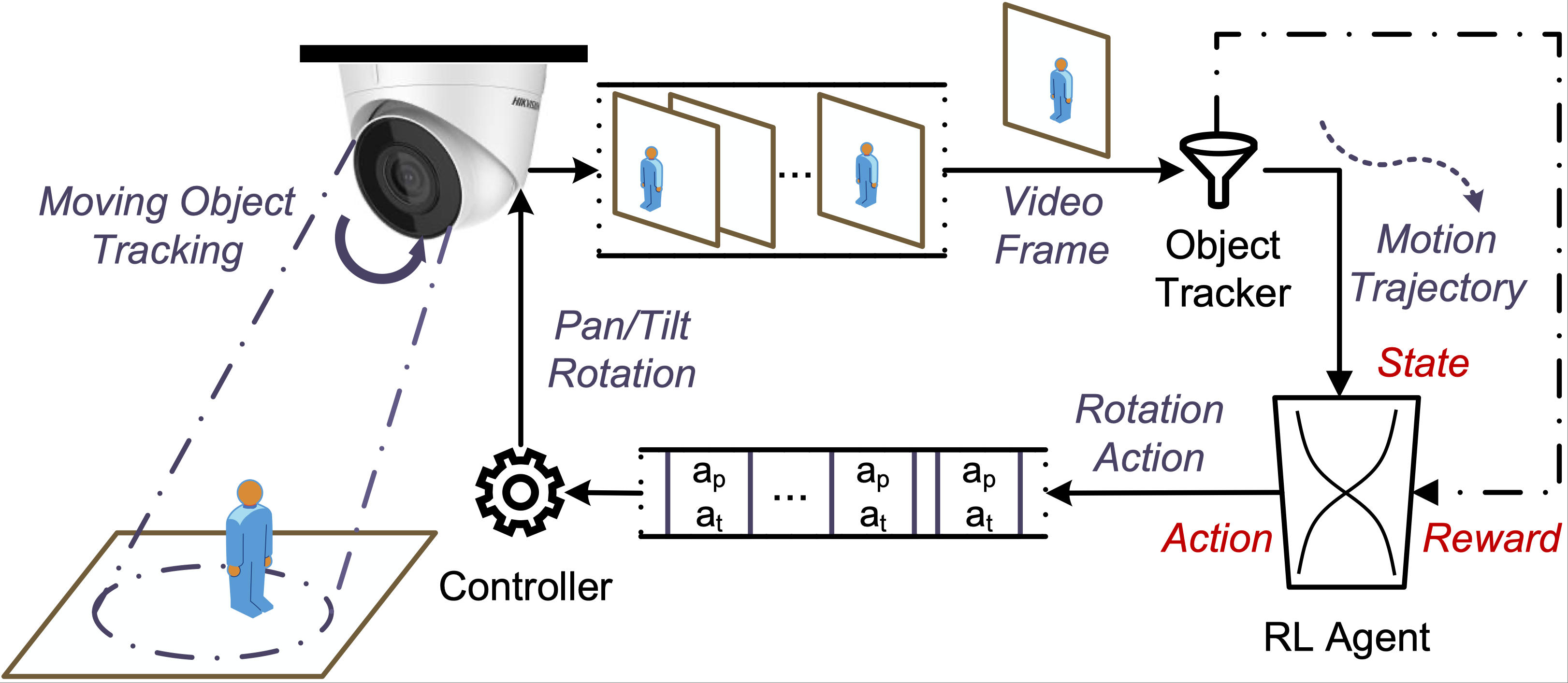 WiseCam: Wisely Tuning Wireless Pan-Tilt Cameras for Cost-Effective Moving Object TrackingJinlong E, Lin He, Zhenhua Li, Yunhao LiuIn Proceedings of the 42nd IEEE Conference on Computer Communications (INFOCOM 2023)
WiseCam: Wisely Tuning Wireless Pan-Tilt Cameras for Cost-Effective Moving Object TrackingJinlong E, Lin He, Zhenhua Li, Yunhao LiuIn Proceedings of the 42nd IEEE Conference on Computer Communications (INFOCOM 2023)
New York area, USA, May 17–20, 2023Network ManagementWith desired functionality of moving object tracking, wireless pan-tilt cameras are able to play critical roles in a growing diversity of surveillance environments. However, today’s pan-tilt cameras oftentimes underperform when tracking frequently moving objects like humans – they are prone to lose sight of objects and bring about excessive mechanical rotations that are especially detrimental to those energy-constrained outdoor scenarios. The ineffectiveness and high cost of state-of-the-art tracking approaches are rooted in their adherence to the industry’s simplicity principle, which leads to their stateless nature, performing gimbal rotations based only on the latest object detection. To address the issues, we design and implement WiseCam that wisely tunes the pan-tilt cameras to minimize mechanical rotation costs while maintaining long-term object tracking. We examine the performance of WiseCam by experiments on two types of pan-tilt cameras with different motors. Results show that WiseCam significantly outperforms the state-of-the-art tracking approaches on both tracking duration and power consumption.
@inproceedings{e2023wisecam, title = {WiseCam: Wisely Tuning Wireless Pan-Tilt Cameras for Cost-Effective Moving Object Tracking}, author = {E, Jinlong and He, Lin and Li, Zhenhua and Liu, Yunhao}, booktitle = {Proceedings of the 42nd IEEE Conference on Computer Communications (INFOCOM 2023)}, year = {2023}, pages = {1-10}, doi = {10.1109/INFOCOM53939.2023.10228926}, address = {New York area, USA}, date = {May 17–20}, } - IWQoS
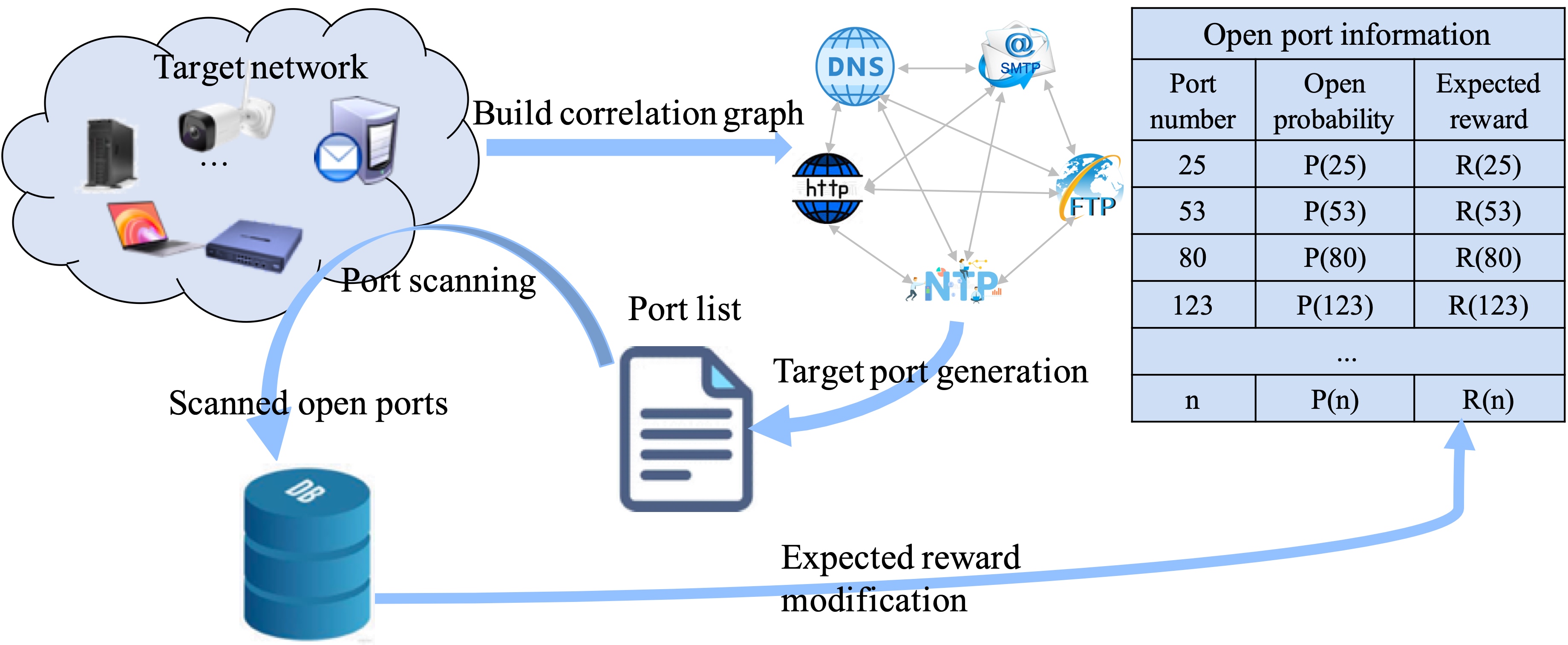 Which Doors Are Open: Reinforcement Learning-based Internet-wide Port ScanningGuanglei Song, Lin He#, Tianyun Zhao, Yirui Luo, Yichao Wu, Linna Fan, Chenglong Li, Zhiliang Wang, Jiahai YangIn Proceedings of the 31st IEEE/ACM International Symposium on Quality of Service (IWQoS 2023)
Which Doors Are Open: Reinforcement Learning-based Internet-wide Port ScanningGuanglei Song, Lin He#, Tianyun Zhao, Yirui Luo, Yichao Wu, Linna Fan, Chenglong Li, Zhiliang Wang, Jiahai YangIn Proceedings of the 31st IEEE/ACM International Symposium on Quality of Service (IWQoS 2023)
Orlando, FL, USA, June 19–21, 2023Internet MeasurementInternet-wide scanning is a commonly used research technique in various network surveys, such as measuring service deployment and security vulnerabilities. However, these network surveys are limited to the given port set, not comprehensively obtaining the real network landscape, and even misleading survey conclusions. In this work, we introduce PMap, a port scanning tool that efficiently discovers the majority of open ports from all 65K ports in the whole network. PMap uses the correlation of ports to build an open port correlation graph of each network, using a reinforcement learning framework to update the correlation graph based on feedback results and dynamically adjust the order of port scanning. Compared to current port scanning methods, PMap achieves better performance on hit rate, coverage, and intrusiveness. Our experiments over real-world networks show that PMap can find 90% open ports by only scanning 125 ports (90%@125) to each active address with 136× less than the state-of-the-art port probing methods. PMap reduces the number of scanned ports to decrease the intrusive nature of port scanning. PMap is the first effective practice for scanning open ports using reinforcement learning. It bridges the gap of existing scanning tools and effectively supports subsequent service discovery and security research.
@inproceedings{song2023pmap, title = {Which Doors Are Open: Reinforcement Learning-based Internet-wide Port Scanning}, author = {Song, Guanglei and He, Lin and Zhao, Tianyun and Luo, Yirui and Wu, Yichao and Fan, Linna and Li, Chenglong and Wang, Zhiliang and Yang, Jiahai}, booktitle = {Proceedings of the 31st IEEE/ACM International Symposium on Quality of Service (IWQoS 2023)}, year = {2023}, pages = {1-10}, doi = {10.1109/IWQoS57198.2023.10188692}, address = {Orlando, FL, USA}, date = {June 19–21}, } - IWQoS
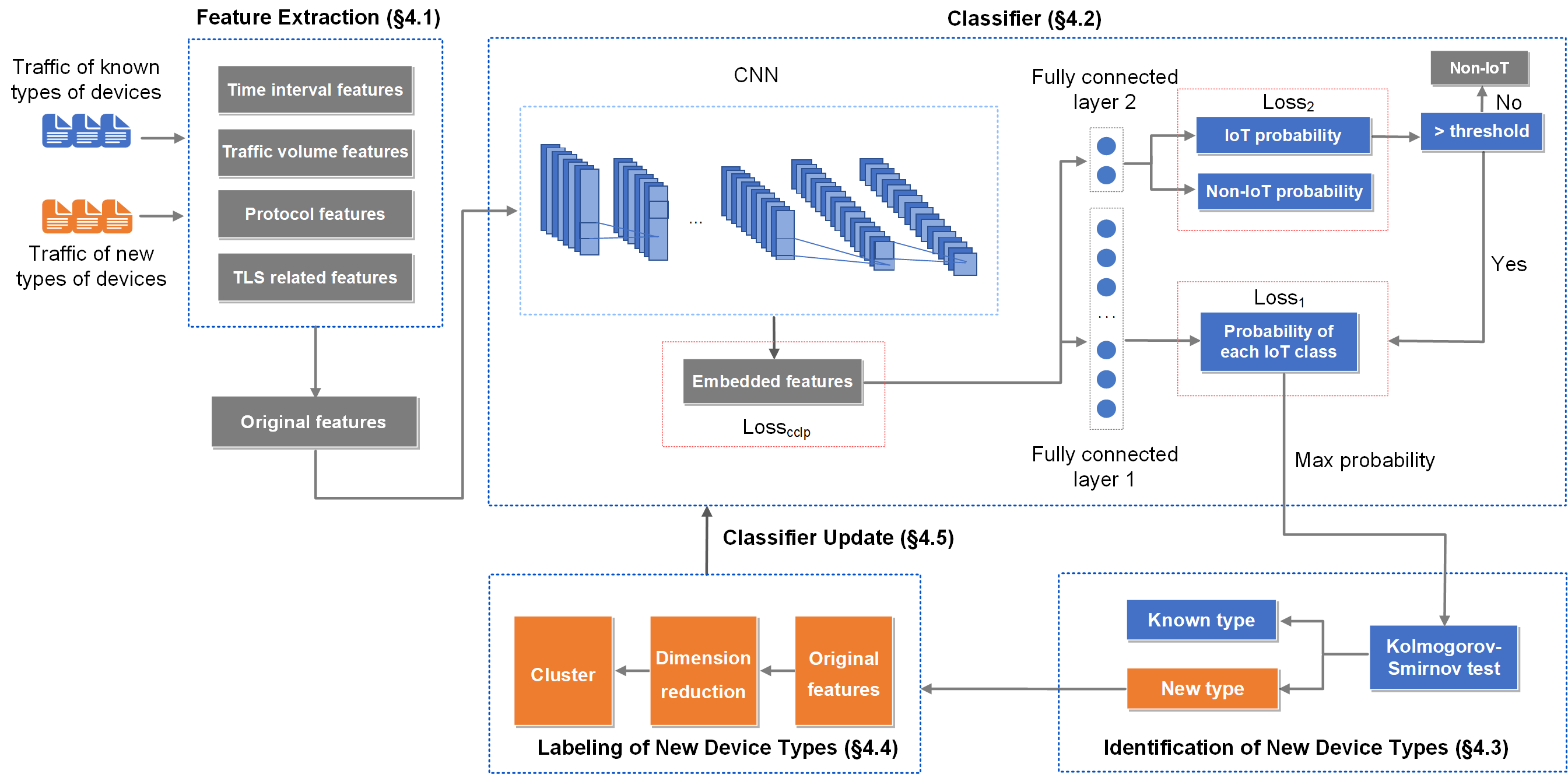
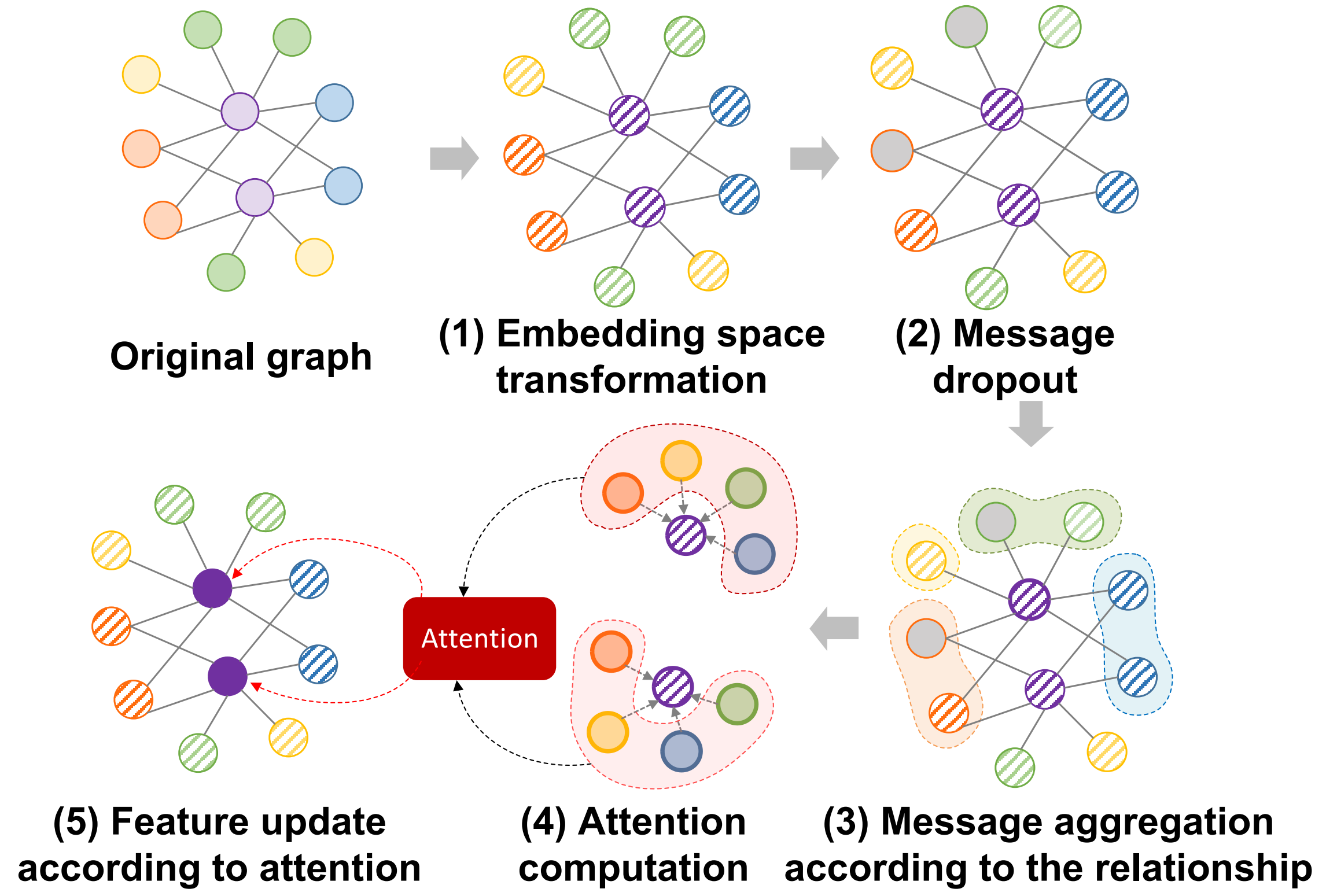 GraphIoT: Accurate IoT Identification based on Heterogeneous GraphLinna Fan, Lin He#, Xiaoqing Sun, Enhuan Dong, Jiahai Yang, Zhiliang Wang, Jinlei Lin, Guanglei SongIn Proceedings of the 31st IEEE/ACM International Symposium on Quality of Service (IWQoS 2023)
GraphIoT: Accurate IoT Identification based on Heterogeneous GraphLinna Fan, Lin He#, Xiaoqing Sun, Enhuan Dong, Jiahai Yang, Zhiliang Wang, Jinlei Lin, Guanglei SongIn Proceedings of the 31st IEEE/ACM International Symposium on Quality of Service (IWQoS 2023)
Orlando, FL, USA, June 19–21, 2023Network ManagementIoT devices deployed on campus and enterprise networks facilitate people’s lives and work. However, these devices also bring serious network asset management and security management problems. IoT device identification is the premise to solve these problems. Although current IoT identification methods can identify devices with relatively high accuracy in ideal environments, it is difficult to accurately identify devices in real-world complex environments (e.g., campus networks, enterprise networks). Therefore, we propose to use exact features. To solve the problem of different dimensions of exact features, we creatively model the IoT identification problem as a heterogeneous graph representation learning problem and design a new representation learning algorithm. We are the first to propose an approach to accurately identify IoT devices in real-world complex environments and solve this problem through heterogeneous graphs. The evaluation shows that GraphIoT’s macro F1 is on average 13.58% and 12.77% higher than the other methods on two public datasets.
@inproceedings{fan2023graphiot, title = {GraphIoT: Accurate IoT Identification based on Heterogeneous Graph}, author = {Fan, Linna and He, Lin and Sun, Xiaoqing and Dong, Enhuan and Yang, Jiahai and Wang, Zhiliang and Lin, Jinlei and Song, Guanglei}, booktitle = {Proceedings of the 31st IEEE/ACM International Symposium on Quality of Service (IWQoS 2023)}, year = {2023}, pages = {01-04}, doi = {10.1109/IWQoS57198.2023.10188710}, address = {Orlando, FL, USA}, date = {June 19–21}, }
2022
- USENIX ATC
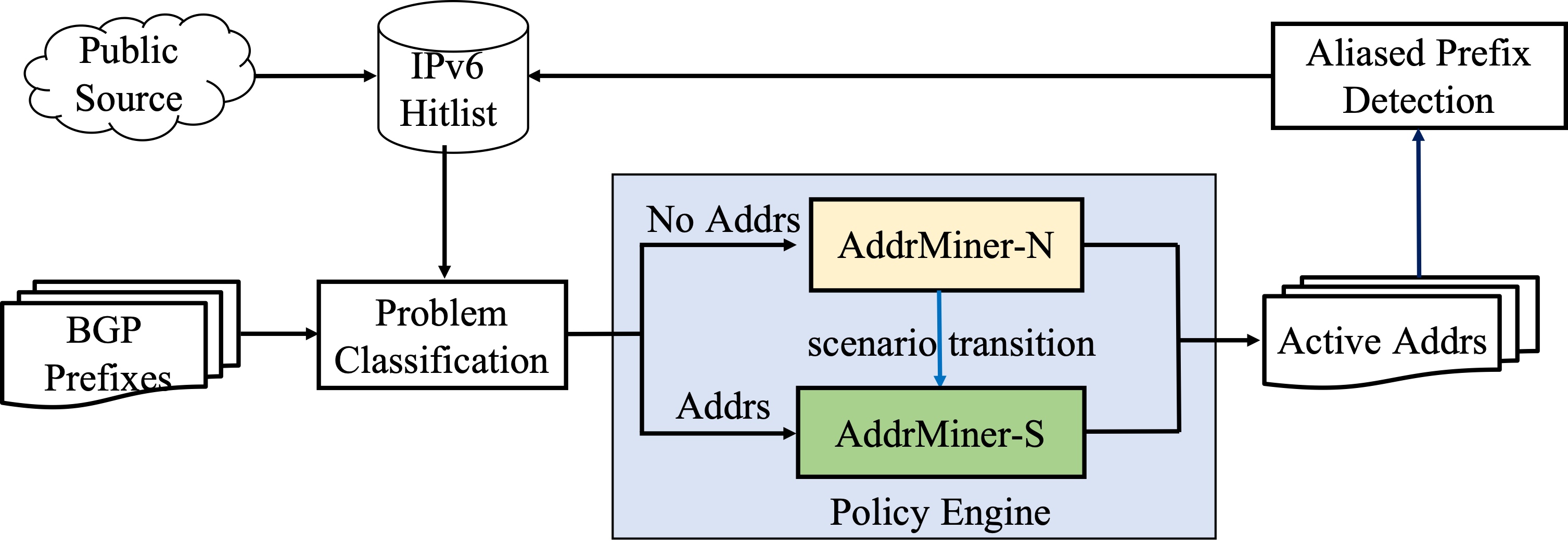
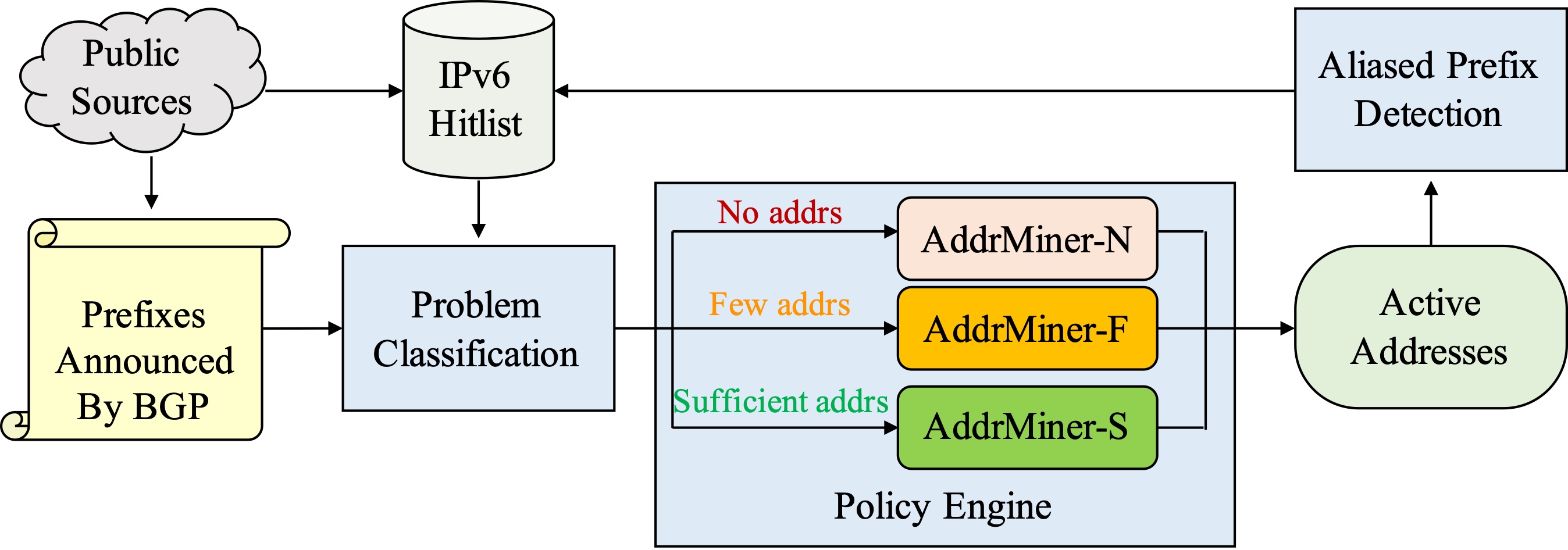 AddrMiner: A Comprehensive Global Active IPv6 Address Discovery SystemGuanglei Song, Jiahai Yang, Lin He#, Zhiliang Wang, Guo Li, Chenxin Duan, Yaozhong Liu, Zhongxiang SunIn Proceedings of the 2022 USENIX Annual Technical Conference (USENIX ATC 2022)
AddrMiner: A Comprehensive Global Active IPv6 Address Discovery SystemGuanglei Song, Jiahai Yang, Lin He#, Zhiliang Wang, Guo Li, Chenxin Duan, Yaozhong Liu, Zhongxiang SunIn Proceedings of the 2022 USENIX Annual Technical Conference (USENIX ATC 2022)
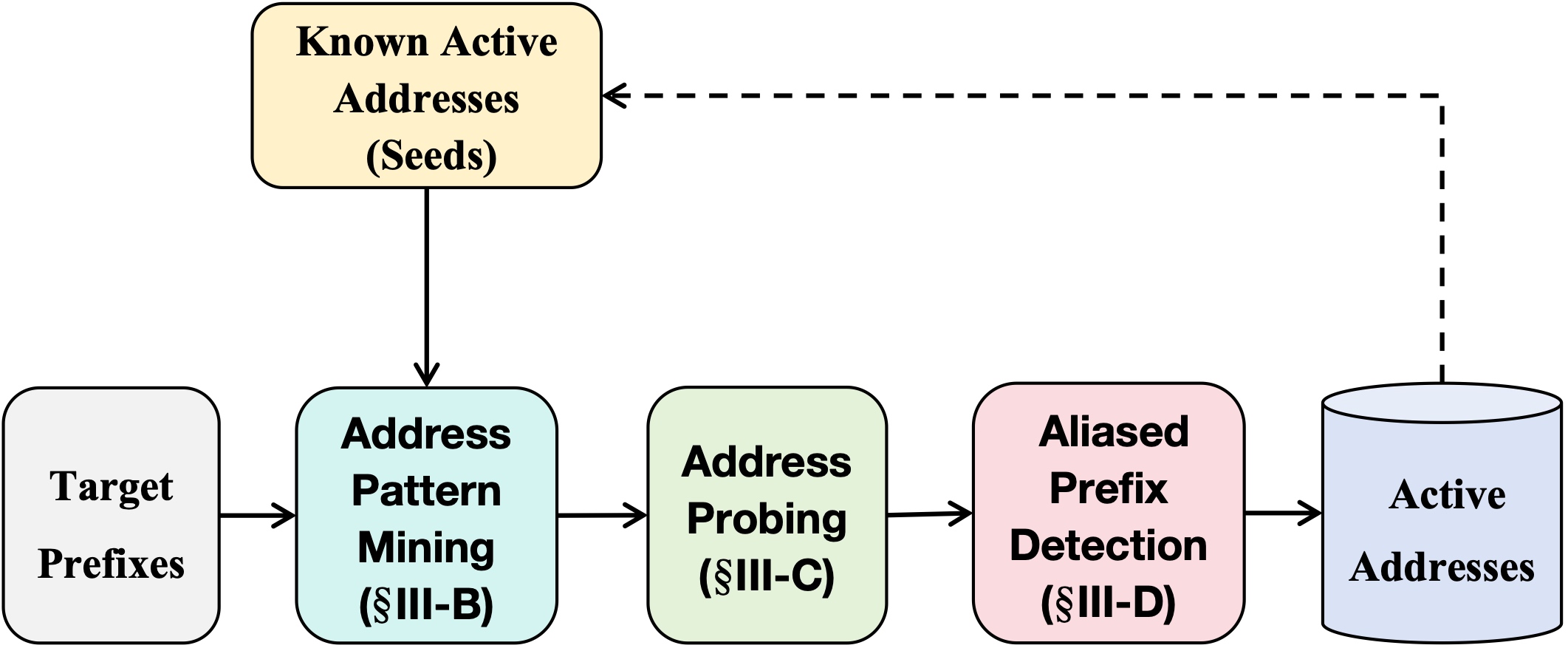
Carlsbad, CA, USA, July 11–13, 2022IPv6 Internet MeasurementFast Internet-wide scanning is essential for network situational awareness and asset evaluation. However, the vast IPv6 address space makes brute-force scanning infeasible. Although state-of-the-art techniques have made effective attempts, these methods do not work in seedless regions, while the detection efficiency is low in regions with seeds. Moreover, the constructed hitlists with low coverage cannot truly represent the active IPv6 address landscape of the Internet. This paper introduces AddrMiner, a global active IPv6 address probing system, making IPv6 active address probing systematic, comprehensive, and economical. We divide the IPv6 address space regions into three kinds according to the number of seed addresses and propose a probing algorithm for each of them. For the regions with no seeds, we propose AddrMiner-N, leveraging an organization association strategy to mine active addresses. It finds active addresses covering 86.4K BGP prefixes, accounting for 81.6% of the probed BGP prefixes. For the regions with few seeds, we propose AddrMiner-F, utilizing a similarity matching strategy to probe active addresses further. The hit rate of active address probing is improved by 70%-150% compared to existing algorithms. For the regions with sufficient seeds, we propose AddrMiner-S to generate target addresses based on reinforcement learning dynamically. It nearly doubles the hit rate compared to the state-of-the-art algorithms. Finally, we deploy AddrMiner and discover 2.1 billion active IPv6 addresses, including 1.7 billion de-aliased active addresses and 0.4 billion aliased addresses, through continuous probing for 13 months. We would like to further open the door of IPv6 measurement studies by publicly releasing AddrMiner and sharing our data.
@inproceedings{song2022addeminer, title = {AddrMiner: A Comprehensive Global Active IPv6 Address Discovery System}, author = {Song, Guanglei and Yang, Jiahai and He, Lin and Wang, Zhiliang and Li, Guo and Duan, Chenxin and Liu, Yaozhong and Sun, Zhongxiang}, booktitle = {Proceedings of the 2022 USENIX Annual Technical Conference (USENIX ATC 2022)}, year = {2022}, isbn = {978-1-939133-29-19}, address = {Carlsbad, CA, USA}, date = {July 11–13}, pages = {309--326}, url = {https://www.usenix.org/conference/atc22/presentation/song}, publisher = {USENIX Association}, } - USENIX ATC
 Firebolt: Finding Bugs in Programmable Data Plane GeneratorsIn Proceedings of the 2022 USENIX Annual Technical Conference (USENIX ATC 2022)
Firebolt: Finding Bugs in Programmable Data Plane GeneratorsIn Proceedings of the 2022 USENIX Annual Technical Conference (USENIX ATC 2022)
Carlsbad, CA, USA, July 11–13, 2022Programmable NetworksProgrammable data planes (DP) enable flexible customization of packet processing logic with domain-specific languages such as P4. To relieve developers from lengthy codes and tedious hardware details, many researches propose DP program generators that take high-level intents as input and automatically convert intents into DP programs. Generators must be correct, otherwise they may produce buggy programs or DP logic that is inconsistent with intents. Nevertheless, existing verification tools are designed to verify individual DP programs, not generators. They either cannot achieve high bug coverage or cannot debug generators with high scalability. This paper presents Firebolt, a blackbox testing tool designed to dig out faults in DP program generators, including security vulnerabilities, intent violations, and generator crash. Firebolt achieves high bug coverage by using syntax-guided intent generation to construct a comprehensive, syntactically correct, and semantically valid intent set. To avoid intent explosion, Firebolt designs an intent space pruning approach that eliminates redundant intents while preserving representative ones. For high scalability, Firebolt automatically formalizes DP programs and intents for verification. We apply Firebolt to three popular open-source DP generators. Evaluation results demonstrate that Firebolt can detect 2x bugs with 0.1% to 0.01% human efforts compared to existing tools.
@inproceedings{cao2022firebolt, title = {Firebolt: Finding Bugs in Programmable Data Plane Generators}, author = {Cao, Jiamin and Zhou, Yu and Sun, Chen and He, Lin and Xi, Zhaowei and Liu, Ying}, booktitle = {Proceedings of the 2022 USENIX Annual Technical Conference (USENIX ATC 2022)}, year = {2022}, isbn = {978-1-939133-29-32}, address = {Carlsbad, CA, USA}, date = {July 11–13}, pages = {819--834}, url = {https://www.usenix.org/conference/atc22/presentation/cao}, publisher = {USENIX Association}, } - GLOBECOM
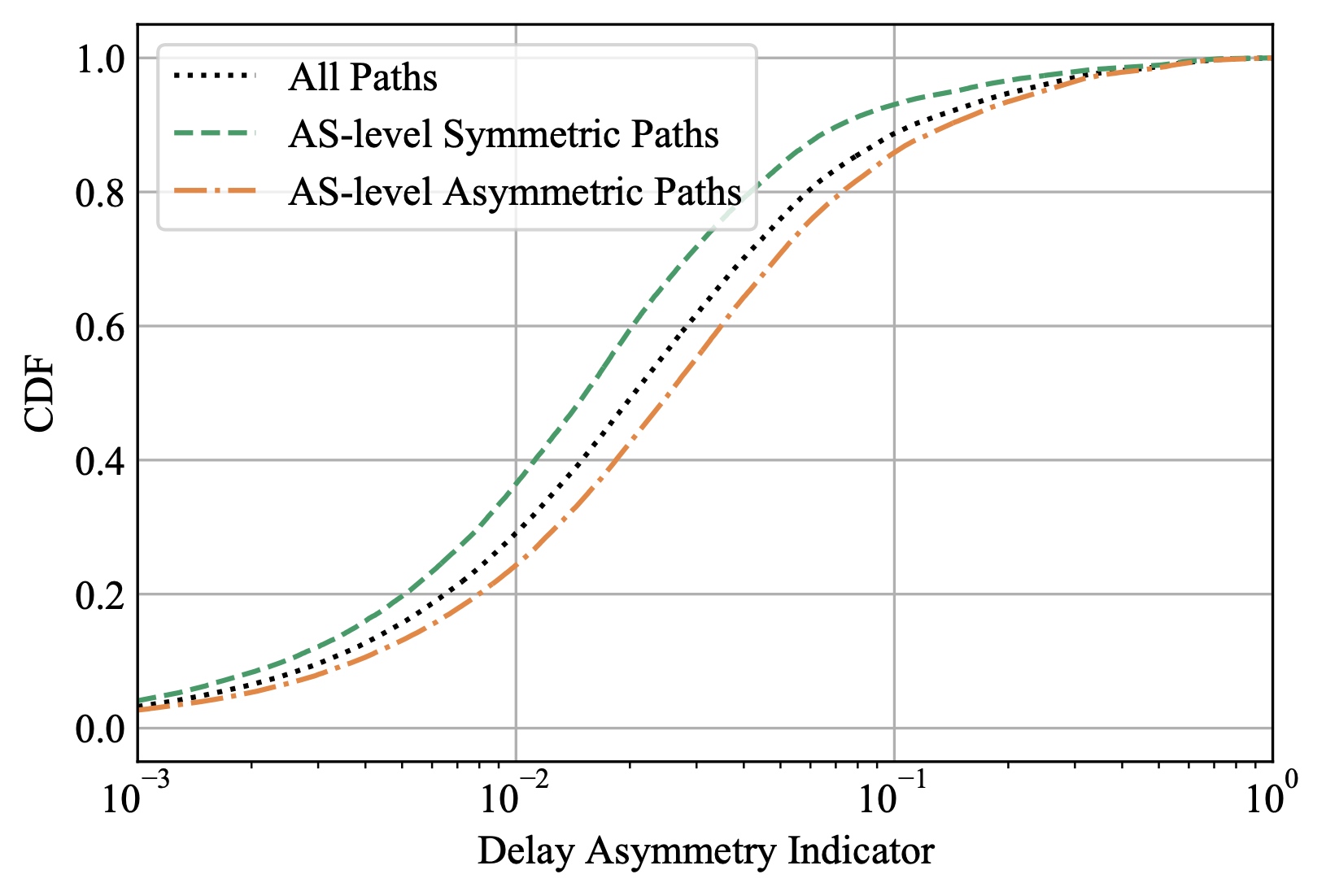 What Causes Delay Asymmetry: A Large-scale One-way Delay Measurement and Empirical StudyYaozhong Liu, Jiahai Yang, Zhiliang Wang, Long Pan, Lin He#, Jinlei Lin, Guanglei Song, Chenglong LiIn Proceedings of the 2022 IEEE Global Communications Conference (GLOBECOM 2022)
What Causes Delay Asymmetry: A Large-scale One-way Delay Measurement and Empirical StudyYaozhong Liu, Jiahai Yang, Zhiliang Wang, Long Pan, Lin He#, Jinlei Lin, Guanglei Song, Chenglong LiIn Proceedings of the 2022 IEEE Global Communications Conference (GLOBECOM 2022)
Rio de Janeiro, Brazil, December 4–8, 2022Internet MeasurementIn global communications, severe one-way delay (OWD) asymmetry often occurs. Due to the difficulties of OWD measurement (need to control both ends and synchronize their clocks), now RTT/2 is commonly used to estimate OWD. However, OWD asymmetry can lead to large errors in the halving RTT method, which in turn affects the end-to-end quality of service (QoS) guarantees. In this paper, we investigate OWD asymmetry through large-scale OWD measurements on a global scale. The measurements show that more than 11% of network paths have OWDs with a relative difference of more than 10% compared to RTT/2. By analyzing the measurement results in depth, we try to explain why the delay asymmetry occurs. We find that 67% is caused by hop inflation or a significant increase in propagation distance, and 33% is caused by variable queuing delays. We also find AS-level paths between node pairs with significant delay asymmetry are much more likely (∼ 10×) to violate the well-known valley-free rule.
@inproceedings{liu2022what, title = {What Causes Delay Asymmetry: A Large-scale One-way Delay Measurement and Empirical Study}, author = {Liu, Yaozhong and Yang, Jiahai and Wang, Zhiliang and Pan, Long and He, Lin and Lin, Jinlei and Song, Guanglei and Li, Chenglong}, booktitle = {Proceedings of the 2022 IEEE Global Communications Conference (GLOBECOM 2022)}, year = {2022}, pages = {6127-6132}, doi = {10.1109/GLOBECOM48099.2022.10000938}, address = {Rio de Janeiro, Brazil}, date = {December 4–8}, } - GLOBECOM
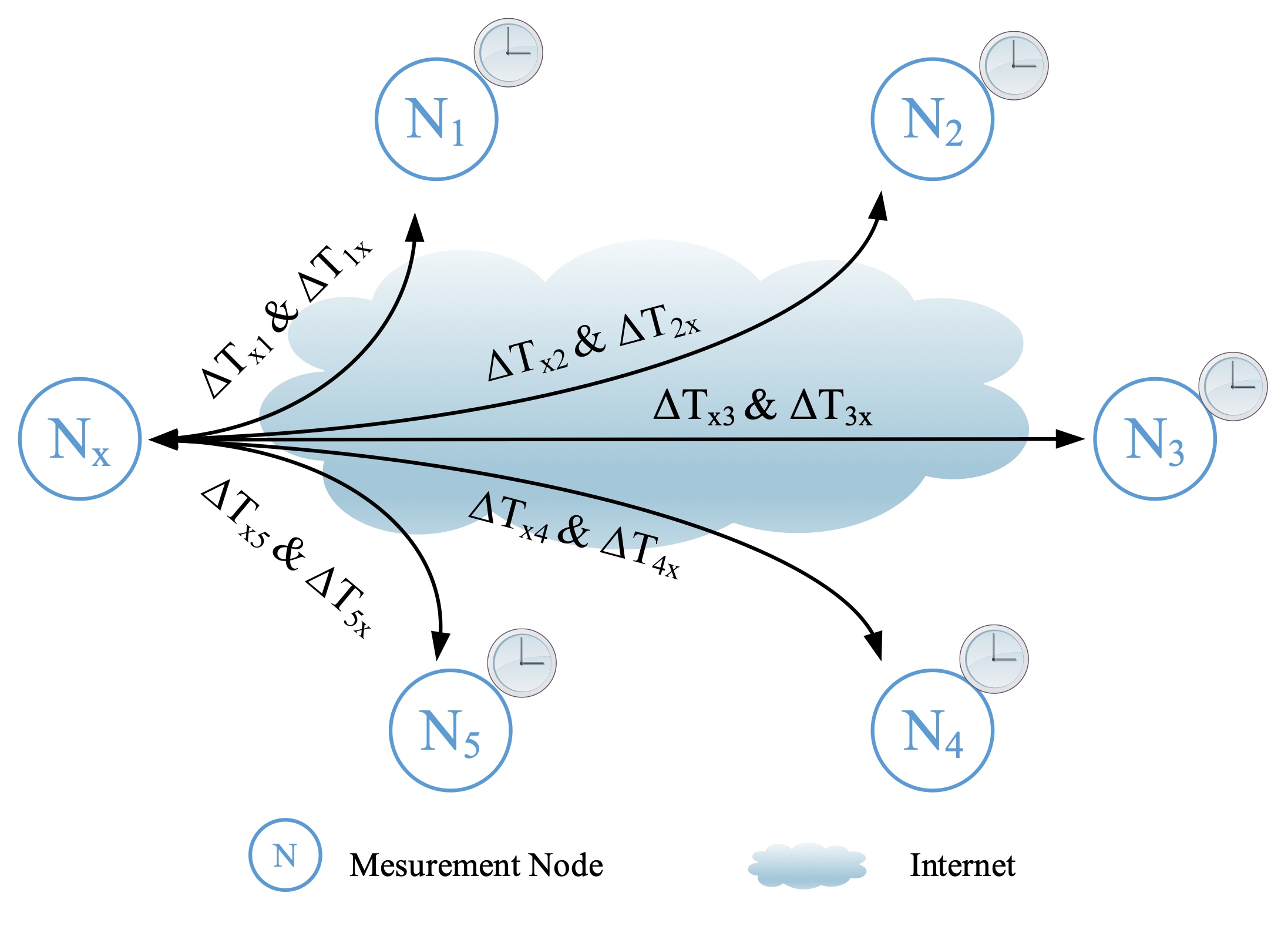 Both Efficient and Accurate: A Large-scale One-way Delay Measurement SchemeYaozhong Liu, Zhiliang Wang, Jiahai Yang, Long Pan, Lin He#, Jinlei Lin, Guanglei Song, Chenglong LiIn Proceedings of the 2022 IEEE Global Communications Conference (GLOBECOM 2022)
Both Efficient and Accurate: A Large-scale One-way Delay Measurement SchemeYaozhong Liu, Zhiliang Wang, Jiahai Yang, Long Pan, Lin He#, Jinlei Lin, Guanglei Song, Chenglong LiIn Proceedings of the 2022 IEEE Global Communications Conference (GLOBECOM 2022)
Rio de Janeiro, Brazil, December 4–8, 2022Internet MeasurementOne-way delay (OWD) is one of the essential network performance metrics. In large-scale resilient overlay networks (RONs), OWD measurements can be used for shortest path selection and troubleshooting. However, OWD measurements remain difficult because of the need for precise time synchronization. Especially in large-scale networks, clock synchronization of all nodes has always been a considerable challenge. Therefore, in many cases, people use half of the round-trip time (RTT/2) as a rough substitute for the OWD. This paper presents an efficient and easy-to-deploy scheme for large-scale OWD measurements with the algorithm ClockConverger at its core. The scheme consists of three steps: Firstly, we perform low-precision time synchronization for all the measured nodes relying on network time protocol daemons (ntpd); Then, we use the open-source tool OWPing to perform OWD measurements; Finally, we correct the errors of the measured OWDs with our proposed ClockConverger. The theory and experiments show that our scheme’s accuracy is significantly better than RTT/2. Meanwhile, the complexity of ClockConverger is O(n^2), which is much lower than the exponential complexity of the existing Maximum-Entropy algorithm.
@inproceedings{liu2022both, title = {Both Efficient and Accurate: A Large-scale One-way Delay Measurement Scheme}, author = {Liu, Yaozhong and Wang, Zhiliang and Yang, Jiahai and Pan, Long and He, Lin and Lin, Jinlei and Song, Guanglei and Li, Chenglong}, booktitle = {Proceedings of the 2022 IEEE Global Communications Conference (GLOBECOM 2022)}, year = {2022}, pages = {395-400}, doi = {10.1109/GLOBECOM48099.2022.10001552}, address = {Rio de Janeiro, Brazil}, date = {December 4–8}, } - CNSM
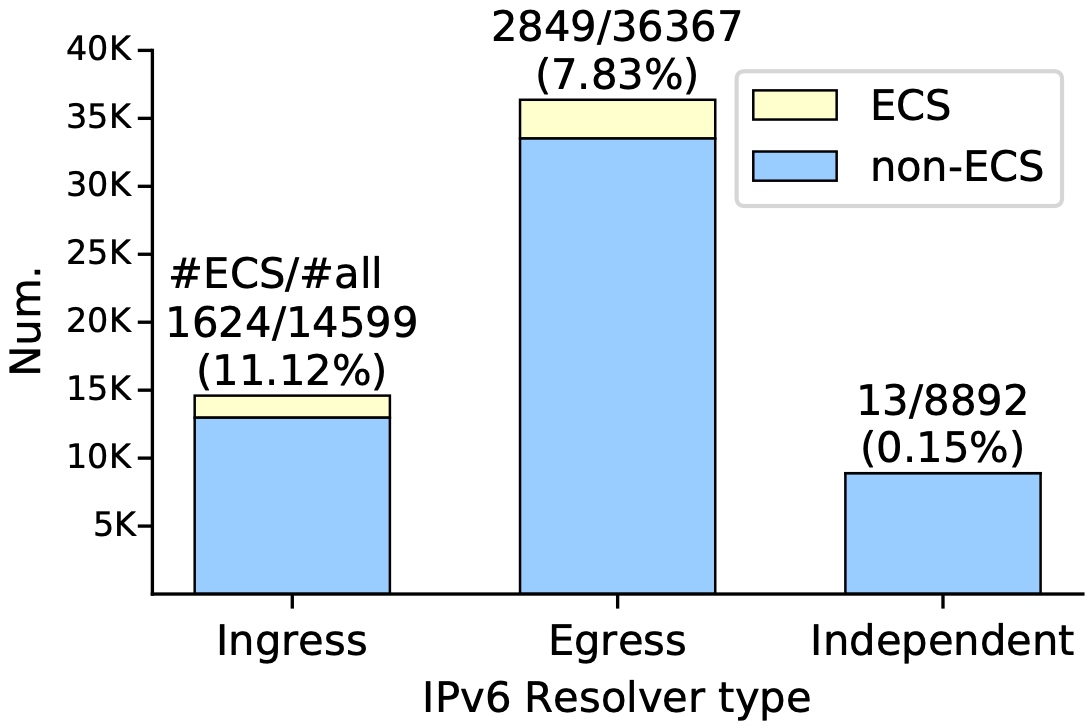 Towards a Behavioral and Privacy Analysis of ECS for IPv6 DNS ResolversIn Proceedings of 18th IEEE Conference on Network and Service Management (CNSM 2022)
Towards a Behavioral and Privacy Analysis of ECS for IPv6 DNS ResolversIn Proceedings of 18th IEEE Conference on Network and Service Management (CNSM 2022)
Thessaloniki, Greece, October 31 - November 4, 2022IPv6 Internet MeasurementThe Domain Name System (DNS) is critical to Internet communications. EDNS Client Subnet (ECS), a DNS extension, allows recursive resolvers to include client subnet information in DNS queries to improve end-user mapping, extending the visibility of client information to a broader range. Major content delivery network (CDN) vendors, content providers (CP), and public DNS service providers (PDNS) are accelerating their IPv6 infrastructure development. With the increasing deployment of IPv6-enabled services and DNS being the most foundational system of the Internet, it becomes important to analyze the behavioral and privacy status of IPv6 resolvers. However, there is a lack of research on ECS for IPv6 DNS resolvers. In this paper, we study the ECS deployment and compliance status of IPv6 resolvers. Our measurement shows that 11.12% IPv6 open resolvers implement ECS. We discuss abnormal non-compliant scenarios that exist in both IPv6 and IPv4 that raise privacy and performance issues. Additionally, we measured if the sacrifice of clients’ privacy can enhance IPv6 CDN performance. We find that in some cases ECS helps end-user mapping but with an unnecessary privacy loss. And even worse, the exposure of client address information can sometimes backfire, which deserves attention from both Internet users and PDNSes.
@inproceedings{nie2022towards, title = {Towards a Behavioral and Privacy Analysis of ECS for IPv6 DNS Resolvers}, author = {Nie, Leyao and He, Lin and Song, Guanglei and Gao, Hao and Li, Chenglong and Wang, Zhiliang and Yang, Jiahai}, booktitle = {Proceedings of 18th IEEE Conference on Network and Service Management (CNSM 2022)}, year = {2022}, pages = {303-309}, doi = {10.23919/CNSM55787.2022.9965032}, address = {Thessaloniki, Greece}, date = {October 31 - November 4}, } - CNSM
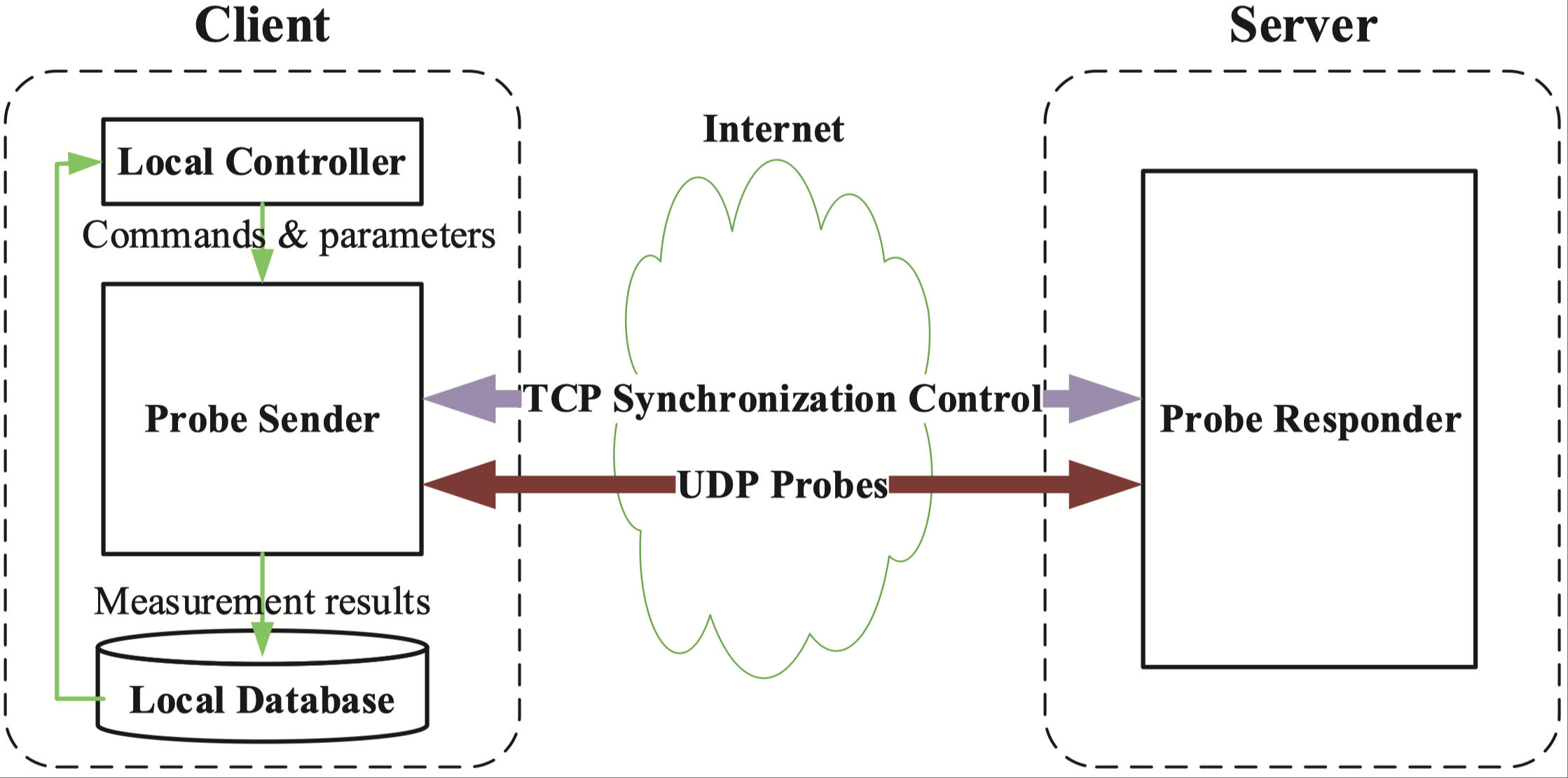 PerfTrace: A New Multi-metric Network Performance Monitoring ToolIn Proceedings of 18th IEEE Conference on Network and Service Management (CNSM 2022)
PerfTrace: A New Multi-metric Network Performance Monitoring ToolIn Proceedings of 18th IEEE Conference on Network and Service Management (CNSM 2022)
Thessaloniki, Greece, October 31 - November 4, 2022Internet MeasurementWe present PerfTrace, an end-to-end tool for efficient, real-time, multi-metric network performance monitoring. PerfTrace provides a high integration of different existing measurement functions, supporting the measurement of essential metrics such as latency, jitter, packet loss, and available bandwidth. More importantly, innovative schemes and algorithms are proposed to address the weaknesses of existing tools. We evaluate PerfTrace on the Internet and our testbed, respectively. We find that (i) PerfTrace measures one-way and two-way latency, jitter, and packet loss ∼9.4× faster and ∼3.6× more data-efficiently; (ii) PerfTrace measures available bandwidth in our testbed with minimal mean relative error (5.22%), outperforming all the tools compared (ranging from 8.17% to 37.24%); (iii) PerfTrace measures available bandwidth with better accuracy and adaptability in different real-world network environments. Meanwhile, PerfTrace consumes a more constant percentage of bandwidth resources than other tools when monitoring available bandwidth. PerfTrace’s data overhead is always only about 1/600 of the total bandwidth for a measurement frequency once per minute.
@inproceedings{liu2022perftrace, title = {PerfTrace: A New Multi-metric Network Performance Monitoring Tool}, author = {Liu, Yaozhong and Pan, Long and Li, Chenglong and He, Lin and Luo, Yirui and Song, Guanglei and Yang, Jiahai and Wang, Zhiliang}, booktitle = {Proceedings of 18th IEEE Conference on Network and Service Management (CNSM 2022)}, year = {2022}, pages = {240-246}, doi = {10.23919/CNSM55787.2022.9964543}, address = {Thessaloniki, Greece}, date = {October 31 - November 4}, }
2021
- IWQoS
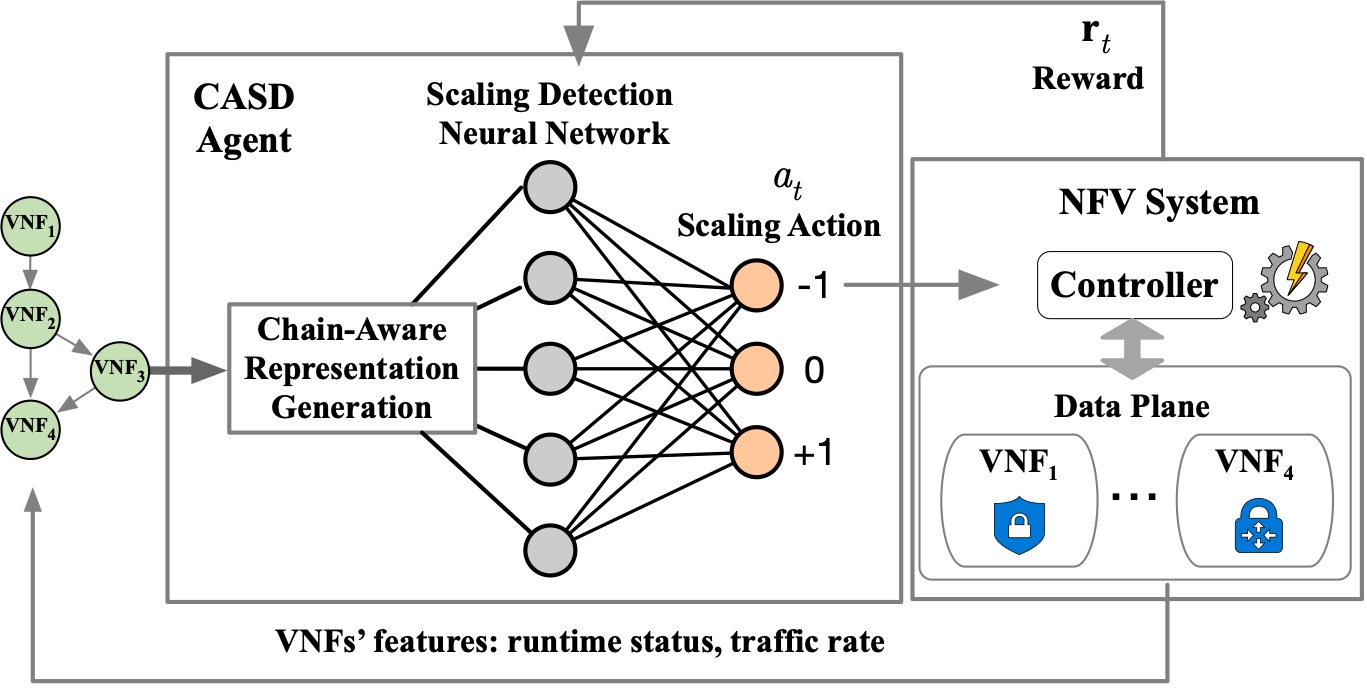 Towards Chain-Aware Scaling Detection in NFV with Reinforcement LearningLin He, Lishan Li, Ying LiuIn Proceedings of the 29th IEEE/ACM International Symposium on Quality of Service (IWQoS 2021)
Towards Chain-Aware Scaling Detection in NFV with Reinforcement LearningLin He, Lishan Li, Ying LiuIn Proceedings of the 29th IEEE/ACM International Symposium on Quality of Service (IWQoS 2021)
Virtual, June 25-28, 2021Programmable NetworksElastic scaling enables dynamic and efficient re-source provisioning in Network Function Virtualization (NFV) to serve fluctuating network traffic. Scaling detection determines the appropriate time when a virtual network function (VNF) needs to be scaled, and its precision and agility profoundly affect system performance. Previous heuristics define fixed control rules based on a simplified or inaccurate understanding of deployment environments and workloads. Therefore, they fail to achieve optimal performance across a broad set of network conditions.In this paper, we propose a chain-aware scaling detection mechanism, namely CASD, which learns policies directly from experience using reinforcement learning (RL) techniques. Furthermore, CASD incorporates chain information into control policies to efficiently plan the scaling sequence of VNFs within a service function chain. This paper makes the following two key technical contributions. Firstly, we develop chain-aware representations, which embed global chains of arbitrary sizes and shapes into a set of embedding vectors based on graph embedding techniques. Secondly, we design an RL-based neural network model to make scaling decisions based on chain-aware representations. We implement a prototype of CASD, and its evaluation results demonstrate that CASD reduces the overall system cost and improves system performance over other baseline algorithms across different workloads and chains.
@inproceedings{he2021towards, title = {Towards Chain-Aware Scaling Detection in NFV with Reinforcement Learning}, author = {He, Lin and Li, Lishan and Liu, Ying}, booktitle = {Proceedings of the 29th IEEE/ACM International Symposium on Quality of Service (IWQoS 2021)}, year = {2021}, pages = {1-10}, doi = {10.1109/IWQOS52092.2021.9521362}, address = {Virtual}, date = {June 25-28}, } - IWQoS
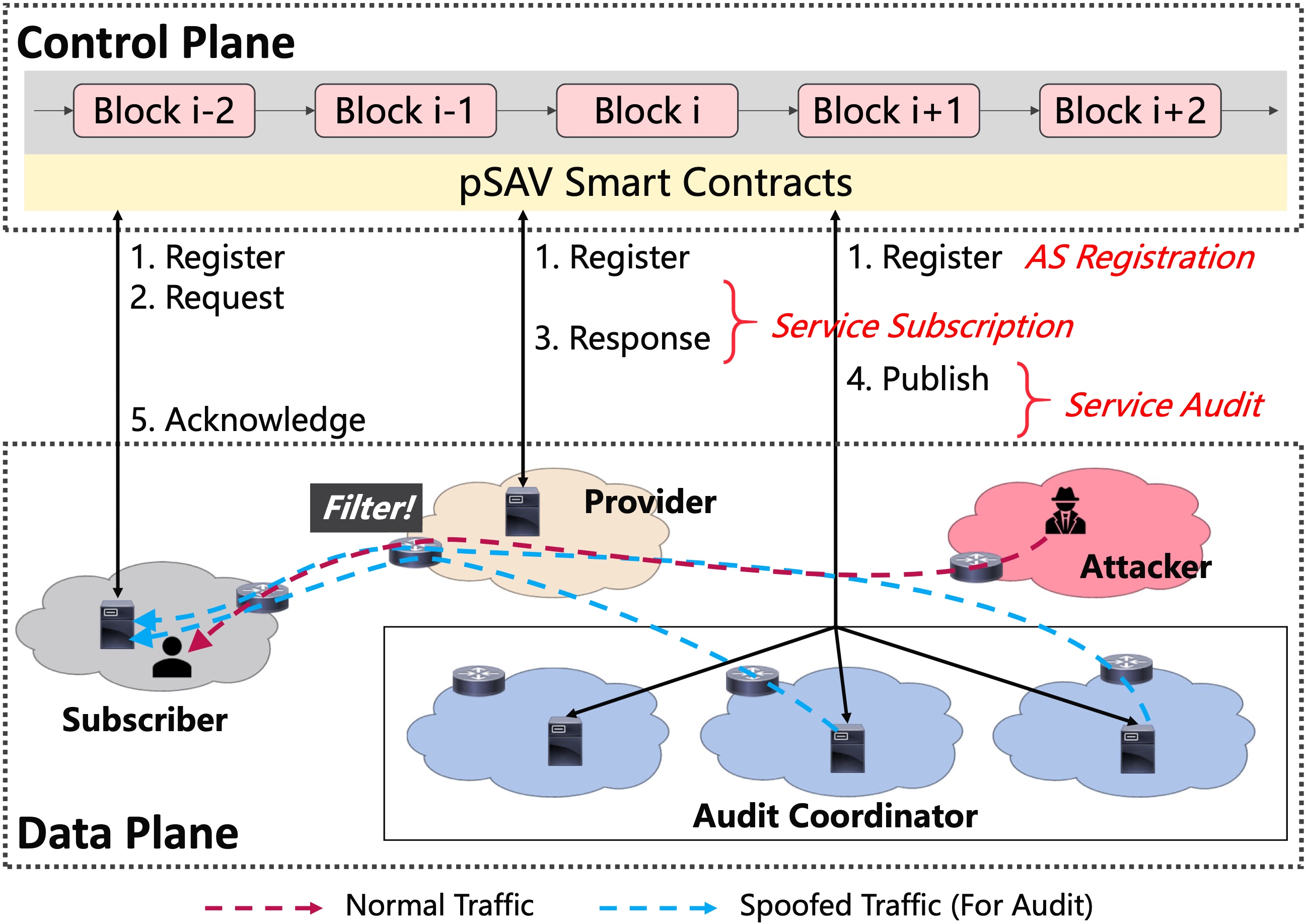 pSAV: A Practical and Decentralized Inter-AS Source Address Validation Service FrameworkJiamin Cao, Ying Liu, Mingxing Liu, Lin He#, Yihao Jia, Fei YangIn Proceedings of the 29th IEEE/ACM International Symposium on Quality of Service (IWQoS 2021)
pSAV: A Practical and Decentralized Inter-AS Source Address Validation Service FrameworkJiamin Cao, Ying Liu, Mingxing Liu, Lin He#, Yihao Jia, Fei YangIn Proceedings of the 29th IEEE/ACM International Symposium on Quality of Service (IWQoS 2021)
Virtual, June 25-28, 2021Network Architecture Protocol DesignSource IP address spoofing has been a major vulnerability of the Internet for many years. Although much work has been done to study the problem extensively, spoofing continues to occur frequently and has led to many serious network attacks. Inter-AS source address validation (SAV) is considered an important defense method for AS to filter spoofed packets. However, existing work has been unable to drive inter-AS SAV deployment into practice due to the lack of deployment incentives and trust foundation.In this paper, we propose a practical and decentralized inter-AS SAV service framework, pSAV, to promote inter-AS SAV deployment. pSAV increases deployment incentives by treating SAV as a payable service and dividing the participant ASes into service subscribers, providers, and auditors. On the control plane, pSAV leverages blockchain as a trust foundation to provide service subscriptions and audits with automatic incentive allocation. On the data plane, pSAV leverages P4-programmable switches to provide flexible and high-performance SAV services. We prototype the pSAV control plane based on Hyperledger Fabric and implement various SAV techniques on Barefoot Tofino switches. The evaluation results show that (1) on the control plane, pSAV blockchain can provide high-performance service transactions (hundreds of transactions per second with second latency), and (2) on the data plane, pSAV can provide various high-throughput (hundreds of Gbps) SAV services using only one programmable switch.
@inproceedings{cao2021psav, title = {pSAV: A Practical and Decentralized Inter-AS Source Address Validation Service Framework}, author = {Cao, Jiamin and Liu, Ying and Liu, Mingxing and He, Lin and Jia, Yihao and Yang, Fei}, booktitle = {Proceedings of the 29th IEEE/ACM International Symposium on Quality of Service (IWQoS 2021)}, year = {2021}, pages = {1-7}, doi = {10.1109/IWQOS52092.2021.9521336}, address = {Virtual}, date = {June 25-28}, } - ISSRE
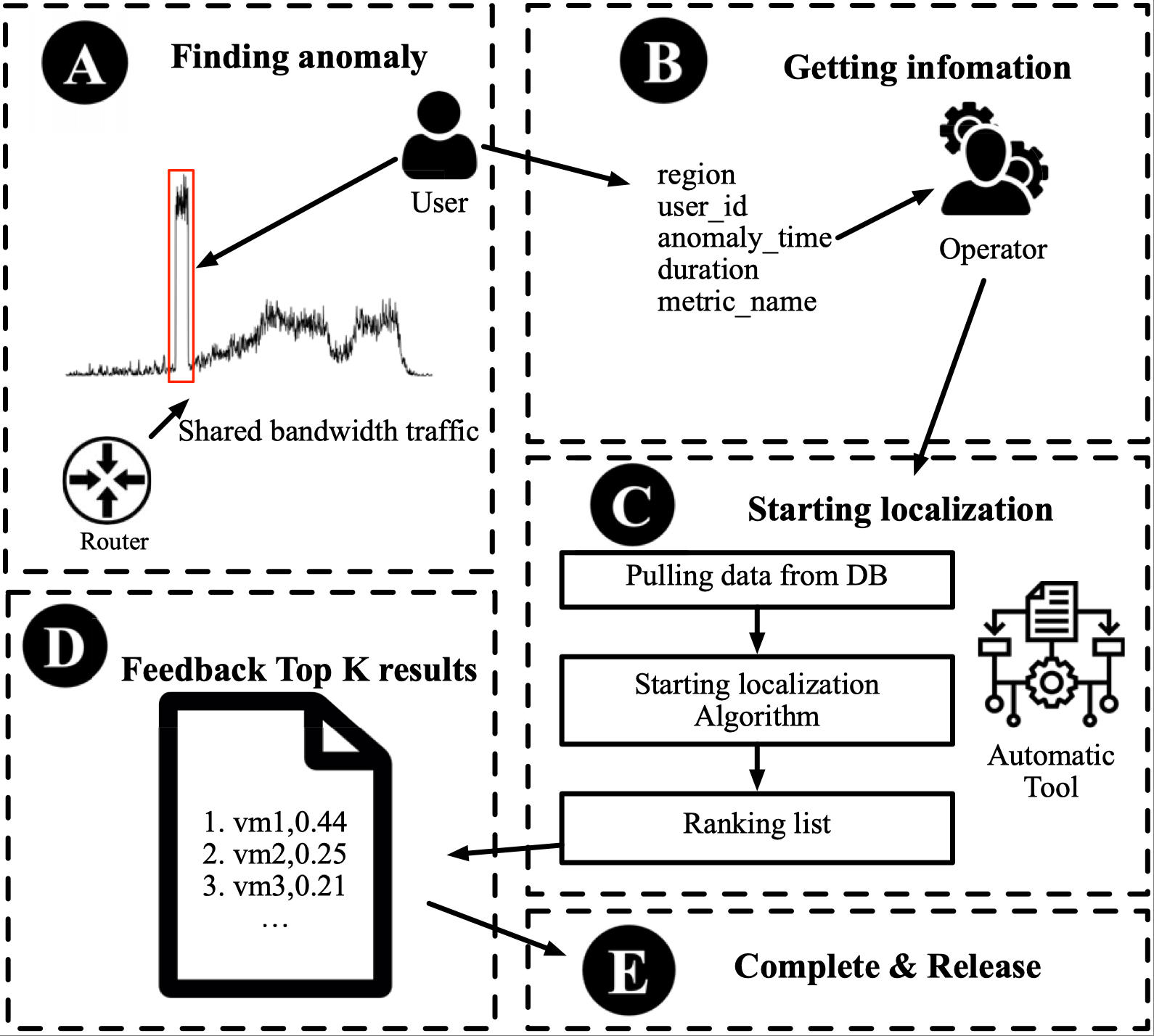 CloudPin: A Root Cause Localization Framework of Shared Bandwidth Package Traffic Anomalies in Public Cloud NetworksShize Zhang, Yunfeng Zhao, Jianyuan Lu, Biao Lyu, Shunmin Zhu, Zhiliang Wang, Jiahai Yang, Lin He, Jianping WuIn Proceedings of the 32nd IEEE International Symposium on Software Reliability Engineering (ISSRE 2021)
CloudPin: A Root Cause Localization Framework of Shared Bandwidth Package Traffic Anomalies in Public Cloud NetworksShize Zhang, Yunfeng Zhao, Jianyuan Lu, Biao Lyu, Shunmin Zhu, Zhiliang Wang, Jiahai Yang, Lin He, Jianping WuIn Proceedings of the 32nd IEEE International Symposium on Software Reliability Engineering (ISSRE 2021)
Wuhan, China, October 25-28, 2021Network ManagementDue to the sharing nature of public cloud, most of the cloud services use a sharing bandwidth package (sBwp) model to conduct inbound/outbound communication. The sBwp model allows users to purchase a sharing bandwidth for plenty of virtual machines instead of purchasing bandwidth for each virtual machine separately. The advantage of sBwp is that it can provide users with convenient configuration and lower economic cost. However, the sBwp model brings new challenges for operators to localize the root cause of traffic anomalies of a sharing bandwidth, especially for a globally distributed large-scale public cloud with millions of users. In this paper, we first formalize the sBwp problem on the cloud and propose CloudPin, a root cause localization framework for this problem. Our framework solves all the challenges by employing a multi-dimensional algorithm with three sub-models of prediction deviation, anomaly amplitude, and shape similarity, and an overall ranking algorithm. Evaluations on real-world data, from one of the world-renowned public cloud vendors, show that our algorithm precision reaches 97.8% for the top 1 of the ranking list, outperforming multiple baseline algorithms.
@inproceedings{zhang2021cloudpin, title = {CloudPin: A Root Cause Localization Framework of Shared Bandwidth Package Traffic Anomalies in Public Cloud Networks}, author = {Zhang, Shize and Zhao, Yunfeng and Lu, Jianyuan and Lyu, Biao and Zhu, Shunmin and Wang, Zhiliang and Yang, Jiahai and He, Lin and Wu, Jianping}, booktitle = {Proceedings of the 32nd IEEE International Symposium on Software Reliability Engineering (ISSRE 2021)}, year = {2021}, pages = {367-377}, doi = {10.1109/ISSRE52982.2021.00046}, address = {Wuhan, China}, date = {October 25-28}, } - ICC
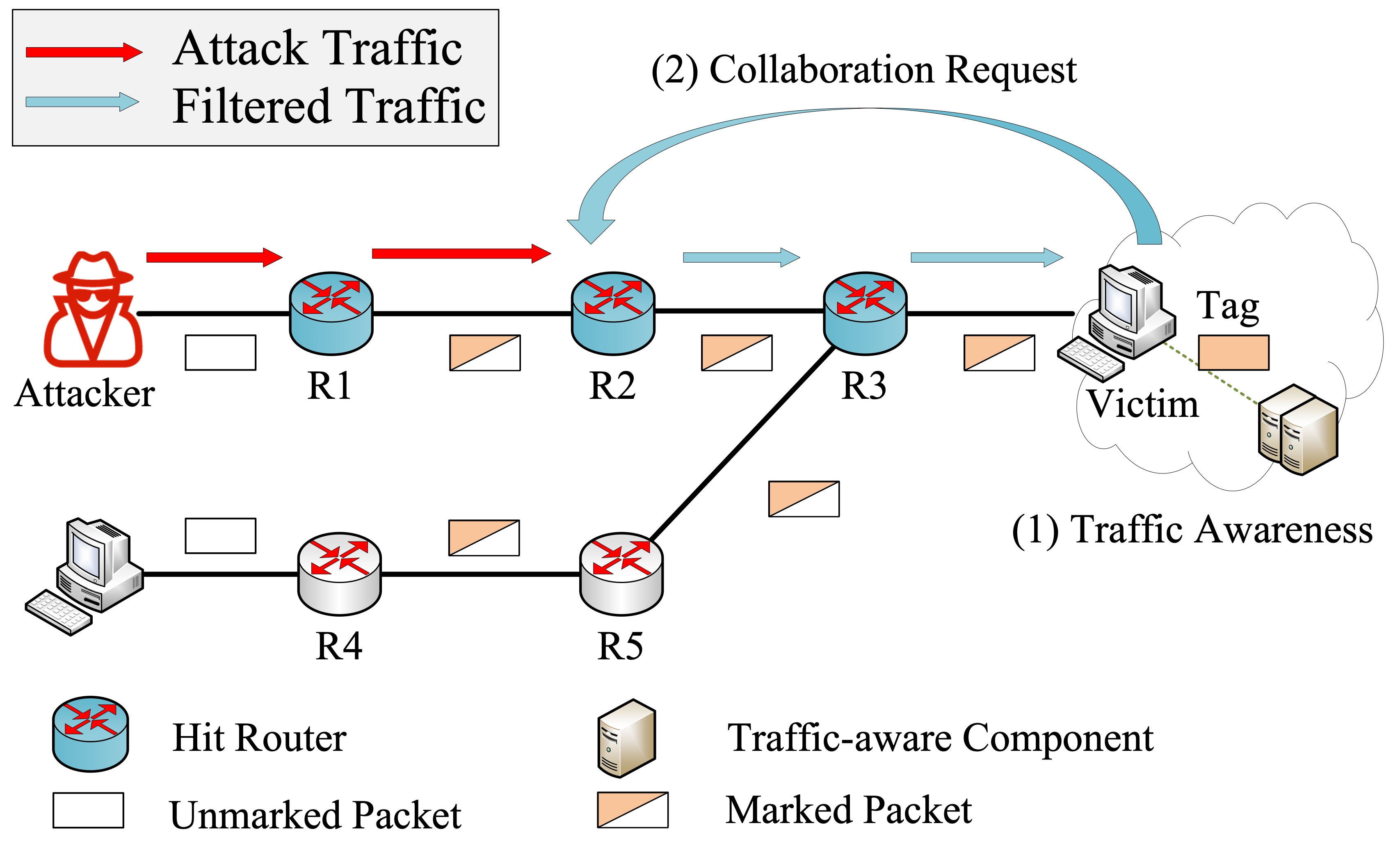
 Deception Maze: A Stackelberg Game-Theoretic Defense Mechanism for Intranet ThreatsJieling Liu, Zhiliang Wang, Jiahai Yang, Bo Wang, Lin He, Guanglei Song, Xinran LiuIn Proceedings of the 2021 IEEE International Conference on Communications (ICC 2021)
Deception Maze: A Stackelberg Game-Theoretic Defense Mechanism for Intranet ThreatsJieling Liu, Zhiliang Wang, Jiahai Yang, Bo Wang, Lin He, Guanglei Song, Xinran LiuIn Proceedings of the 2021 IEEE International Conference on Communications (ICC 2021)
Virtual, June 14-23, 2021The intranets in modern organizations are facing severe data breaches and critical resource misuses. By reusing user credentials from compromised systems, Advanced Persistent Threat (APT) attackers can move laterally within the internal network. A promising new approach called deception technology makes the network administrator (i.e., defender) able to deploy decoys to deceive the attacker in the intranet and trap him into a honeypot. Then the defender ought to reasonably allocate decoys to potentially insecure hosts. Unfortunately, existing APT-related defense resource allocation models are infeasible because of the neglect of many realistic factors.In this paper, we make the decoy deployment strategy feasible by proposing a game-theoretic model called the APT Deception Game to describe interactions between the defender and the attacker. More specifically, we decompose the decoy deployment problem into two subproblems and make the problem solvable. Considering the best response of the attacker who is aware of the defender’s deployment strategy, we provide an elitist reservation genetic algorithm to solve this game. Simulation results demonstrate the effectiveness of our deployment strategy compared with other heuristic strategies.
@inproceedings{liu2021deception, title = {Deception Maze: A Stackelberg Game-Theoretic Defense Mechanism for Intranet Threats}, author = {Liu, Jieling and Wang, Zhiliang and Yang, Jiahai and Wang, Bo and He, Lin and Song, Guanglei and Liu, Xinran}, booktitle = {Proceedings of the 2021 IEEE International Conference on Communications (ICC 2021)}, year = {2021}, pages = {1-6}, doi = {10.1109/ICC42927.2021.9500765}, address = {Virtual}, date = {June 14-23}, } - MSN
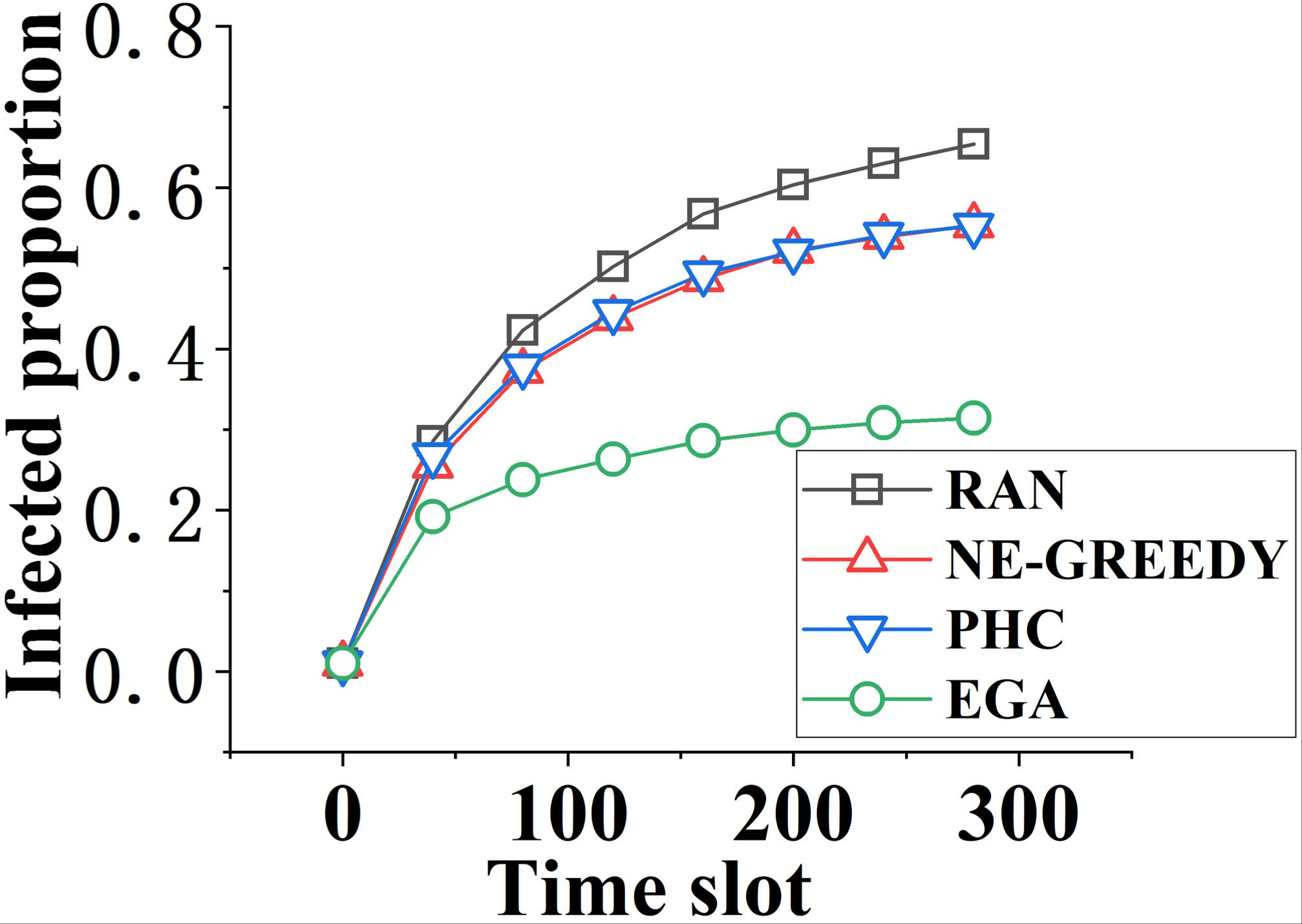
 TAP: A Traffic-Aware Probabilistic Packet Marking for Collaborative DDoS MitigationIn Proceedings of the 17th International Conference on Mobility, Sensing and Networking (MSN 2021)
TAP: A Traffic-Aware Probabilistic Packet Marking for Collaborative DDoS MitigationIn Proceedings of the 17th International Conference on Mobility, Sensing and Networking (MSN 2021)
Exeter, UK, December 13-15, 2021Network Architecture Protocol DesignIn recent years, Distributed Denial-of-Service (DDoS) attacks have become more rampant and continue to be one of the most serious security threats facing network infrastructure. In a classic DDoS attack, the attacker controls numerous bots from many sources to send a significant volume of traffic to flood the victim end or the bottleneck link. In practical networks, it is inefficient and costly to request all partner routers to collaboratively mitigate DDoS attacks. The common feature of DDoS attacks is the abnormal distribution of traffic to the victim. In this paper, we propose TAP, a collaborative DDoS mitigation framework, based on traffic-aware probabilistic packet marking (PPM). TAP enables the victim to select a few hit routers as collaborators to mitigate attack traffic efficiently depending on the traffic distribution. Our evaluation results show that TAP greatly reduces attack traffic within seconds and mitigate the damage caused by DDoS with less overhead, which demonstrates that TAP is an effective, efficient, and rapid-response scheme for collaborative DDoS mitigation.
@inproceedings{liu2021tap, title = {TAP: A Traffic-Aware Probabilistic Packet Marking for Collaborative DDoS Mitigation}, author = {Liu, Mingxing and Liu, Ying and Xu, Ke and He, Lin and Wang, Xiaoliang and Guo, Yangfei and Jiang, Weiyu}, booktitle = {Proceedings of the 17th International Conference on Mobility, Sensing and Networking (MSN 2021)}, year = {2021}, pages = {470-478}, doi = {10.1109/MSN53354.2021.00076}, address = {Exeter, UK}, date = {December 13-15}, }
2020
- IWQoS
 Towards the Construction of Global IPv6 Hitlist and Efficient Probing of IPv6 Address SpaceGuanglei Song, Lin He, Zhiliang Wang, Jiahai Yang, Tao Jin, Jieling Liu, Guo LiIn Proceedings of the 28th IEEE/ACM 28th International Symposium on Quality of Service (IWQoS 2020)
Towards the Construction of Global IPv6 Hitlist and Efficient Probing of IPv6 Address SpaceGuanglei Song, Lin He, Zhiliang Wang, Jiahai Yang, Tao Jin, Jieling Liu, Guo LiIn Proceedings of the 28th IEEE/ACM 28th International Symposium on Quality of Service (IWQoS 2020)
Virtual, June 15-17, 2020IPv6 Internet MeasurementFast IPv4 scanning has made sufficient progress in network measurement and security research. However, it is infeasible to perform brute-force scanning of the IPv6 address space. We can find active IPv6 addresses through scanning candidate addresses generated by the state-of-the-art algorithms, whose probing efficiency of active IPv6 addresses, however, is still very low. In this paper, we aim to improve the probing efficiency of IPv6 addresses in two ways. Firstly, we perform a longitudinal active measurement study over four months, building a high-quality dataset called hitlist with more than 1.3 billion IPv6 addresses distributed in 45.2k BGP prefixes. Different from previous work, we probe the announced BGP prefixes using a pattern-based algorithm, which makes our dataset overcome the problems of uneven address distribution and low active rate. Secondly, we propose an efficient address generation algorithm DET, which builds a density space tree to learn high-density address regions of the seed addresses in linear time and improves the probing efficiency of active addresses. On the public hitlist and our hitlist, we compare our algorithm DET against state-of-the-art algorithms and find that DET increases the de-aliased active address ratio by 10%, and active address (including aliased addresses) ratio by 14%, by scanning 50 million addresses.
@inproceedings{song2020towards, title = {Towards the Construction of Global IPv6 Hitlist and Efficient Probing of IPv6 Address Space}, author = {Song, Guanglei and He, Lin and Wang, Zhiliang and Yang, Jiahai and Jin, Tao and Liu, Jieling and Li, Guo}, booktitle = {Proceedings of the 28th IEEE/ACM 28th International Symposium on Quality of Service (IWQoS 2020)}, year = {2020}, pages = {1-10}, doi = {10.1109/IWQoS49365.2020.9212980}, address = {Virtual}, date = {June 15-17}, } - ICC
 P4DAD: Securing Duplicate Address Detection Using P4Peng Kuang, Ying Liu, Lin He#In Proceedings of the 2020 IEEE International Conference on Communications (ICC 2020)
P4DAD: Securing Duplicate Address Detection Using P4Peng Kuang, Ying Liu, Lin He#In Proceedings of the 2020 IEEE International Conference on Communications (ICC 2020)
Virtual, June 7-11, 2020IPv6 Network Architecture Programmable NetworksDuplicate Address Detection (DAD) is an essential part of the Neighbor Discovery Protocol (NDP), which determines whether the IPv6 address of a node conflicts with those of other nodes. Due to the lack of verification of NDP messages, DAD is vulnerable to DoS attacks. Existing solutions suffer from high complexity, need to modify the NDP, or have a single point of failure. To solve the above problems, we propose P4DAD, a secure DAD mechanism described by P4. By creating and maintaining binding entries between IPv6 address and link-layer property of host, P4DAD can filter spoofed NDP messages in an in-network manner to prevent DoS attacks on DAD without modifications to the NDP or host stack. We implement a prototype of P4DAD and evaluate it in terms of functionality, performance, and scalability. Evaluation results show that P4DAD can prevent DoS attacks on DAD successfully with negligible overhead, and has satisfactory scalability.
@inproceedings{kuang2020p4dad, title = {P4DAD: Securing Duplicate Address Detection Using P4}, author = {Kuang, Peng and Liu, Ying and He, Lin}, booktitle = {Proceedings of the 2020 IEEE International Conference on Communications (ICC 2020)}, year = {2020}, pages = {1-7}, doi = {10.1109/ICC40277.2020.9149310}, address = {Virtual}, date = {June 7-11}, }
2019
- INFOCOM
 Bootstrapping Accountability and Privacy to IPv6 Internet without Starting from ScratchLin He, Gang Ren, Ying LiuIn Proceedings of the 38th IEEE Conference on Computer Communications (INFOCOM 2019)
Bootstrapping Accountability and Privacy to IPv6 Internet without Starting from ScratchLin He, Gang Ren, Ying LiuIn Proceedings of the 38th IEEE Conference on Computer Communications (INFOCOM 2019)
Paris, France, April 29 - May 2, 2019IPv6 Network Architecture Protocol DesignAccountability and privacy are considered valuable but conflicting properties in the Internet, which at present does not provide native support for either. Past efforts to balance accountability and privacy in the Internet have unsatisfactory deployability due to the introduction of new communication identifiers, and because of large-scale modifications to fully deployed infrastructures and protocols. The IPv6 is being deployed around the world and this trend will accelerate. In this paper, we propose a private and accountable proposal based on IPv6 called PAVI that seeks to bootstrap accountability and privacy to the IPv6 Internet without introducing new communication identifiers and large-scale modifications to the deployed base. A dedicated quantitative analysis shows that the proposed PAVI achieves satisfactory levels of accountability and privacy. The results of evaluation of a PAVI prototype show that it incurs little performance overhead, and is widely deployable.
@inproceedings{he2019bootstrapping, title = {Bootstrapping Accountability and Privacy to IPv6 Internet without Starting from Scratch}, author = {He, Lin and Ren, Gang and Liu, Ying}, booktitle = {Proceedings of the 38th IEEE Conference on Computer Communications (INFOCOM 2019)}, year = {2019}, pages = {1486-1494}, doi = {10.1109/INFOCOM.2019.8737453}, address = {Paris, France}, date = {April 29 - May 2}, } - NAACL
 Relation Extraction with Temporal Reasoning Based on Memory Augmented Distant SupervisionJianhao Yan, Lin He, Ruqin Huang, Jian Li, Ying LiuIn Proceedings of the 2019 Conference of the North American Chapter of the Association for Computational Linguistics: Human Language Technologies (NAACL 2019)
Relation Extraction with Temporal Reasoning Based on Memory Augmented Distant SupervisionJianhao Yan, Lin He, Ruqin Huang, Jian Li, Ying LiuIn Proceedings of the 2019 Conference of the North American Chapter of the Association for Computational Linguistics: Human Language Technologies (NAACL 2019)
Minneapolis, USA, June 2-7, 2019Distant supervision (DS) is an important paradigm for automatically extracting relations. It utilizes existing knowledge base to collect examples for the relation we intend to extract, and then uses these examples to automatically generate the training data. However, the examples collected can be very noisy, and pose significant challenge for obtaining high quality labels. Previous work has made remarkable progress in predicting the relation from distant supervision, but typically ignores the temporal relations among those supervising instances. This paper formulates the problem of relation extraction with temporal reasoning and proposes a solution to predict whether two given entities participate in a relation at a given time spot. For this purpose, we construct a dataset called WIKI-TIME which additionally includes the valid period of a certain relation of two entities in the knowledge base. We propose a novel neural model to incorporate both the temporal information encoding and sequential reasoning. The experimental results show that, compared with the best of existing models, our model achieves better performance in both WIKI-TIME dataset and the well-studied NYT-10 dataset.
@inproceedings{yan2019relation, title = {Relation Extraction with Temporal Reasoning Based on Memory Augmented Distant Supervision}, author = {Yan, Jianhao and He, Lin and Huang, Ruqin and Li, Jian and Liu, Ying}, booktitle = {Proceedings of the 2019 Conference of the North American Chapter of the Association for Computational Linguistics: Human Language Technologies (NAACL 2019)}, year = {2019}, address = {Minneapolis, USA}, publisher = {Association for Computational Linguistics}, url = {https://aclanthology.org/N19-1107}, doi = {10.18653/v1/N19-1107}, pages = {1019--1030}, date = {June 2-7}, } - ACML
 Multi-modal Representation Learning for Successive POI RecommendationLishan Li, Ying Liu, Jianping Wu, Lin He, Gang RenIn Proceedings of the 11th Asian Conference on Machine Learning (ACML 2019)
Multi-modal Representation Learning for Successive POI RecommendationLishan Li, Ying Liu, Jianping Wu, Lin He, Gang RenIn Proceedings of the 11th Asian Conference on Machine Learning (ACML 2019)
Nagoya, Japan, November 17-19, 2019Successive POI recommendation is a fundamental problem for location-based social networks (LBSNs). POI recommendation takes a variety of POI context information (e.g. spatial location and textual comment) and user preference into consideration. Existing POI recommendation systems mainly focus on part of the POI context and user preference with a specific modeling, which loses valuable information from other aspects. In this paper, we propose to construct a multi-modal check-in graph, a heterogeneous graph that combines five check-in aspects in a unified way. We further propose a multi-modal representation learning model based on the graph to jointly learn POI and user representations. Finally, we employ an attentional recurrent neural network based on the representations for successive POI recommendation. Experiments on a public dataset studies the effects of modeling different aspects of check-in records and demonstrates the effectiveness of the method in improving POI recommendation performance.
@inproceedings{li2019multi, title = {Multi-modal Representation Learning for Successive POI Recommendation}, author = {Li, Lishan and Liu, Ying and Wu, Jianping and He, Lin and Ren, Gang}, booktitle = {Proceedings of the 11th Asian Conference on Machine Learning (ACML 2019)}, pages = {441--456}, year = {2019}, volume = {101}, publisher = {PMLR}, address = {Nagoya, Japan}, date = {November 17-19}, }
2017
- IPCCC
 Revisiting inter-AS IP Spoofing Let the Protection Drive Source Address ValidationYihao Jia, Ying Liu, Gang Ren, Lin HeIn Proceedings of the 36th IEEE International Performance Computing and Communications Conference (IPCCC 2017)
Revisiting inter-AS IP Spoofing Let the Protection Drive Source Address ValidationYihao Jia, Ying Liu, Gang Ren, Lin HeIn Proceedings of the 36th IEEE International Performance Computing and Communications Conference (IPCCC 2017)
San Diego, California, USA, December 10-12, 2017Network ArchitectureIP spoofing, which is prevalently used for anonymity and reflection attacks, has shown increasing destructive power in recent years. Although certain source address validation solutions have been standardized by the Internet Engineering Task Force, few networks are willing to adopt them in view of the deficiency of deployment benefits. Actually, all the source address validation solutions face the problem of a lack of deployability. In this paper, we summarize the key points describing deployability and propose a new security service-inter-autonomous-system (AS) Source Address Protection (iSAP). Technically, by increasing the possibility of keeping the source address belonging to one AS from being the victim of reflection flooding, iSAP improves the deployers ability to prevent IP spoofing and increases incremental deployability. In reality, such a service can also be regarded as a new profit opportunity for ASes and it could progress gradually once it is well commercialized. Based on simulations with real Internet topology data, the results illustrate that iSAP can protect ASes from being reflected with only a few deployers, exhibiting a high potential to mitigate reflection flooding with modest resource consumption.
@inproceedings{jia2017revisiting, title = {Revisiting inter-AS IP Spoofing Let the Protection Drive Source Address Validation}, author = {Jia, Yihao and Liu, Ying and Ren, Gang and He, Lin}, booktitle = {Proceedings of the 36th IEEE International Performance Computing and Communications Conference (IPCCC 2017)}, year = {2017}, pages = {1-10}, doi = {10.1109/PCCC.2017.8280451}, address = {San Diego, California, USA}, date = {December 10-12}, }
Journal & Magazine papers
2026
- AddrProbe: An Internet-wide Active IPv6 Address Probing System with Limited SeedsDaguo Cheng, Lin He#, Qilei Yin, Guangxing Han, Yizhen Zhang, Boran Jin, Ying Liu, Guanglei Song, Jinlong E, Tiankai Yang, Jiahai YangIEEE Transactions on Networking, 2026IPv6 Internet Measurement
With the large-scale deployment of IPv6, it is becoming more and more important to probe active IPv6 addresses on the global Internet. However, the vast address space and the random distribution of active addresses make the probing process full of challenges, especially for the probing of IPv6 prefixes without seed addresses. Furthermore, the widespread existence of IPv6 aliased prefixes also causes significant trouble for probing. In this paper, we present AddrProbe, an active IPv6 address probing system, which dynamically probes all global routing prefixes based on learned fine-grained address patterns from limited seed addresses and quickly detects aliased prefixes during probing. The evaluation results show that AddrProbe achieves a hit rate of 23%-45% with all routing prefixes announced by the BGP system, which is 6.6-13× that of current state-of-the-art approaches (no more than 4%). Moreover, we find 1.2×10^33 aliased addresses characterized by the detected aliased prefixes, covering 6,412 routing prefixes, which is a 10^7× and 5.9× improvement over existing methods, respectively. Finally, an IPv6 Hitlist is constructed based on the long-term probing results, which contains 562M addresses covering 190K routing prefixes and 29K ASes. These widely distributed addresses are meaningful for analyzing IPv6 address assignments and some other IPv6 measurement activities.
@article{cheng2026addrprobe, title = {AddrProbe: An Internet-wide Active IPv6 Address Probing System with Limited Seeds}, author = {Cheng, Daguo and He, Lin and Yin, Qilei and Han, Guangxing and and Zhang, Yizhen and Jin, Boran and Liu, Ying and Song, Guanglei and E, Jinlong and Yang, Tiankai and Yang, Jiahai}, journal = {IEEE Transactions on Networking}, year = {2026}, volume = {34}, number = {}, pages = {2498-2513}, publisher = {IEEE}, doi = {10.1109/TON.2025.3645923}, } - SwitchTAD: Defending Deep Learning-Based Website Fingerprinting Attacks with Programmable SwitchesComputer Networks, 2026Programmable Networks Security
Traffic analysis poses a serious threat to the privacy of users, particularly through website fingerprinting attacks. To mitigate these attacks, existing defense methods typically modify traffic patterns by configuring defense at the endpoint. However, these defense methods degrade user experience due to complex configurations and tight client-server cooperation. Furthermore, their static and coarse-grained defense rules are unable to adjust the perturbation decision flexibly at a fine-grained level according to the dynamic changes in individual packet sequences. These limitations greatly affect the effectiveness of defense. To this end, we propose SwitchTAD, a website fingerprinting defense system based on programmable switches. SwitchTAD offers a general and effective solution that protects all users behind the switch without requiring individual configurations. It also leverages the programmability of switches to process packets at a fine granularity, enabling the application of different defense policies tailored to the characteristics of each traffic flow. Specifically, we design a data plane friendly Recurrent Neural Network (RNN) architecture for generating defense policies without the intervention of the control plane. As packets arrive, the data plane uses the output of the RNN to determine whether to add dummy packets on a per-packet basis, ensuring robust defense while minimizing overhead. Experimental results show that SwitchTAD significantly reduces the accuracy of state-of-the-art website fingerprinting attacks while maintaining overall high performances.
@article{zhou2025switchtad, title = {SwitchTAD: Defending Deep Learning-Based Website Fingerprinting Attacks with Programmable Switches}, author = {Zhou, Jiasheng and He, Lin and Shi, Xiaoyi and Yang, Yifan and E, Jinlong and Liu, Ying}, journal = {Computer Networks}, year = {2026}, volume = {275}, pages = {111921}, issn = {1389-1286}, publisher = {Elsevier}, doi = {10.1016/j.comnet.2025.111921}, }
2024
- AddrMiner: A Fast, Efficient, and Comprehensive Global Active IPv6 Address Detection SystemGuanglei Song, Lin He#, Feiyu Zhu, Jinlei Lin, Wenjian Zhang, Lina Fan, Chenglong Li, Zhiliang Wang, Jiahai YangIEEE/ACM Transactions on Networking, 2024IPv6 Internet Measurement
Fast Internet-wide scanning is essential for network situational awareness and asset evaluation. However, the vast IPv6 address space makes brute-force scanning infeasible. Despite advancements in state-of-the-art methods, they do not work in seedless regions and suffer low detection efficiency and speed in regions with seed addresses. Moreover, the collected active address list (i.e., IPv6 hitlist) with low coverage cannot truly represent the active IPv6 address landscape of the Internet. This paper introduces AddrMiner, a fast, efficient, and comprehensive global active IPv6 address detection system. We design a systematic active IPv6 address detection strategy that divides the IPv6 space into two detection scenarios based on the presence or absence of seed addresses to discover active IPv6 addresses from scratch and from few to many. In the seedless regions, we present AddrMiner-N, leveraging a multi-level association policy to probe active addresses. It fills the gap of address detection in seedless regions and successfully discovers active addresses in 39,899 BGP prefixes without seed addresses, with a 1.03X higher hit rate, 30∼911X higher speed, and 2.7X broader coverage, compared to existing solutions. In the regions with seed addresses, our method AddrMiner-S dynamically generates target addresses using reinforcement learning. Compared to state-of-the-art methods, AddrMiner-S achieves an impressive 56.3% hit rate and a discovery speed of 839.0/s, which is 1.9∼2153X and 1.5∼755X of existing works, respectively. Finally, we deploy AddrMiner and discover 2.1B active IPv6 addresses, including 1.7B de-aliased active addresses and 0.4B aliased addresses, through continuous probing for three years.
@article{song2024addrminer, title = {AddrMiner: A Fast, Efficient, and Comprehensive Global Active IPv6 Address Detection System}, author = {Song, Guanglei and He, Lin and Zhu, Feiyu and Lin, Jinlei and Zhang, Wenjian and Fan, Lina and Li, Chenglong and Wang, Zhiliang and Yang, Jiahai}, journal = {IEEE/ACM Transactions on Networking}, year = {2024}, volume = {32}, number = {5}, pages = {3870-3887}, publisher = {IEEE}, doi = {10.1109/TNET.2024.3406508}, } - PMap: Reinforcement Learning-based Internet-wide Port ScanningGuanglei Song, Lin He, Tao Chen, Jinlei Lin, Linna Fan, Kun Wen, Zhiliang Wang, Jiahai YangIEEE/ACM Transactions on Networking, 2024Internet Measurement
Internet-wide scanning is a commonly used research technique in various network surveys, such as measuring service deployment and security vulnerabilities. However, these network surveys are limited to the given port set, not comprehensively obtaining the real network landscape, and even misleading survey conclusions. In this work, we introduce PMap, a port scanning tool that efficiently discovers the most open ports from all 65K ports in the whole network. PMapuses the correlation of ports to build an open port correlation graph of each network, using a reinforcement learning framework to update the correlation graph based on feedback results and dynamically adjust the order of port scanning. Compared to current port scanning methods, PMapperforms better on hit rate, coverage, and intrusiveness. Our experiments over real networks show that PMapcan find 90% open ports by only scanning 125 ports (90%@125) to each address, which is 99.3% less than the state-of-the-art port scanning methods. It reduces the number of scanned ports to decrease the intrusive nature of port scanning. In addition, PMapis highly parallel and lightweight. It scans 500 networks in parallel, achieving a port recommendation rate of up to 18 million per second, consuming only 7GB of memory. PMapis the first effective practice for scanning open ports using reinforcement learning. It bridges the gap of existing scanning tools and effectively supports subsequent service discovery and security research.
@article{song2024pmap, title = {PMap: Reinforcement Learning-based Internet-wide Port Scanning}, author = {Song, Guanglei and He, Lin and Chen, Tao and Lin, Jinlei and Fan, Linna and Wen, Kun and Wang, Zhiliang and Yang, Jiahai}, journal = {IEEE/ACM Transactions on Networking}, year = {2024}, volume = {32}, number = {6}, pages = {5524 - 5538}, publisher = {IEEE}, doi = {10.1109/TNET.2024.3491314}, } - WiseCam: A Systematic Approach to Intelligent Pan-Tilt Cameras for Moving Object TrackingJinlong E, Fangshuo Han, Lin He, Wei Xu, Zhenhua Li, Yunpeng Chai, Yunhao LiuIEEE Transactions on Mobile Computing, 2024Network Management
With the desired functionality of moving object tracking, wireless pan-tilt cameras are able to play critical roles in a growing diversity of surveillance environments. However, today’s pan-tilt cameras oftentimes underperform when tracking frequently moving objects like humans – they are prone to lose sight of objects and bring about excessive mechanical rotations that are especially detrimental to those energy-constrained outdoor scenarios. The ineffectiveness and high cost of all state-of-the-art tracking approaches are rooted in their adherence to the industry’s simplicity principle, which leads to their stateless nature, performing gimbal rotations based only on the latest object detection. To address the issues, we design and implement WiseCam that wisely tunes the pan-tilt cameras to minimize mechanical rotation costs while maintaining long-term object tracking. This systematic tracking approach also tackles issues of motion-rotation speed gap and scattered moving objects, which is universally applicable to complex tracking scenarios. We examine the performance of WiseCam by experiments on two types of pan-tilt cameras with different motors. Results show that it significantly outperforms the state-of-the-art tracking approaches on both tracking duration and power consumption.
@article{e2024wisecam, title = {WiseCam: A Systematic Approach to Intelligent Pan-Tilt Cameras for Moving Object Tracking}, author = {E, Jinlong and Han, Fangshuo and He, Lin and Xu, Wei and Li, Zhenhua and Chai, Yunpeng and Liu, Yunhao}, journal = {IEEE Transactions on Mobile Computing}, year = {2024}, volume = {23}, number = {12}, pages = {12330-12344}, publisher = {IEEE}, doi = {10.1109/TMC.2024.3410645}, }
2023
- AutoIoT: Automatically Updated IoT Device Identification with Semi-supervised LearningLinna Fan, Lin He#, Yichao Wu, Shize Zhang, Zhiliang Wang, Jia Li, Jiahai Yang, Chaocan Xiang, Xiaoqian MaIEEE Transactions on Mobile Computing, 2023Network Management
IoT devices bring great convenience to a person’s life and industrial production. However, their rapid proliferation also troubles device management and network security. Network administrators usually need to know how many IoT devices are in the network and whether they behave normally. IoT device identification is the first step to achieving these goals. Previous IoT device identification methods reach high accuracy in a closed environment. But they are not applicable in the continuously changing environment. When new types of devices are plugged in, they cannot update themselves automatically. Besides, they usually rely on supervised learning and need lots of labeled data, which is costly. To solve these problems, we propose a novel IoT device identification model named AutoIoT, updating itself automatically when new types of devices are plugged in. Besides, it only needs a few labeled data and identifies IoT devices with high accuracy. The evaluation on two public datasets shows that AutoIoT can identify new device types only using 1.5∼2.5 hours’ traffic and still have high accuracy after updating. Moreover, it has a better performance than other works when there are only a few labeled data, especially in an environment with scanning traffic.
@article{fan2023autoiot, title = {AutoIoT: Automatically Updated IoT Device Identification with Semi-supervised Learning}, author = {Fan, Linna and He, Lin and Wu, Yichao and Zhang, Shize and Wang, Zhiliang and Li, Jia and Yang, Jiahai and Xiang, Chaocan and Ma, Xiaoqian}, journal = {IEEE Transactions on Mobile Computing}, year = {2023}, volume = {22}, number = {10}, pages = {5769-5786}, publisher = {IEEE}, doi = {10.1109/TMC.2022.3183118}, } - SAV6: A Novel Inter-AS Source Address Validation Protocol for IPv6 InternetIEEE Network, 2023IPv6 Network Architecture
IP spoofing is prevalently used for anonymity and reflection attacks, e.g., distributed denial of service (DDoS) attacks, which have shown increasingly destructive power in recent years because today’s Internet lacks validation on source addresses. Moreover, the fast deployment of IPv6 on the Internet may further aggravate the damages of DDoS attacks. This paper proposes a novel source address validation mechanism called SAV6, which leverages the huge IPv6 address space to validate source addresses at an inter-autonomous system (AS) granularity. In SAV6, each IPv6 address contains an AS number (ASN), whose corresponding AS announces the prefix of the address to other ASes. An AS can determine the authenticity of the source address by whether the ASN in the address matches the corresponding prefix after receiving an incoming packet. The performance evaluation of a SAV6 prototype shows that it adds little performance overhead to the deployed infrastructures and is a lightweight and deployable protocol.
@article{he2023sav6, title = {SAV6: A Novel Inter-AS Source Address Validation Protocol for IPv6 Internet}, author = {He, Lin and Ren, Gang and Liu, Ying and Song, Guanglei and E, Jinlong and Yang, Jiahai and Xu, Mingwei}, journal = {IEEE Network}, year = {2023}, volume = {37}, number = {5}, pages = {64-70}, publisher = {IEEE}, doi = {10.1109/MNET.123.2200111}, } -
 Efficient Video Distribution Based on Collaboration of Heterogenous Computing Nodes基于异构算力节点协同的高效视频分发Jinlong E, Lin He#Journal of Computer Research and Development, 2023
Efficient Video Distribution Based on Collaboration of Heterogenous Computing Nodes基于异构算力节点协同的高效视频分发Jinlong E, Lin He#Journal of Computer Research and Development, 2023Computing power network connects computing nodes through the network to break the limitation of single point of computing power, and it is rapidly developed and applied in more and more business fields in recent years. The popular live video broadcasting relies on the transmission and transcoding of a large number of video frames, and it is of great practical importance to explore computing power networks for efficient video distribution. Compared with the traditional large-scale data processing, video applications have higher requirements for transmission delay and bandwidth guarantee. However, the computing power of nodes provided by each cloud service varies, and the state of network links between nodes often varies. Therefore, it is a great challenge to realize low latency and high bandwidth video distribution by selecting nodes with the best combined transmission and transcoding performance. Therefore, we design an efficient video distribution scheme based on heterogeneous computing nodes, including planning video transmission paths and reasonably selecting transcoding nodes through reinforcement learning, using priority queuing scheduling for different video distribution tasks and adaptively adjusting node resources to reduce resource bursty competition, adopting a layered-log-synchronization fault tolerance mechanism to quickly restore data consistency after node failures, and finally deploying multi-cloud service distributed nodes to realize a complete video distribution system. A large number of live ultra-high definition video experiments show that the performance of this scheme is significantly improved compared with existing video distribution methods.
@article{e2023efficient, title = {Efficient Video Distribution Based on Collaboration of Heterogenous Computing Nodes}, author = {E, Jinlong and He, Lin}, journal = {Journal of Computer Research and Development}, year = {2023}, volume = {60}, number = {4}, pages = {772-785}, doi = {10.7544/issn1000-1239.202330004}, chinesetitle = {基于异构算力节点协同的高效视频分发}, }
2022
- DET: Enabling Efficient Probing of IPv6 Active AddressesGuanglei Song, Jiahai Yang, Zhiliang Wang, Lin He#, Jinlei Lin, Long Pan, Chenxin Duan, Xiaowen QuanIEEE/ACM Transactions on Networking, 2022IPv6 Internet Measurement
Fast IPv4 scanning significantly improves network measurement and security research. Nevertheless, it is infeasible to perform brute-force scanning of the IPv6 address space. Alternatively, one can find active IPv6 addresses through scanning the candidate addresses generated by state-of-the-art algorithms. However, the probing efficiency of such algorithms is often very low. In this paper, our objective is to improve the probing efficiency of IPv6 addresses. We first perform a longitudinal active measurement study and build a high-quality dataset, hitlist, including more than 1.95,B IPv6 addresses distributed in 58.2,K BGP prefixes and collected over 17 months period. Different from the previous works, we probe the announced BGP prefixes using a pattern-based algorithm. This results in a dataset without uneven address distribution and low active rates. Further, we propose an efficient address generation algorithm, DET, which builds a density space tree to learn high-density address regions of the seed addresses with linear time complexity and improves the active addresses’ probing efficiency. We then compare our algorithm DET against state-of-the-art algorithms on the public hitlist and our hitlist by scanning 50,M addresses. Our analysis shows that DET increases the de-aliased active address ratio and active address (including aliased addresses) ratio by 10%, and 14%, respectively. Furthermore, we develop a fingerprint-based method to detect aliased prefixes. The proposed method for the first time directly verifies whether the prefix is aliased or not. Our method finds that 10.64% of the public aliased prefixes are false positive.
@article{song2022det, title = {DET: Enabling Efficient Probing of IPv6 Active Addresses}, author = {Song, Guanglei and Yang, Jiahai and Wang, Zhiliang and He, Lin and Lin, Jinlei and Pan, Long and Duan, Chenxin and Quan, Xiaowen}, journal = {IEEE/ACM Transactions on Networking}, year = {2022}, volume = {30}, number = {4}, pages = {1629-1643}, doi = {10.1109/TNET.2022.3145040}, } - TurboNet: Faithfully Emulating Networks with Programmable SwitchesJiamin Cao, Ying Liu, Yu Zhou, Lin He#, Mingwei XuIEEE/ACM Transactions on Networking, 2022Programmable Networks
Faithfully emulating networks is critical for verifying the correctness and effectiveness of new networking-related designs. Existing network experiment platforms either cannot faithfully emulate the functionality and performance of production networks or cannot scale well due to cost constraints. In this paper, we propose TurboNet, a new network emulator that utilizes one or more programmable switches to achieve faithful emulation of the network data plane and control plane. For data plane emulation, we propose a series of key designs, such as port mapper, queue mapper, and delayed queue, to emulate network topologies and performance metrics with high flexibility and accuracy. For control plane emulation, we support static routing configurations, distributed routing agents, and the centralized routing controllers. Meanwhile, we provide APIs for operators to simplify network emulation tasks. We implement TurboNet on Tofino switches. Evaluation results show that: (1) On the data plane, TurboNet can flexibly emulate various topologies, such as an 8-ary fat-tree with only one programmable switch and a 10-ary fat-tree with four programmable switches; (2) On the control plane, TurboNet supports about 200 BGP agents on a single programmable switch with a CPU usage of 25%; (3) TurboNet can accurately emulate different network performance metrics such as 10⁻⁸ link loss, and microsecond to millisecond link delay.
@article{cao2022turbonet, title = {TurboNet: Faithfully Emulating Networks with Programmable Switches}, author = {Cao, Jiamin and Liu, Ying and Zhou, Yu and He, Lin and Xu, Mingwei}, journal = {IEEE/ACM Transactions on Networking}, year = {2022}, volume = {30}, number = {3}, pages = {1395-1409}, doi = {10.1109/TNET.2022.3142126}, } - CoFilter: High-Performance Switch-Accelerated Stateful Packet Filter for Bare-Metal ServersIEEE Transactions on Parallel and Distributed Systems, 2022Programmable Networks
As one of the most critical cloud services, Bare-Metal Servers (BMS) introduce stringent performance requirements on data center networks (DCN). Stateful packet filter is an integral DCN component of ensuring connection security for BMS. However, the off-the-shelf stateful packet filters either are costly for cloud DCNs or introduce significant performance bottlenecks. In this article, we present CoFilter , which leverages low-cost programmable switches to accelerate the stateful packet filter for BMS. CoFilter uses (1) stateful process partition to enable complex stateful packet filtering logic on programmability-limited switching ASICs, (2) state compression to track tens of millions of connections with constrained hardware memory, and (3) per-tenant packet rate limit and tenant-aware flow migration to achieve efficient performance isolation among different tenants. Overall, CoFilter implements a high-performance stateful packet filter via the co-design of programmable switching ASIC and CPU. We evaluate CoFilter under various data center traffic traces with real-world flow distributions. The evaluation results show that CoFilter remarkably outperforms NetFilter, i.e., forwarding packets at line rate (13x throughput of NetFilter), keeping packet delay within 1us, and freeing a significant quantity of CPU cores, with rather small memory usage, i.e., accommodating over 107 connections with only 16MB SRAM.
@article{cao2021cofilter, title = {CoFilter: High-Performance Switch-Accelerated Stateful Packet Filter for Bare-Metal Servers}, author = {Cao, Jiamin and Liu, Ying and Zhou, Yu and He, Lin and Sun, Chen and Wang, Yangyang and Xu, Mingwei}, journal = {IEEE Transactions on Parallel and Distributed Systems}, year = {2022}, volume = {33}, number = {9}, pages = {2249-2262}, doi = {10.1109/TPDS.2021.3136575}, } - EvoIoT: An Evolutionary IoT and Non-IoT Classification Model in Open EnvironmentsComputer Networks, 2022Network Management
IoT device identification is essential for both device asset management and security management. IoT device identification in open environments is the key to its application in real environments, where IoT and non-IoT device identification is the first and critical step. However, existing methods are either not applicable to open environments or have poor scalability and sustainability for IoT and non-IoT device identification. This paper presents EvoIoT, an IoT and non-IoT identification model designed to apply in open environments with high scalability and the ability to run sustainably and effectively. EvoIoT achieves high scalability by applying a unified model for all devices. To mine discriminative features from encrypted traffic, EvoIoT extracts original features from packet headers and judges feature importance in the entire model update process. For sustainability, EvoIoT proposes a representative device choosing method and model update method to address the concept drift caused by new types of devices. EvoIoT is the first high-performance model that systematically addresses the IoT and non-IoT device classification problem. We evaluate EvoIoT on two public datasets and a private dataset collected from a laboratory setting. The evaluation results show that EvoIoT is on average 6.27% 48.89% more accurate than state-of-the-art methods.
@article{fan2022evoiot, title = {EvoIoT: An Evolutionary IoT and Non-IoT Classification Model in Open Environments}, author = {Fan, Linna and He, Lin and Dong, Enhuan and Yang, Jiahai and Li, Chenglong and Lin, Jinlei and Wang, Zhiliang}, journal = {Computer Networks}, year = {2022}, volume = {219}, pages = {109450}, publisher = {Elsevier}, doi = {10.1016/j.comnet.2022.109450}, } - Enabling Application-aware Traffic Engineering in IPv6 NetworksLin He, Shicheng Wang, Yichi Xu, Peng Kuang, Jiamin Cao, Ying Liu, Xing Li, Shuping PengIEEE Network, 2022IPv6 Network Management
The Internet hosts numerous applications with different requirements for network delay, bandwidth, jitter, packet loss, and so on. However, in the TCP/IP network architecture, the network and application layers are decoupled, which means that the network does not have a fine-grained understanding of the application requirements. Therefore, it is not easy to provide truly fine-grained traffic operations for applications and guarantee their corresponding service level agreement requirements. In this article, we propose ATE6, which is an application-aware traffic engineering (TE) framework. For the control plane, we define a request language that can be used by applications to express their requirements, which allows networks to associate IPv6 addresses with the communication requirements of applications. We also devise an efficient path selection algorithm that allows the network operator to deploy an optimal TE path for an application. For the data plane, ATE6 uses segment routing over the IPv6 data plane to enforce and control network paths based on network policies. We implemented a prototype, and evaluation results show that ATE6 is a flexible, privacy-preserving, lightweight, and cost-efficient application-aware TE framework.
@article{he2022enabling, title = {Enabling Application-aware Traffic Engineering in IPv6 Networks}, author = {He, Lin and Wang, Shicheng and Xu, Yichi and Kuang, Peng and Cao, Jiamin and Liu, Ying and Li, Xing and Peng, Shuping}, journal = {IEEE Network}, year = {2022}, volume = {36}, number = {2}, pages = {42-49}, publisher = {IEEE}, doi = {10.1109/MNET.005.2100440}, }
2021
- PAVI: Bootstrapping Accountability and Privacy to IPv6 InternetLin He, Gang Ren, Ying Liu, Jiahai YangIEEE/ACM Transactions on Networking, 2021IPv6 Network Architecture Protocol Design
Accountability and privacy are considered valuable but conflicting properties in the Internet, which at present does not provide native support for either. Past efforts to balance accountability and privacy in the Internet have unsatisfactory deployability due to the introduction of new communication identifiers, and because of large-scale modifications to fully deployed infrastructures and protocols. The IPv6 is being deployed around the world and this trend will accelerate. In this paper, we propose a private and accountable proposal based on IPv6 called PAVI that seeks to bootstrap accountability and privacy to the IPv6 Internet without introducing new communication identifiers and large-scale modifications to the deployed base. A dedicated quantitative analysis shows that the proposed PAVI achieves satisfactory levels of accountability and privacy. The results of the evaluation of a PAVI prototype show that it incurs little performance overhead, and is widely deployable.
@article{he2021pavi, title = {PAVI: Bootstrapping Accountability and Privacy to IPv6 Internet}, author = {He, Lin and Ren, Gang and Liu, Ying and Yang, Jiahai}, journal = {IEEE/ACM Transactions on Networking}, year = {2021}, volume = {29}, number = {2}, pages = {695-708}, doi = {10.1109/TNET.2020.3047667}, } - Towards Securing Duplicate Address Detection using P4Lin He, Peng Kuang, Ying Liu, Gang Ren, Jiahai YangComputer Networks, 2021IPv6 Network Architecture Programmable Networks
Duplicate Address Detection (DAD) is one of the functions of the Neighbor Discovery Protocol (NDP), which determines whether the IPv6 address of a node conflicts with those of other nodes. However, due to the lack of verification of NDP messages, DAD is vulnerable to Denial of Service (DoS) attacks. Existing solutions suffer from high complexity and low security, need to modify the NDP, or have a single point of failure, which renders them infeasible to be deployed. To solve the above problems, we propose P4DAD, which is a secure DAD mechanism based on P4. By creating and maintaining a binding entry between an IPv6 address and a link-layer property of a host’s network attachment, P4DAD can filter spoofed NDP messages in an in-network manner to prevent DoS attacks on DAD without modification to the NDP or host stack. We implement a prototype of P4DAD and evaluate it in terms of functionality, performance, and scalability. Evaluation results show that P4DAD can prevent DoS attacks on DAD successfully with negligible overhead and has satisfactory scalability.
@article{he2021towards, author = {He, Lin and Kuang, Peng and Liu, Ying and Ren, Gang and Yang, Jiahai}, title = {Towards Securing Duplicate Address Detection using {P4}}, journal = {Computer Networks}, volume = {198}, pages = {108323}, year = {2021}, url = {https://doi.org/10.1016/j.comnet.2021.108323}, doi = {10.1016/j.comnet.2021.108323}, }
2018
- GAGMS: A Requirement-driven General Address Generation and Management SystemYing Liu, Lin He, Gang RenScience China Information Sciences, 2018IPv6 Network Architecture
IPv6 address generation is closely related to the manageability, security, privacy protection, and traceability of the Internet. There are many kinds of IPv6 address generation and configuration methods in the area of Internet standards and research that may cause certain problems, including the mixed operation problem of multiple IPv6 address generation schemes, the synchronization problem of the change in IPv6 address, the efficiency problem of processing large-scale concurrent IPv6 address requests, and the general model problem for mapping IPv6 addresses to other requirement spaces as identifiers. In this paper, we consider generating and managing IPv6 addresses according to network requirements. After conducting a requirement analysis of most proposed address generation schemes, we propose a general address generation model and a general address management system, which are the cores of the general address generation and management system (GAGMS). This system solves the above problems under the premise of maintaining the diversity and flexibility of the existing IPv6 address generation and configuration methods and allows networks to utilize different address generation schemes according to different requirements in different scenarios. Finally, we design a prototype system and evaluate our GAGMS to demonstrate its effectiveness, manageability, and scalability, and we have conducted trial deployment in campus networks and are trying to standardize this work in IETF.
@article{liu2018gagms, author = {Liu, Ying and He, Lin and Ren, Gang}, title = {GAGMS: A Requirement-driven General Address Generation and Management System}, journal = {Science China Information Sciences}, volume = {61}, number = {9}, pages = {092109:1--092109:15}, year = {2018}, url = {https://doi.org/10.1007/s11432-017-9298-3}, } - IEEE Access
 Network-Layer Accountability Protocols: A SurveyLin He, Ying Liu, Gang RenIEEE Access, 2018Network Architecture
Network-Layer Accountability Protocols: A SurveyLin He, Ying Liu, Gang RenIEEE Access, 2018Network ArchitectureToday’s Internet is vulnerable to numerous attacks, including source spoofing, distributed denial of service, prefix hijacking, and route forgery. Network-layer accountability is considered as an effective deterrence tool which can be used to address these attacks. Much research has been devoted to improving network-layer accountability of today’s Internet. In this paper, we first investigate the state-of-the-art network-layer accountability research and summarize a general definition of network-layer accountability. Next, we propose a network-layer accountability framework and present a taxonomy of network-layer accountability protocols according to accountability granularity. Furthermore, we compare these protocols and discuss their pros and cons mainly from accountability function, deployability, and security. Finally, some open research questions are emphasized for directing future designs.
@article{he2018network, title = {Network-Layer Accountability Protocols: A Survey}, author = {He, Lin and Liu, Ying and Ren, Gang}, journal = {IEEE Access}, year = {2018}, volume = {6}, number = {}, pages = {66886-66902}, doi = {10.1109/ACCESS.2018.2879489}, } -
 RISP: An RPKI-based inter-AS Source Protection MechanismYihao Jia, Ying Liu, Gang Ren, Lin HeTsinghua Science and Technology, 2018Network Architecture
RISP: An RPKI-based inter-AS Source Protection MechanismYihao Jia, Ying Liu, Gang Ren, Lin HeTsinghua Science and Technology, 2018Network ArchitectureIP source address spoofing is regarded as one of the most prevalent components when launching an anonymous invasion, especially a Distributed Denial-of-Service (DDoS) attack. Although Source Address Validations (SAVs) at the access network level are standardized by the Internet Engineering Task Force (IETF), SAV at the inter-Autonomous System (AS) level still remains an important issue. To prevent routing hijacking, the IETF is constructing a Resource Public Key Infrastructure (RPKI) as a united trust anchor to secure interdomain routing. In this study, we creatively use the RPKI to support inter-AS SAV and propose an RPKI-based Inter-AS Source Protection (RISP) mechanism. According to the trust basis provided by the RPKI, RISP offers ASes a more credible source-oriented protection for the IP addresses they own and remains independent of the RPKI. Based on the experiments with real Internet topology, RISP not only provides better incentives, but also improves efficacy and economizes bandwidth with a modest resource consumption.
@article{jia2018risp, author = {Jia, Yihao and Liu, Ying and Ren, Gang and He, Lin}, journal = {Tsinghua Science and Technology}, title = {RISP: An RPKI-based inter-AS Source Protection Mechanism}, year = {2018}, volume = {23}, number = {1}, pages = {1-12}, doi = {10.26599/TST.2018.9010025}, }
2015
- Building an IPv6 Address Generation and Traceback System with NIDTGA in Address Driven NetworkYing Liu, Gang Ren, Jianping Wu, Shenglin Zhang, Lin He, Yihao JiaScience China Information Sciences, 2015IPv6 Network Architecture
In the design and construction process of Next Generation Internet, it is important to identify the source of each IP packet forwarding accurately, especially for the support of precise fine-grained management, control, traceability and improving the trustworthiness of the Internet. This paper designed a scalable Network Identity (NID) scheme for the Internet users, proposed NIDTGA (Network Identity and Time Generated Address), an IPv6 address generation algorithm embedded NID and time information, then designed and implemented an IPv6 address generation and traceback system based on NIDTGA. The design of NIDTGA, which reflects the length, time and owner attributes of the IP address, can be a good support to ADN (Address Driven Network). At the same time, by embedding the key elements of user identity and time in the IPv6 address, and by taking into account both the traceability and privacy, NIDTGA can provide a technical basis for the establishment of the network trust mechanism, and achieve the traceability of security event.
@article{liu2015building, author = {Liu, Ying and Ren, Gang and Wu, Jianping and Zhang, Shenglin and He, Lin and Jia, Yihao}, title = {Building an IPv6 Address Generation and Traceback System with NIDTGA in Address Driven Network}, journal = {Science China Information Sciences}, volume = {58}, number = {12}, pages = {1--14}, year = {2015}, url = {https://doi.org/10.1007/s11432-015-5461-0}, doi = {10.1007/s11432-015-5461-0}, }
Posters & Demos
2025
- IMC
 Poster: TopoHunter: Enabling Efficient and High-Coverage Active IPv6 Topology DiscoveryWenwen Gong, Lin He#, Hongwei Li, Guanglei Song, Wentong Wang, Daguo Cheng, Enhuan Dong, Chenglong Li, Hui Zhang, Zhiliang Wang, Jinlong E, Ying Liu, Jiahai YangIn Proceedings of the 2025 ACM on Internet Measurement Conference (IMC 2025)
Poster: TopoHunter: Enabling Efficient and High-Coverage Active IPv6 Topology DiscoveryWenwen Gong, Lin He#, Hongwei Li, Guanglei Song, Wentong Wang, Daguo Cheng, Enhuan Dong, Chenglong Li, Hui Zhang, Zhiliang Wang, Jinlong E, Ying Liu, Jiahai YangIn Proceedings of the 2025 ACM on Internet Measurement Conference (IMC 2025)
Madison, Wisconsin, USA, October 28–31, 2025IPv6 Internet MeasurementThe rapid expansion of the IPv6 Internet highlights the critical need for advanced topology mapping to enhance network management and security. However, the large address space and stringent ICMP rate limiting pose significant challenges for IPv6 topology discovery. To this end, we introduce TopoHunter, an efficient IPv6 Internet topology discovery system. The central concept of TopoHunter is to allocate more probing resources to target prefix spaces that yield greater topological benefits, as well as to their surrounding areas. To achieve this, we design a feedback-based target generation module comprised of a Target Prefix Probing Value Forest that maintains the estimated probing values of hierarchical target prefix spaces. This approach efficiently addresses the inefficiencies of existing probing methods by reducing redundancy and maximizing topological gains from each vantage point. Our system has successfully discovered the most extensive and complete IPv6 topology map to date, comprising over 144 million router interfaces and 251 million edges, covering 72.83% of autonomous systems and 43.36% of routing prefixes announced by the BGP system.
@inproceedings{zhang2025rgen, title = {Poster: TopoHunter: Enabling Efficient and High-Coverage Active IPv6 Topology Discovery}, author = {Gong, Wenwen and He, Lin and Li, Hongwei and Song, Guanglei and Wang, Wentong and Cheng, Daguo and Dong, Enhuan and Li, Chenglong and Zhang, Hui and Wang, Zhiliang and E, Jinlong and Liu, Ying and Yang, Jiahai}, booktitle = {Proceedings of the 2025 ACM on Internet Measurement Conference (IMC 2025)}, year = {2025}, pages = {1052–1053}, doi = {10.1145/3730567.3768591}, address = {Madison, Wisconsin, USA}, date = {October 28–31}, } - IWQoS
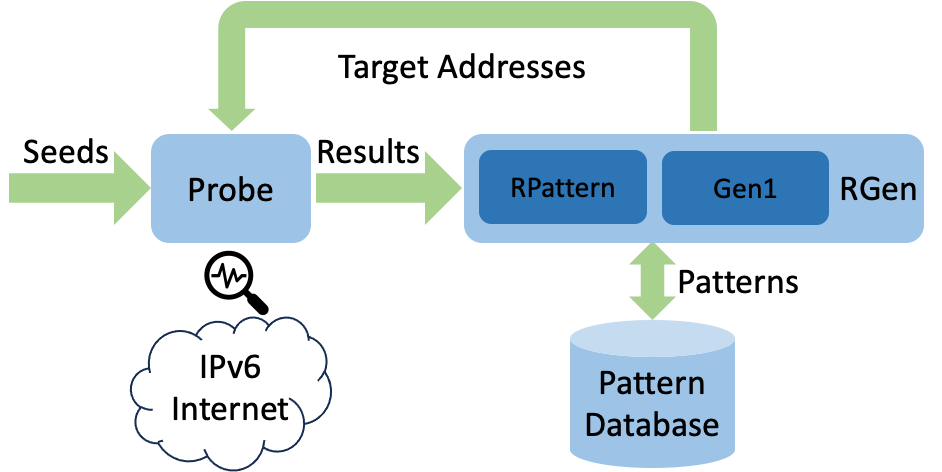 RGen: A Real-Time Pattern Mining Approach to Target Generation for Internet-wide IPv6 ScanningWei Zhang, Gang Ren, Xia Yin, Lin HeIn Proceedings of the 33rd IEEE/ACM International Symposium on Quality of Service (IWQoS 2025)
RGen: A Real-Time Pattern Mining Approach to Target Generation for Internet-wide IPv6 ScanningWei Zhang, Gang Ren, Xia Yin, Lin HeIn Proceedings of the 33rd IEEE/ACM International Symposium on Quality of Service (IWQoS 2025)
Gold Coast, Australia, July 2–4, 2025IPv6 Internet MeasurementTarget generation is a crucial step for efficient Internet-wide IPv6 scanning, yet existing techniques are hindered by limited pattern discovery and biased target distribution. We introduce RGen, a novel target generation algorithm employing real-time pattern mining and a stochastic generation strategy. RGen minimizes pattern loss, dynamically incorporates new addresses, and promotes balanced target distribution, overcoming prior limitations. Experiments show RGen achieves the highest overall hit rate (58%), surpassing the previous best (AddrMiner-S) by 60%, while simultaneously leading in network discovery, finding the most new BGP prefixes and new /64 prefixes.
@inproceedings{zhang2025rgeo, title = {RGen: A Real-Time Pattern Mining Approach to Target Generation for Internet-wide IPv6 Scanning}, author = {Zhang, Wei and Ren, Gang and Yin, Xia and He, Lin}, booktitle = {Proceedings of the 33rd IEEE/ACM International Symposium on Quality of Service (IWQoS 2025)}, year = {2025}, pages = {1-2}, doi = {10.1109/IWQoS65803.2025.11143325}, address = {Gold Coast, Australia}, date = {July 2–4}, }
Patents
2021
- US PatentDynamic IPv6 address detection method based on densityJiahai Yang, Guanglei Song, Lin He, Zhiliang Wang17192016, September 9, 2021
2020
- CN PatentInter-domain source address verification method and device, electronic equipment and storage mediumLin He, Ying Liu, Gang Ren, Jiahai YangZL202011406286.5, December 2, 2020
- CN Patent
- CN PatentAddress detection method and device, switch and storage mediumLin He, Ying Liu, Peng KuangZL202010245453.6, March 31, 2020
- CN PatentBlockchain-based NIDTGA user identity traceability systemYing Liu, Lin He, Zhitao LiZL202010987763.5, September 18, 2020
- CN PatentInter-domain source address verification method based on SRv6Ying Liu, Lin He, Jiamin Cao, Yihao JiaZL202010632607.7, July 2, 2020
- CN PatentIPv6 alias prefix detection method based on fragmentation fingerprintsJiahai Yang, Guanglei Song, Lin He, Zhiliang WangZL202011322303.7, November 23, 2020
- CN PatentDynamic IPv6 address detection method based on densityJiahai Yang, Guanglei Song, Lin He, Zhiliang WangZL202010157916.3, March 9, 2020
- CN PatentAccess subnet source address verification method and systemYing Liu, Shicheng Wang, Zhitao Li, Lin HeZL202011306063.1, November 19, 2020
2016
- CN PatentIPv6 address generation scheme management systemGang Ren, Ying Liu, Lin HeZL201610621792.3, August 1, 2016
2015
- CN PatentUser internet identity and generation method and system thereofGang Ren, Ying Liu, Jianping Wu, Shenglin Zhang, Yihao Jia, Lin HeZL201510373628.0, June 30, 2015